It seems that there is now a typical scenario for malware evolution. First cybercriminals release a skeleton with basic functions — that piece of malware behaves quietly, showing almost no malicious activity. Usually it comes in sight of several anti-virus companies shortly after it’s release, but the researchers treat it like yet another piece of potentially malicious code: nothing of particular interest.
After some time the trojan (yes, it’s usually a trojan) gets additional functionallity and becomes capable of doing way more harm than the first version potentially could. During the third step, the massive attack campaign begins: thousands of devices get infected and then the trojan does it’s dirty job. The amount of damage dealt depends on the type of the trojan — it can turn out to be either ransomware asking for up to several hundred dollars, or a banking trojan stealing whatever it can get from your credit cards, spying tool on you, etc.
For example, this was the exact scenario for Asacub, which had first emerged as a rather simple phishing program and then turned into a banker with capabilities that of a heavy weapon. And now Acecard has followed a similar path. This malware seems to be even more serious bad news than Asacub.
Evolution of #Asacub trojan: from small fish to ultimate weapon – https://t.co/lLv0pY4lol #infosec #mobile #banking pic.twitter.com/gAM3zzy7aC
— Kaspersky (@kaspersky) January 20, 2016
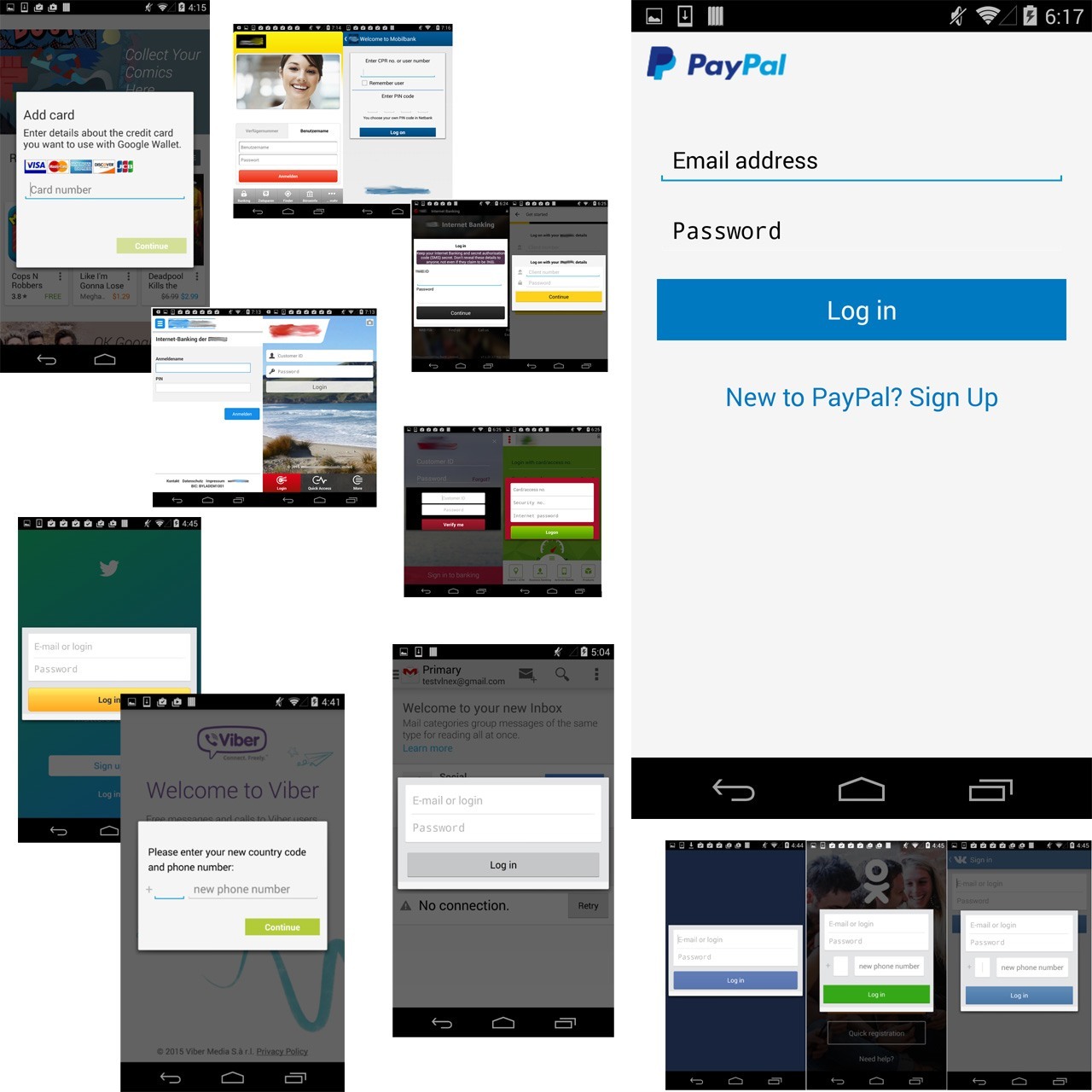
Acecard is an Android banking trojan family consisting of several modifications of the same trojan. As with most of banking trojans, it performs by overlaying mobile banking applications with it’s own phishing forms that the unsuspecting user would be eager to fill in with their credit card data. Once a user presses ‘Submit’ (or a similar action) — the data is stolen, and the malefactors either forward the money from the card to their phony accounts or sell the data to a third party.
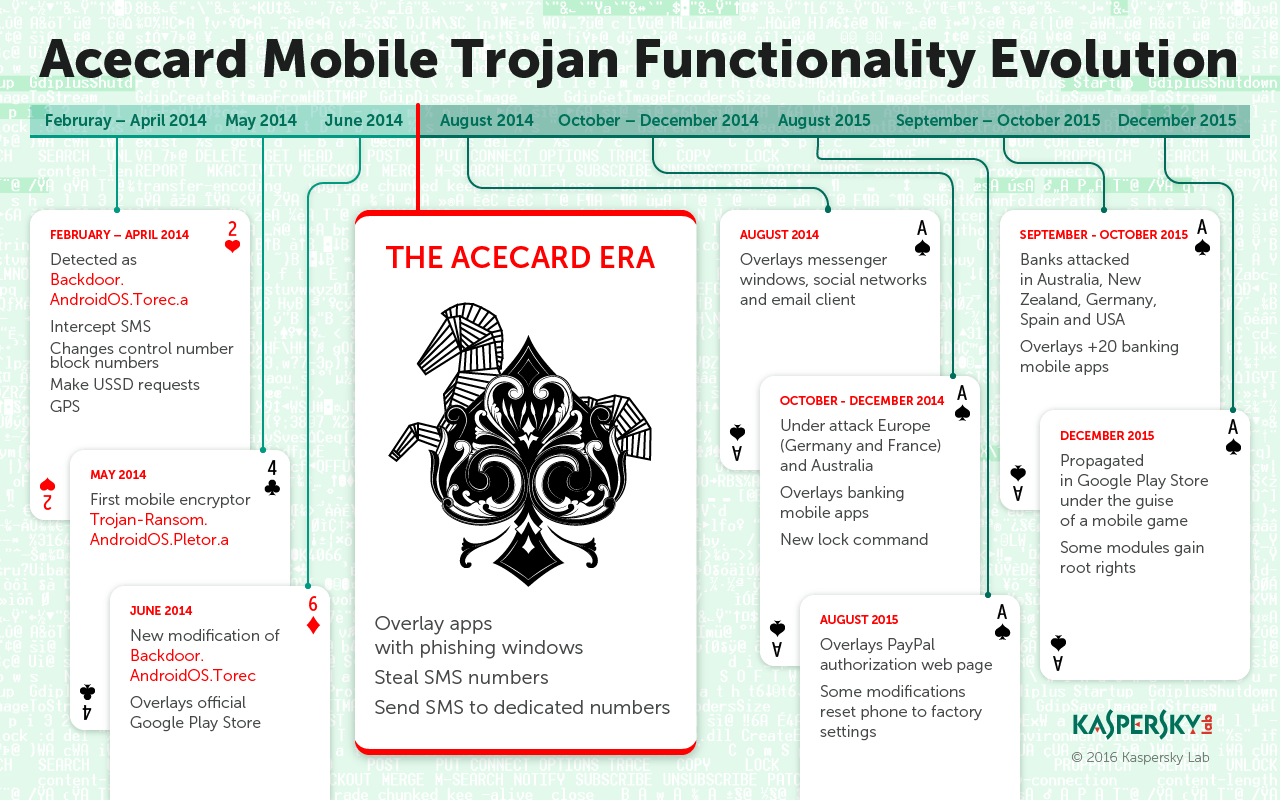
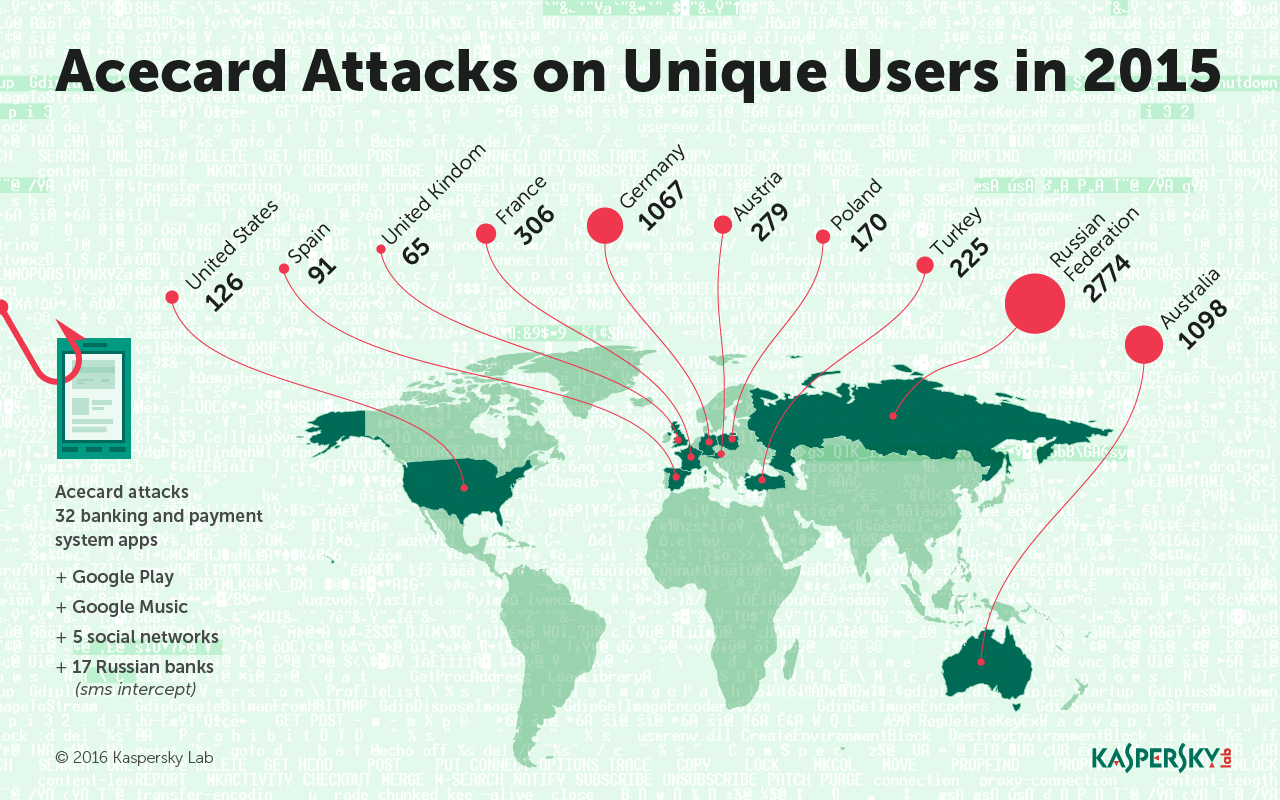
Acecard stands out from the crowd for two main reasons. First of all, common banking trojans are usually capable of overlaying no more than a few mobile banking apps, while Acecard is familiar with about 30 different banks and payment systems. Acecard can also receive a command from the command-and-control server to overlay ANY application, so the amount of attacked apps may be even higher.
~2M attempts to steal money via online access to bank accounts in 2015 #KLReport #banking https://t.co/dEGpO9RNV0 pic.twitter.com/igmson8TOb
— Kaspersky (@kaspersky) December 15, 2015
Second, it does not limit itself with only banking apps. Acecard can be also used for phishing in mobile social networking apps (Facebook, Twitter, Instagram), instant messengers (WhatsApp, Viber, Skype), and, more interestingly, the PayPal app and the Gmail client. It also is up to overlaying Google Play Store and Google Play Music with phishing windows.
Acecard is distributed not by the usual email spam but by disguising as something potentially useful; for example, pretending to be the Adobe Flash. Here we’d rather remind you that Flash for Android was discontinued back in 2012, so there is NO genuine Flash Player for Android nowadays. But that’s not the only distribution channel — our researchers have found a trojan that downloads Acecard in Google Play Store.
How to protect your money from online fraud – https://t.co/LRBlkaC1V0 #banking #onlineshopping #ecommerce pic.twitter.com/rqrqgXkDGK
— Kaspersky (@kaspersky) December 14, 2015
For the first time Acecard was detected in February 2014 — and back then, as we have mentioned before, it was showing no malicious activity. It took the cybercriminals about a year and a half to tune Acecard into real threat, adding new functions from one version to the next. Our experts have detected more then 10 different versions of this malware, each new build gaining more and more malicious abilities. The modern versions are so powerful, that Roman Unuchek, Senior Malware Analyst at Kaspersky Lab called Acecard ‘one of the most dangerous threats to users today’.
And then, in May 2015, the attacks began. During the time interval from May to September 2015 more than 6,000 users were attacked. Acecard is single-handedly responsible for a massive increase in the number of banking cyberattacks in Australia, it’s other victims primarily reside in Russia, Germany, Austria and France. Meanwhile, the cybercriminals behind Acecard most likely are Russian-speaking.
In order to protect yourself from Acecard and other’s of its kind, we suggest that you do the following:
- Pay attention to the apps you install. For example, Acecard doesn’t show anything but the Flash Player logo while running, but that’s the perfect time to recall that there is no Android Flash Player anymore.
- Don’t download applications from nonofficial stores and even if you are using an official store don’t download apps that you don’t trust and don’t really need. Hackers can bypass Google Play’s security and your new kitty wallpaper app can turn out to be infected.
- Use a good security solution. Kaspersky Internet Security for Android detects all known versions of Acecard and thus would serve as a good enough protection against Acecard as well as other malware families.
 Acecard
Acecard


 Tips
Tips