
Ask the expert: Vitaly Kamluk answers questions about malware and security issues
Vitaly Kamluk answers our readers’ questions about malware counteraction and various security issues.

248 articles

Vitaly Kamluk answers our readers’ questions about malware counteraction and various security issues.

Hackers and cyberspies are not something you only see at the movies. The Internet is actually crawling with weirdos and criminals who are just looking for a chance to infect your smartphone or steal your gaming account.

MRG Effitas awarded Kaspersky Lab its highest accolade for the development of reliable security technology for online banking.

Kaspersky Lab security expert Vitaly Kamluk answers our readers’ questions about DDoS and botnets counteractions.

Vitaly Kamluk answers our readers’ questions about his work with INTERPOL and other digital investigations.

The web service for secure password storage, LastPass, asks users to change their passwords ASAP.

The first technology to enable instant long-distance communication was the telegraph. Back in its time, the telegraph helped to shape many of the current IT infrastructures.

We’ve collected the most interesting books and movies which give a lot of detail on how exactly ciphers are solved.

Recently, Apple’s CEO Tim Cook delivered a speech on privacy and security during EPIC’s Champions of Freedom event. Here are the 10 best quotes from his speech.

Kaspersky Lab experts detected a sly scheme that allows fraudsters to steal personal data without your login and password.

We have worked together with child psychologists from across the globe to put together recommendations on how to support a victim of online bullying.

Ransomware is a huge problem nowadays, with new examples circulating on a regular basis. Learn how to protect yourself.

Our personal implementation of the cloud security model is called Kaspersky Security Network. And here we’ll explain how it actually works.

A legendary Soviet spy, Richard Sorge, is famous for conveying the exact date of the German invasion into the Soviet Union, and for letting the command know Japan had no plans of attacking the USSR in the Far East.

Five lessons from the story of the Enigma cryptographic machine which are still relevant.

During WW2 modern cryptography principles were often coupled with ‘amateur’ ciphering methods. Curiously, the latter ones often proved to be equally reliable
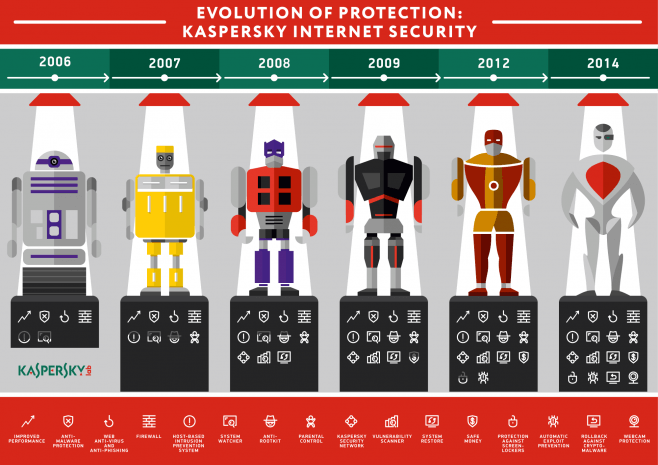
We’ve created an infographic that shows how the Kaspersky Lab flagship antivirus software has improved over the last 10 years.

Yet another APT of the ‘Dukes family’ is hitting high-profile targets, including the US government office.

Recent report by US GAO was treated by medias as “Modern aircrafts can be hacked and commandeered through onboard Wi-Fi”. Is it really that bad?

While surfing the Internet, children may come across web pages containing inappropriate information. IT solutions can help protect children from such content.

With so many games and apps available for download on your mobile devices, it’s important to remember that not all of them are suitable for children. That’s why you should be monitoring what your kid installs.