
Protecting yourself from adware with Kaspersky Internet Security 2016
Did you know that the new features of Kaspersky Internet Security will protect you from the sneaky add-ons for freeware like adware, browser extensions and toolbars?
3956 articles

Did you know that the new features of Kaspersky Internet Security will protect you from the sneaky add-ons for freeware like adware, browser extensions and toolbars?

Researchers expose how a criminal can hack air conditioners to crash the power grid.

According to AV-TEST, Kaspersky Lab solutions are the most efficient and reliable system watchdogs that require very few system resources.

Our products have demonstrated the best results for the third consecutive year, achieving a higher percentage of top-three places and received awards than any other vendor: 82%.

What’s wrong with ATMs’ security and what should the banks do about it

Learn why the true cost of a cyberattack goes far beyond just a loss of data.

Why Steam users often fall victims to scams and frauds and how to avoid it.

Israel’s Electric Authority – an agency in charge of regulating and overseeing the distribution of electricity in Israel – had to mitigate what officials there called a “severe cyber attack.”

Sooner or later each user of the internet will face a trick or trap. Here’s the list of the most widespread ones. Forewarned is forearmed!

Securing Smart Cities has contributed to two studies of The European Union Agency for Network and Information Security (ENISA) on the cybersecurity of public transport in a smart city.

The SAS 2016 has come and gone. Here’s a look back on the top 10 Tweets from the conference to relive the magic.

At SAS 2016 Sergey Lozhkin revealed how he hacked his friend’s hospital and medical equipment.

Vitaly Kamluk of the Kaspersky GReAT discusses Adwind during the SAS 2016.
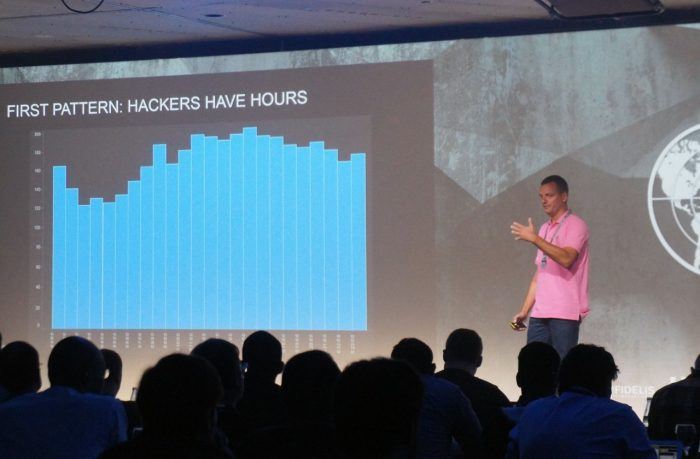
Observing cybercriminals’ behaviour one can find consistent patterns and thus find out who the criminal is in real life

Targeted attacks are visibly commoditizing, choosing cost efficiency over sophistication. If a combination of social engineering, tweaks to widely-available malware and legit apps can do the trick, why bother to create something original and exquisite?

At The SAS 2016, Kaspersky Lab researchers discussed the newly discovered Poseidon Group. A custom APT boutique chasing commercially valuable data

Successful malware writers quickly figured that offering their creations to ‘people-with-a-purpose’ could be very profitable. Yet offering a service proved even more lucrative.

From ancient times, the banking business has been associated with the danger of theft. The advance of technology has provided criminals with extra opportunities.
Kaspersky Security Analyst Summit has begun! In this post we’re running a liveblog from the event – thoughts and impressions of the participants, updated in real time. So everybody’s welcome!

At SAS 2016 our GReAT experts talk about a Java-based multi platform malware used by hundreds of cybercriminals for a handful of purposes