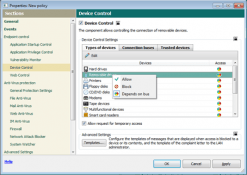
A soft approach to hardware usage
Applying corporate security policies to devices used by employees, especially mobile ones, is every bit as important as monitoring applications installed on the network or controlling Internet access. The larger … Continue reading A soft approach to hardware usage