
Internet-proof your children with Kaspersky Safe Kids
What if you could be sure that your kids use Internet safely while their mobile phones are protected from fraud, unwanted calls and SMS? All you need for that is Kaspersky Safe Kids!
3956 articles

What if you could be sure that your kids use Internet safely while their mobile phones are protected from fraud, unwanted calls and SMS? All you need for that is Kaspersky Safe Kids!

Why working in Kaspersky Lab has always been more than just business.

Threatpost had a story last week describing a disruption of a large ransomware campaign connected to the Angler exploit kit. Experts from Cisco’s Talos security group “effectively nillified 50 percent of the exploit kit’s activity”.

In this edition of Security Week infosec digest we’ll cover threecases of companies being hacked and data being leaked and companies reacting on the incidents.

Kaspersky Lab is pleased to announce the continuation of its sponsorship contract with the Scuderia Ferrari Formula One racing team. The new five-year contract will be valid from 2017 until 2021.

Tips and methods of hacking global surveillance: makeup, special clothes, eyeglasses and more.

Frequently, on having installed a free application we’d inadvertently install a plugin or toolbar which alters the home page or search settings. How can you remedy the situation?
In the fierce storm of active APT campaigns there is always something in motion. Researchers pin down and catalogue new threats all the time, but old names occasionally pop up,

Yesterday The European Court of Justice ruled that the Safe Harbor agreement is invalid: what does this decision mean for your personal data?

Are you committing these six online parenting sins? If so, please stop.

A recent study of attitudes toward information risk shows that one in four (24%) IT specialists are concerned about the growing complexity of IT infrastructures and see this trend as a threat to security.

What is the difference between real and theoretical threats?

Have you ever considered your smart office from an IT security viewpoint? Did it occur to you that by equipping your office with devices designed to provide life’s comforts, cybercriminals are handed even more opportunity to gain access to your corporate information and even to cause physical damage?

Our vocabulary continues to evolve as we see slang enter our lexicon. From Googling to memes once-thought silly words have become accepted. This evolution is also impacting the way we write and punctuate statements online.

Kaspersky Lab recently launched an online quiz “Are you cyber-savvy”, and the first results are in. While oriented towards end-users, this quiz’s results may serve as another alert for businesses, especially those that are online-based.
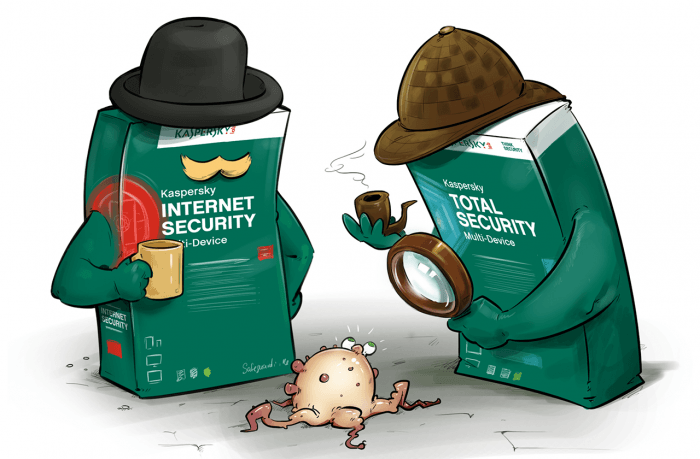
What is the Kaspersky Lab product is best for you? This post outlines the difference between KIS and KTS to help you choose which is better for you.

Today’s smartphones are full-fledged computers much more powerful than the desktops you used 10 years ago. Your device is very likely to contain data the cybercriminals are after, like banking data.

We sit down with one of our interns to discuss what it is like to work within Kaspersky Lab.

While the total amount of companies reporting to experience DDOs attacks is more or less stable over recent years, in 2015 there was a slight increase in the number of businesses considering them the most damaging type of cyberincidents.

Today’s weekly news digest covers the stories about various mistakes in coding, and how they can be used for different purposes, including earning money.
Two young individuals were arrested by Dutch police on suspicion of involvement in CoinVault ransomware attacks.