
All posts
3952 articles


Kaspersky Small Office Security: administrative tools for all
There is a joke about a note in a letter saying “Burn after reading.” It’s not the highest degree of secrecy. The best form of secrecy would be “Eat before

Can Air Drones Really Replace Santa’s Sleigh?
It seems Santa’s reindeer could be deprived of their usual Christmas duty by 2016, as Amazon would arrange for your Christmas presents to be delivered via air drones. Moreover, the

Tip of the Week: How to Wipe Sensitive Data From a Lost Phone
Christmas and New Year’s Eve celebrations are quickly approaching, which means dinners with friends and relatives as well as parties and festivities. But, the holiday rush often makes us less

Kaspersky 7 Volcanoes Expedition Finale: On The Top Of Ojos del Salado
There is an opportunity for adventure in everyone’s life. We at Kaspersky Lab respect adventurous, maverick souls and that’s why we’ve helped Olga Rumyantseva, the Russian alpinist, climb the highest

Top Security Stories of 2013
In this video, Vitaly Kamluk of Kaspersky Lab examines the biggest security news of 2013 and talks about the lasting effects they may have.

Christmas Party Survival Guide
Expecting to attend a lot of parties and get-togethers before Christmas? Check out our infographic to make sure you and your gadgets are well-prepared!
No hotbed for cybercriminals: preventing valuable data leaks
The Problem At present, even very small companies store information that could cause irreparable damage to their financial future if it fell into the wrong hands. An example of this

Data encryption in Kaspersky Small Office Security: the way to be sure
Sony Corp. underwent a large-scale fiasco in April 2011, when a security breach affected tens of millions of people. The intruders stole the personal data of many users along with

Tip Of The Week: Use Kaspersky Internet Security To Guard Your Health
We all know that working on a computer for hours can affect our health. Our eyes and back need rest regularly. However, sometimes we are too busy and we forget

Ask The Expert: Nikolay Grebennikov Answers Questions From Kaspersky Users Via Social Networks
Information security issues are of greater importance today than ever, and they should be a concern for everyone. The people who can address their concerns to a real expert are

Kaspersky Lab: Rated No. 1 in Protection
It’s that time of year when you’re buying new computers for yourself, your family or your business. And because you want to take care of the items you spend good

This Year in Cybersecurity
2013 will be remembered by both security professionals and everyday people for the number of events that took place in information security. Various incidences, from Edward Snowden’s revelations to the
Java vulnerabilities keep breeding
As many as 4.2 million attacks using Java exploits were repelled by our Automatic Exploit Prevention system between September 2012 and August 2013. This number indicates two points. The first

The Secret For An Anti-Virus’s Flawless Work
Being a careful and consistent user, you might have read the License Agreement for the product that is installed on your computer. Today we would like to draw your attention

Stopping Unsafe Christmas Gift Searches
It is more important than ever during the holiday season that parents monitor and protect their childrens’ web activities. That’s because kids with toys on the brain – so basically
Case 1. Big problems for very small businesses: banking malware
The Problem We often hear from small business owners that the modest size of their companies provides them with “invisibility protection”. Employees believe that their organization and its activities are

Is Onboard Wi-Fi Safe?
From takeoff to landing, the U.S. Federal Aviation Administration and its counterpart in the European Union have cleared the use of computers and mobile devices, though flyers will still be
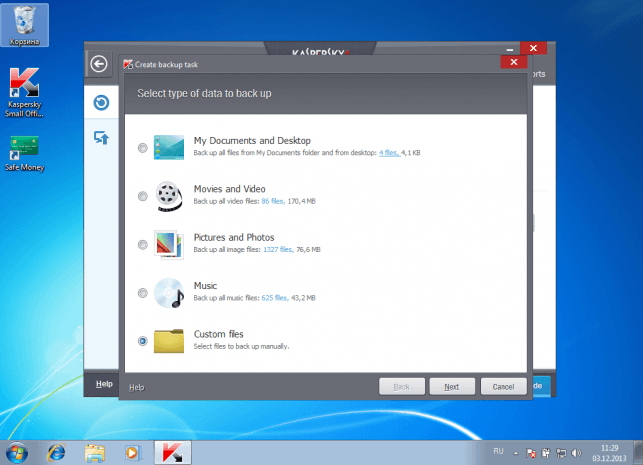
Data backup as elemental security
It was a very typical situation of “yesterday it worked!” In the morning, the accountant’s laptop would not turn on. More precisely, it did turn on but the operating system

Two million passwords have been stolen. What about yours?
Any of your passwords, be it for email, social networks or online banking hold value for cybercriminals, because almost any stolen account can be used in fraud schemes. It’s no
 device protection
device protection security
security 7 volcanoes
7 volcanoes data protection
data protection data
data Automatic Exploit Prevention
Automatic Exploit Prevention