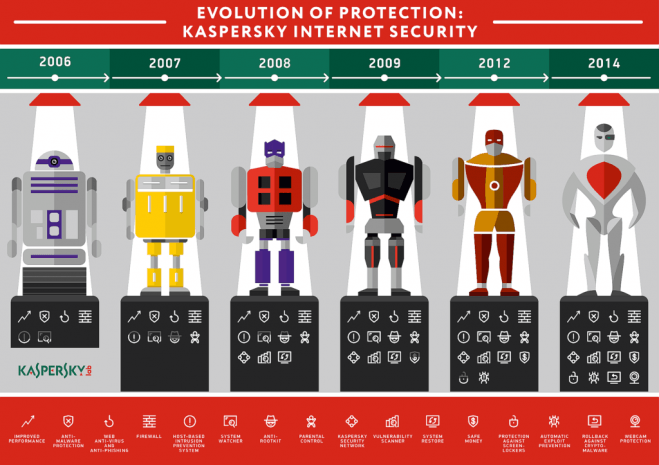
More than an antivirus, p.2: When and why the antivirus alone became insufficient
It’s not feasible to call a security solution, either for individual users or for businesses, “an antivirus.” There’s more than that.
3949 articles

It’s not feasible to call a security solution, either for individual users or for businesses, “an antivirus.” There’s more than that.

The 2016 editions of the Kaspersky Lab product suite have enhanced privacy options for the company’s customers.
Three most important recent news with extensive commentary and trolling: nasty Android Stagefright vulnerability, new car hacks and Do Not Track 2.0 privacy initiative

Kaspersky Lab experts have investigated a new series of attacks by the Darkhotel cybercriminal group. Here are the details.
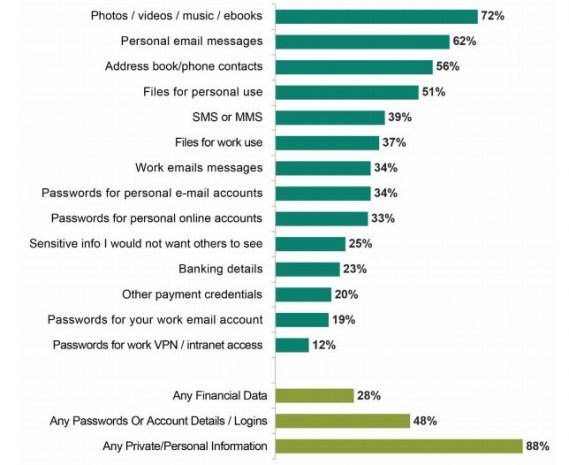
Kaspersky Lab has rolled out a new cyberthreats report covering Q2. While it is consumer-oriented, certain findings are extremely relevant to business.

Predictability of human beings can barely be overestimated when it comes to passwords. But what about lock screen patterns, are we predictable as well when we’re creating them?

Researchers compete at finding security holes in infotainment systems of connected cars and breaking in. The new case proves that Tesla does care a lot about security at wheel.

Security researcher Chris Rock discovered, that it’s very easy to kill a human. All you need is just a computer with Internet access, some knowledge and common sense.

Is it still correct to use the term “antivirus?” Cybersecurity today is much more than just antiviruses; still essential, but alone it is no longer enough.

Recently we wrote about the Jeep Cherokee hack incident. At Black Hat security researchers Charlie Miller and Chris Valasek finally explained, how exactly the now-famous Jeep hack happened.

Apple patched a serious issue in its App Store and iTunes Store, which could have undermined many of the businesses working in this ecosystem.

History, tradition, passion and belonging to the world of motorsport. The 24 hours of SPA was all that and so much more

The number of vulnerable Google devices reached an all-time high since worst Android flaws ever are uncovered. There are already patches available but they may never reach end users.
Windows 10 was launched to general availability on July 29th. The feedback so far is mixed, which isn’t unusual with new versions of Windows. Some say it’s the best Windows since XP, some call for caution. Security-wise and business-wise it looks promising.
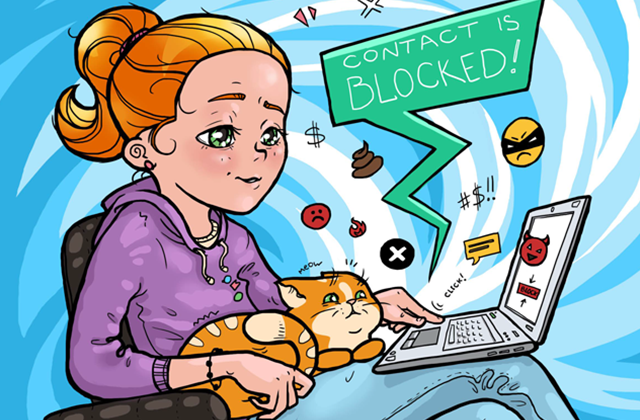
Confronting cyberbullies? Behave smart; don’t do what mockers expect from you. Check these tips to keep the situation under control.

Since Windows 10 arrived two days ago, new security-related concerns have surfaced. First and foremost, they’re about control over the data on Windows 10-based PCs and other devices.

Security experts often mention exploits as one of the most serious problems, although it’s not always clear why exploits are so special and scary. We’ll try to explain here.

Among all of its promised security enhancements, Microsoft also said that updates will be performed as a “service”: Users will receive new features at no charge for the “supported lifetime” of the device it is installed on.

Kaspersky Lab launches the new versions of its flagship products, designed with privacy concerns in mind.

It’s up to the manufacturers to change the approach to designing modern hi-tech equipment. As we have written before, security should come first. It must be taken in account at the design level, not added later.

A contactless bank card is a super-convenient thing. However, its ease of use would make you wonder whether stealing your money is equally easy.