
The Four Biggest Problems with “Hacking Back”
Call it retribution, justice, or just plain revenge: few films are as satisfying as when the bad guy (or gal) gets what they deserve in the end. But vigilante movies
3946 articles

Call it retribution, justice, or just plain revenge: few films are as satisfying as when the bad guy (or gal) gets what they deserve in the end. But vigilante movies

Russian chess player Mikhail Antipov sponsored by Kaspersky Lab has won the World Junior Championship.

A virus damaging hardware is one of the most widely believed myths in the infosec domain. And, at the same time, it’s the most non-standard one. And it’s not totally a myth, after all.

In the new installment of our explosive hit series “Infosec news” you’ll find: the breach of Bugzilla, Carbanak is coming back and Turla uses Level-God hard to track techniques to hide servers.

Threatpost published a fairly detective-like story earlier this month about an attacker who was able to compromise a Bugzilla, steal bug-related data, and turn it into an exploit.

One of the most interesting ciphers designed to eliminate the vulnerability to symbol frequency analysis was the Vigenere cipher. Which later became the basis of unbreakable one-time pads.

Routers are again becoming a source of cyberthreats as a new batch of security vulnerabilities in UPnP were publicized earlier this month.

By tracking your online activities, advertisers adapt their banner adverts and ad modules. If you don’t want to be tracked, enable the Private Browsing feature.
Law enforcement agencies, with the help of leading IT security providers, are keen on blocking all the malware Command & Control servers they find. Sometimes, they efficiently shut down massive

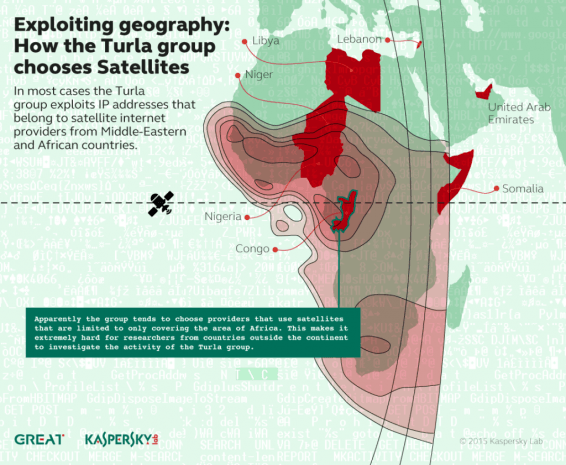
Kaspersky Lab’s researchers have found that Russian-speaking Turla APT group is exploiting satellites to mask its operation ant to hide command-and-control servers.
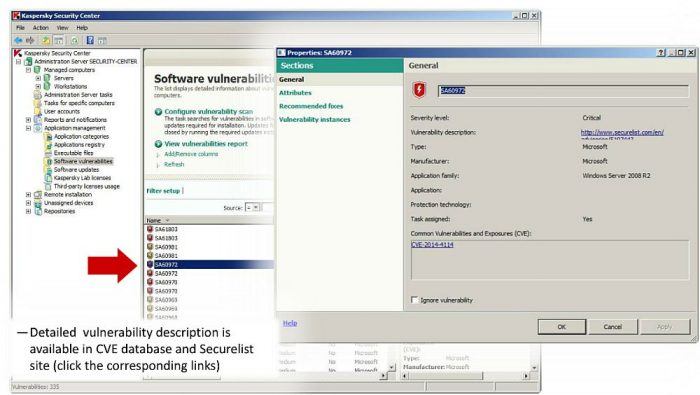
Kaspersky Security Center 10, the Kaspersky Lab’s unified management console, makes it easier to manage and secure all your endpoints – including physical, virtual and mobile devices.

The new trend on IFA 2015 is all about integrity and security. Meet Kaspersky Lab’s observations from the trade show.

Information security digest: the greatest iOS theft, farewell to RC4 cipher, multiple vulnerabilities in routers

We received more accolades from AV-Comparatives in late August, and we would like to take a moment to share them.
Headlines raise alarm: the greatest hack in history finally reached iOS. Is that really so and who are the potential victims?

The rulebook for freethinking people: how not to get made the next time you log on Ashley Madison or buy goods in a sex shop online.

RAT stands for Remote Administration Tool. While it may sound rather innocuous, the term “RAT” is usually associated with the software used for criminal or malicious purposes.

I won’t even dare to ask if you are sick and tired of banner adverts on the Internet. I’ll better tell you how to get rid of them with help of Kaspersky Internet Security.

They teach a lot of things in schools, but they never tell you how to be safe in Internet. We have several simple advices on cybersecurity for you, that will help you stay away from trouble.

The results of the recent IT Security Risks Survey 2015 show that half of banks and payment systems prefer to handle cyberincidents when they happen, rather than invest in tools to prevent them.

Infosec digest: exploit kit Neutrino in Wordpress, yet another GitHub DDoS, Wyndham responsible for breach, while Target is not.