
Should we protect embedded Linux devices?
Can Linux-based embedded systems be considered secure by default or do they require additional protection?

Senior Global Product Marketing Manager, Kaspersky
21 articles

Can Linux-based embedded systems be considered secure by default or do they require additional protection?

If your company uses devices running Windows XP, this source code leak is yet another reason get them protected.

Our security solution for Internet gateways is updated and more capable than ever.

Web threats are actively used in targeted attacks, so their neutralization should be an integral part of APT defense strategy.

Start protecting your network by stopping potential threats way before they can get too close — on the Internet gateway level.

Implementing effective cybersecurity technologies does not equal GDPR compliance, but it is among the cornerstones on which this compliance is built.

Protecting a hybrid infrastructure from a single console

The never-ending cycle of Adaptive Security Architecture. Ideally, it enables us to stay ahead of cybercriminals, creating and improving security systems.

We shared our general vision of today’s threat landscape at Kaspersky Lab’s RSA booth.

In our previous article on this topic, we looked into the history of memory-only attacks, also taking a glance at attack scenarios and appropriate defensive technologies. Now it is time

One of the most sophisticated mechanisms malware uses to stay below security systems’ radars is having no detectable file body. Malware creators use various techniques to accomplish that. Perhaps the most insidious of which is the execution of the malicious code wholly within the machine’s volatile memory.

An Indian-speaking threat actor, Dropping Elephant chooses targets mainly in the Asian region, paying particular attention to Chinese government/diplomatic organizations – and also to foreign embassies and diplomatic offices in China.

One of the most popular techniques used to penetrate corporate defenses is the use of vulnerabilities found in working software, which, in fact, do not need to be brand-new 0-days.

Targeted attacks are visibly commoditizing, choosing cost efficiency over sophistication. If a combination of social engineering, tweaks to widely-available malware and legit apps can do the trick, why bother to create something original and exquisite?

Successful malware writers quickly figured that offering their creations to ‘people-with-a-purpose’ could be very profitable. Yet offering a service proved even more lucrative.

From ancient times, the banking business has been associated with the danger of theft. The advance of technology has provided criminals with extra opportunities.

The majority of targeted attacks hitting businesses nowadays are conducted with cyberespionage in mind, harvesting precious business secrets or confidential personal data. But from time to time attackers get up to something completely different – like sabotage.

Introduction Running a datacenter involves a plethora of complex tasks, of which security is just one. But the security of virtual environments and data storage in particular is critical to
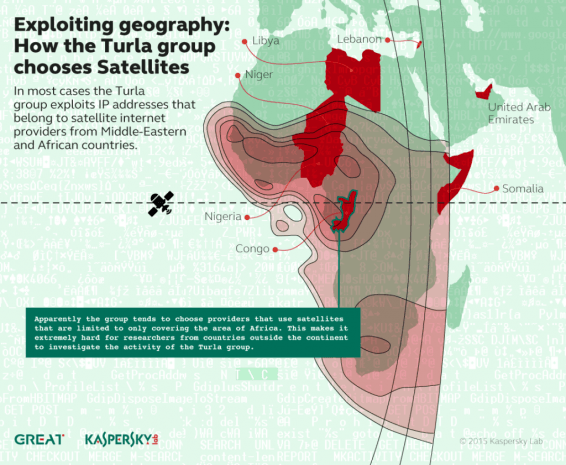
Law enforcement agencies, with the help of leading IT security providers, are keen on blocking all the malware Command & Control servers they find. Sometimes, they efficiently shut down massive

Attacking a broad spread of companies allows the group to access potentially valuable ‘bonus’ data from unexpected sources.

Yet another Duke APT is hitting high-profile targets, including the US government office. This time it’s CozyDuke (also known as CozyBear, CozyCar or “Office Monkeys”, in honour of the video it employs as a decoy).