Everything you need to know about Facebook security settings
Facebook regularly changes its security settings. Take a look: A useful new setting may have appeared since the last time you checked.
3956 articles

Facebook regularly changes its security settings. Take a look: A useful new setting may have appeared since the last time you checked.

An unwitting army of connected devices caused an insane disruption of major Internet sites. IoT users need to wise up.

Who is responsible when connected devices go on a crime spree?
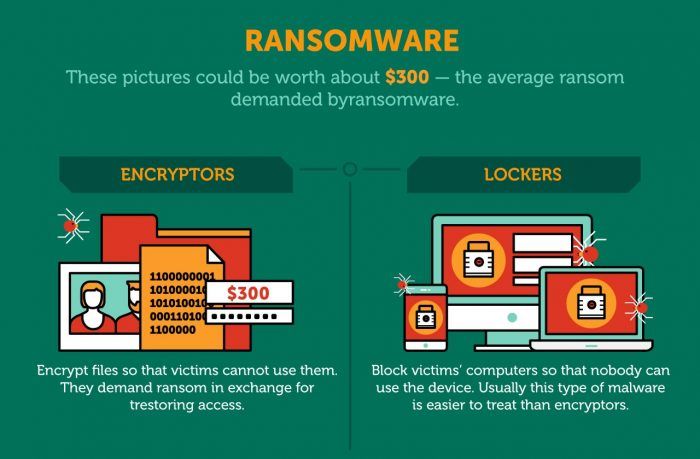

It can be tempting to disregard software update notifications. Everything seems to be working fine. Sometimes programs behave oddly or crash after an update. And by the way, you have

Yet another example of an attack against an ATM: This time the cash machine itself is emulated.
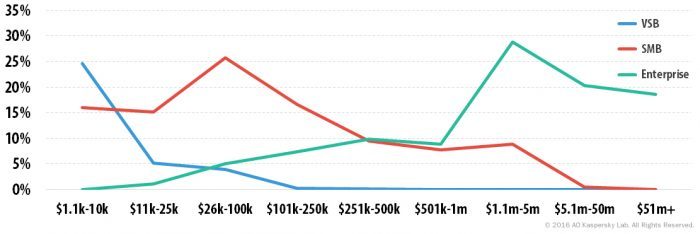
For many SMBs SaaS can provide a cost effective way to take advantage of technology through a cloud-based, subscription model.

Internet Security 2017’s Software Updater keeps your applications up to date — automatically.

Careless behavior online can have devastating personal and financial consequences. Here are seven common shortcuts to avoid.

To protect critical infrastructure, industrial facilities need a way to share information.

ATMs will soon use fingerprint readers and iris sensors to identify customers. But is biometric authentication as secure as advertised?

Three months in, we report on the development of No More Ransom and the goals we’ve already achieved.

With accessible network cables and a lack of authentication between the ATM and the bank’s infrastructure, ATMs are far too easy to attack.

Everything you need to know about mobile banking Trojans and how to fight them.

We explain three important concepts underlying antivirus action: signatures, the nature of viruses, and how antivirus solutions remove malware.

We illustrate for the layman what a virtual private network is and why you need one.


Independent testing agency MRG Effitas put 16 security products through their paces against a battery of malware. Here are the results.

Cybercriminals are always on the lookout for a new trend to exploit and have developed malware that gives them access to encryption software.

We continue our series on the mechanics of Internet advertising. This time we will focus on the the various types of ads and how, precisely, they work.

Kaspersky Safe Kids helps protect your children from inappropriate content and limit device use time, but kids are potentially able to delete the app. Here’s how to prevent that from happening.