
Dos and Don’ts for Creating Secure Passwords
These days we conduct so much of our lives online that invariably – whether it is with our online bank accounts, our shopping sites, our credit cards, our emails –
3930 articles

These days we conduct so much of our lives online that invariably – whether it is with our online bank accounts, our shopping sites, our credit cards, our emails –

Most people are aware that there is a seemingly infinite sea of hackers out there whose goal in life is to steal sensitive data from corporate networks. And while tomes
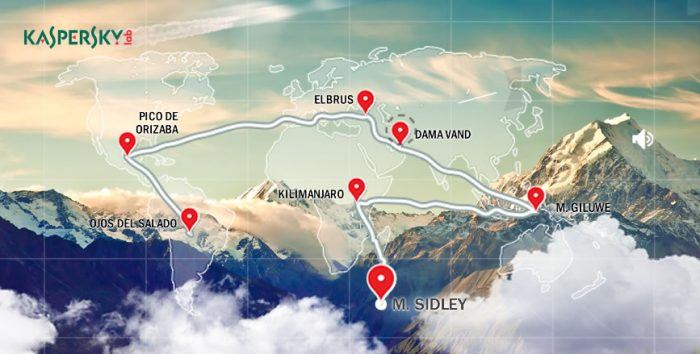
Climbing the highest volcanoes on every continent alone, without any backup is definitely not for the faint-hearted! You’d have to be bold, spirited…and just a little bit crazy. But Olga

Google’s social networking site, Google+, continues to grow in popularity. But as with all social media sites, over-sharing your personal information is easy to do on Google+. Use these 10

Heads up, you secretive Facebook users who have made yourself unsearchable on the world’s most popular social networking platform: You can hide no more. Facebook announced updated privacy features —

It’s that time of year when, in the afterglow of the holiday season we start to play with all of our new toys. For a lot of people that will

You probably hadn’t even thrown away the wrapping paper and upgraded from pajamas to pants before you were knee-deep in your new computer (probably a laptop of one brand or

When a browser asks you if you want it to store, save, or remember your password and you allow it to do so, it actually does store your password in

The first thing you want to be aware of when discussing security features on Google’s Chrome browser is that many of the best options aren’t built into the browser, but

It may seem like a great idea to become Facebook friends with people overseas that you’ve never met – and never will meet – but Facebook has a suggestion: don’t

It’s a sad reality that, sooner or later, most businesses will be hacked. If this happens to your business, there are two types of response to avoid. First, there’s the

On Christmas Eve we counted the results of our light-hearted survey on Facebook. Users were asked to say which piece of malware, if any, they most associated with Santa. It

Although some people dismiss it as a minor concern that’s exaggerated by over-protective parents, cyberbullying can have devastating effects on children and families. While traditional bullying can involve physical and

This really shouldn’t need to be said, but here goes: You should never, ever – under any circumstances – post a picture of your debit or credit card anywhere online.

If you’re on Twitter, you know the Fail Whale: When Twitter’s servers get overloaded (it happens surprisingly often) an image appears of a sleepy whale being hoisted out of the

The last year has seen a lot of changes in the threat landscape, with the emergence of a number of new cyber espionage tools such as Gauss and Flame, as

Computers have advanced in the last 20 years from building-sized mainframes to smartphones that can fit in your pocket (and have become infinitely more capable, to boot), yet we use

Everyone knows you should have antivirus applications running on your work and personal computers, but far fewer people take seriously the threat of malware attacks to their mobile devices –

In recent years, cybercriminals have stepped up their efforts to get hold of users’ money. Credit card numbers, login details for online banking, passwords and codes – all this and

It’s always frustrating if your smartphone or tablet gets lost or stolen – and that frustration is compounded by the loss of valuable data stored in the device’s memory. Worse

The good old days, when the owners of mobile phones and smartphones had little to fear from malicious programs and could keep all their personal info in their devices’ memory,