We’re witnessing a new malicious mass-mailing campaign aimed at company employees using Agent Tesla spyware attachments. This time, when creating their e-mail messages, the attackers pay special attention to detail — so that their messages can really be mistaken for regular business e-mails with attached documents. Their final goal is to trick the recipient into opening the attached archive to then execute the malicious file.
Why is this malicious mailing special?
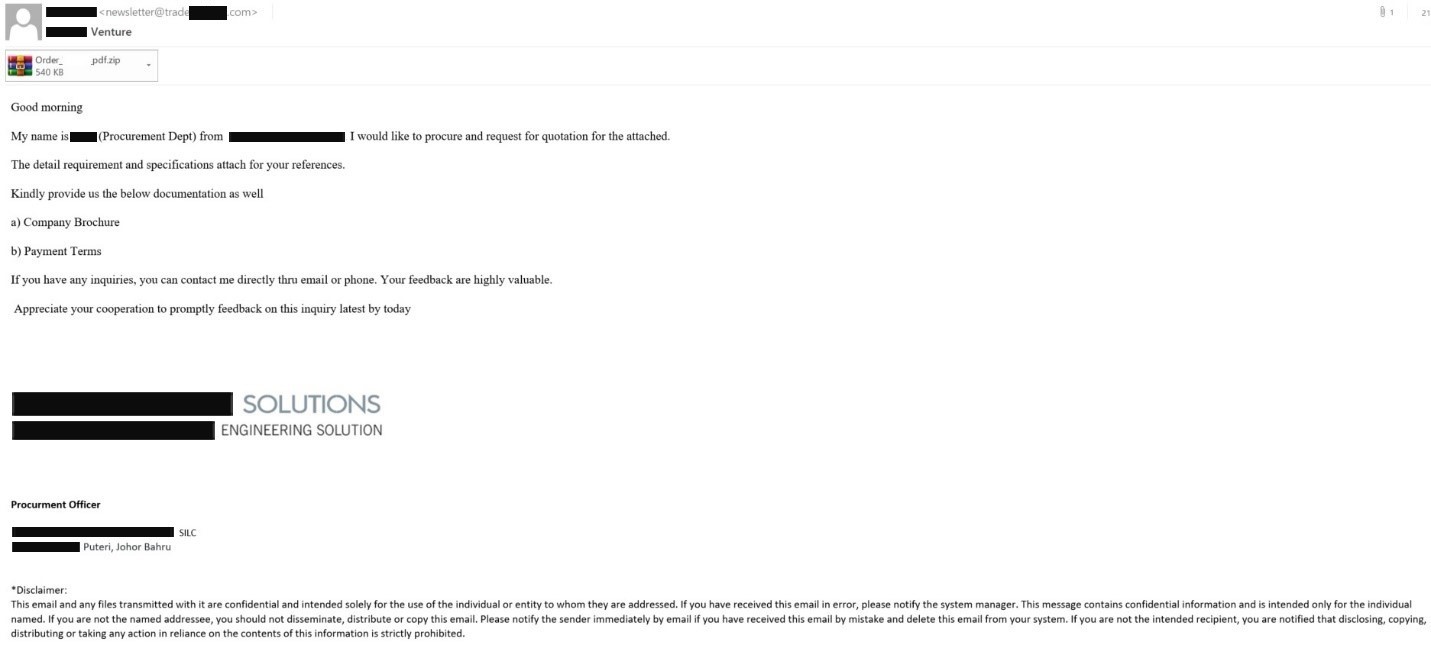
To start with, cybercriminals use real companies as a cover: they supply their e-mails with real logos and legitimate-looking signatures. Their English is far from perfect, so they pretend to be residents of non-English-speaking countries (Bulgaria or Malaysia, for example), so as to raise less suspicion.
The attackers send out their malicious archive on behalf of many companies, changing the text accordingly. Sometimes they ask company employees for prices for certain goods presumably listed in the attached archive, while other times they ask if a listed product is in stock. And we have probably not seen all versions of the text they use to lure their victims. The idea is to convince the respondent to check what kind of goods this pseudo-client is interested in. The cybercriminals have put a lot of effort into the preparation stage, which is not typical for such mass mailing campaigns. Previously we’ve seen such techniques used only in targeted attacks.
From the recipient’s point of view, the only red flag they can spot with the naked eye is the sender’s address. Its domain name rarely matches that of the company, while the sender’s name differs from the name in the signature, which isn’t typical for legitimate business addresses. In the example above, the mail is sent from the “newsletter@” address, which may be ok for a marketing mailout, but absolutely not normal for a letter with a request for prices for a quotation.
What is the Agent Tesla trojan?
Agent Tesla, identified by our solutions as Trojan-PSW.MSIL.Agensla, is fairly old malware, which steals confidential information and sends it to the attack operators. First of all, it hunts for credentials that are stored in different programs: browsers, e-mail clients, FTP/SCP clients, databases, remote administration tools, VPN applications, and several instant messengers. However, Agent Tesla is also capable of stealing clipboard data, recording keystrokes, and taking screenshots.
Agent Tesla sends all collected information to the attackers via e-mail. However, some modifications of the malware are able to transfer data via the Telegram messenger too, or upload it to a website or FTP server.
You can find additional detail about this malware and campaign, along with indicators of compromise, in this Securelist blog post.
How to stay safe
Ideally, such cyberthreats should be stopped at an early stage — when a malicious letter reaches a corporate mail server. While the naked eye can’t always spot a threat at first glance, mail scanners are usually quite capable of such tasks. Therefore, it’s a good idea to protect a mail server with an appropriate security solution.
However, you should also think about raising the level of cybersecurity awareness among your employees; for example, by using online learning platforms.
To make sure the malware sent by the attackers isn’t executed no matter what, you could also consider providing your employees’ computers with a relevant protection.
 e-mail
e-mail

 Tips
Tips