
Securing industrial revolution 4.0
Kaspersky Lab has developed a new solution to provide industrial cybersecurity – Kaspersky Industrial CyberSecurity.
3950 articles

Kaspersky Lab has developed a new solution to provide industrial cybersecurity – Kaspersky Industrial CyberSecurity.

Ryan Naraine and Juan Andrés Guerrero-Saade discuss the threat landscape and what is being done to prevent major attacks.

VPN’s features and pitfalls from legal and technical standpoint

Cryptomalware can infiltrate and encrypt an entire network – including its backups – within minutes.

Google has begun phasing out Chrome support on legacy OS X platforms.

Check this out to know if you want to fall for one of the latest Facebook scams
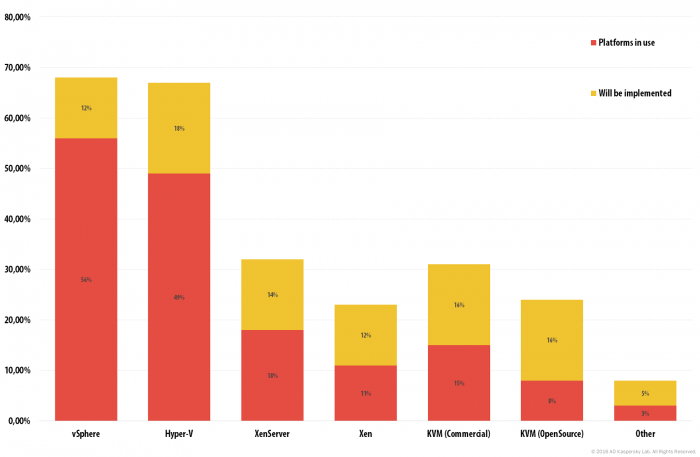
Kaspersky Lab strives for efficient protection and to regularly improve our technology. One of the recent changes affected Kaspersky Security for Virtualization | Light Agent, our security solution for virtual environments. Now it supports one more virtualization platform – Kernel-based Virtual Machine (KVM).

Journalists and their whistle-blowers managed to keep the biggest data leak in secret. How did they do it?

Kaspersky Small Office Security achieves best results in AV-TEST’s latest testing rounds of Windows 10 compatible corporate products.

A bug in Petya ransomware has led to a decryptor that can help those impacted.

They say Facebook severely violates users’ privacy. Is it true and why European authorities claim that?

As the criminals join forces “intercontinentally” to improve their crimeware together, businesses and LEAs should work together as well. Cybersecurity is everybody’s business – today more, perhaps, than ever.

Are you fed up with ad banners and popups, plaguing your iPhone? Install Kaspersky AdCleaner and clean your Safari from ads forever.

Aleks Gostev of Kaspersky Lab’s GReAT discusses the WhatApp move towards encryption and how email needs to be next in adopting end-to-end encryption

USA and Canada governments are fed up with the tyranny of ransomware. Experts from both countries analyzed the latest incidents and released an advisory for their citizens.

Eugene Kaspersky discusses how the world can move towards being more secure.

WhatsApp has just adopted the end-to-end encryption based on Signal Protocol. Kaspersky Daily explains, why it’s the good news and what are the real benefits for all of us.
Categories: Featured, News, Security

Our children might conceal something they do on the Internet from us. What can we do about it?

88% of companies are willing to pay extra in order to work with a bank that has a strong security policy and a good security track record, new survey by Kaspersky Lab shows.

These incidents sound like a detective story, but are taken from real life. It’s almost impossible to avoid targeted hacking and here we explain why is that so.