
Black Friday: Be ready to protect your business
Analysis shows that the attackers are particularly active during the holiday period.
3946 articles

Analysis shows that the attackers are particularly active during the holiday period.

Kaspersky Lab will be showcasing and offering beta version of Kaspersky Security integration with ConnectWise.

You can catch a Trojan even if you visit only legitimate websites. This post explains how it happens and what you should do to protect yourself.


Kaspersky Internet Security can analyze your system, detect unwanted programs and offer to uninstall them — and it works even on programs that resist removal.

FAQ about ransomware: types, origins, dangers, and how you can stay safe

Router manufacturers and ISPs are trying to make Wi-Fi set up as easy as possible — and in the security business, we know e-a-s-y spells trouble.

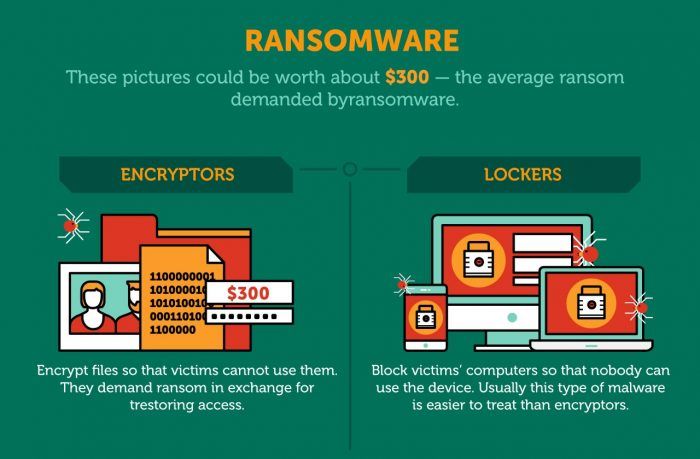
Ransomware research shows that paying ransom is no guarantee you’ll get your files back.

Photo files typically contain additional data on shooting conditions, including a geotag. What happens to this data when the photo is published online?

Forrester Research interviewed vendors and customers to evaluate top endpoint security providers.
Facebook regularly changes its security settings. Take a look: A useful new setting may have appeared since the last time you checked.

An unwitting army of connected devices caused an insane disruption of major Internet sites. IoT users need to wise up.

Who is responsible when connected devices go on a crime spree?

It can be tempting to disregard software update notifications. Everything seems to be working fine. Sometimes programs behave oddly or crash after an update. And by the way, you have

Yet another example of an attack against an ATM: This time the cash machine itself is emulated.
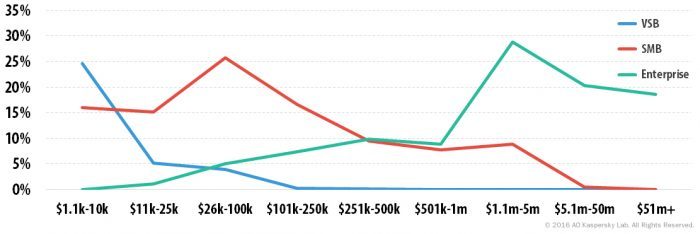
For many SMBs SaaS can provide a cost effective way to take advantage of technology through a cloud-based, subscription model.

Internet Security 2017’s Software Updater keeps your applications up to date — automatically.

Careless behavior online can have devastating personal and financial consequences. Here are seven common shortcuts to avoid.

To protect critical infrastructure, industrial facilities need a way to share information.