
Indestructible malware by Equation cyberspies is out there – but don’t panic (yet)
A malware that cannot be wiped from the victim’s hard drive does exist. However, it’s so rare and expensive, that you probably won’t ever encounter it.

“Just because you're paranoid doesn't mean they aren't after you” ― Joseph Heller
272 articles

A malware that cannot be wiped from the victim’s hard drive does exist. However, it’s so rare and expensive, that you probably won’t ever encounter it.

As a student, I had a part-time job offering PC support services. Now, when visiting relatives who aren’t good at servicing their computers, I often have to apply my expertise once again.
One morning when I was in a hurry to get to work, everything went wrong in an instant: an SMS message alerted me to an $80 charge to my credit card for a purchase that I never made.

The owners of certain expensive cars can analyze their driving skills in the same way F1 pilots do. However, this information is sensitive and, thus, should be protected.

Almost three dozen computers are required by Ferrari engineers to analyze everything happening with a racecar and decide on the maintenance. However, there are other computers in the paddock, very unusual ones.

What changed in Sochi since Olympic games? Does infrastructure suit Grand Prix? Let’s find out together.

We have bought our very own Blackphone to check its security firsthand.

Data breaches have become a routine. It can happen to any site, any day. You can’t prevent it, but there is a way to minimize the damage.

Your iPhone runs hidden monitoring services. Who uses them, and for what purpose?
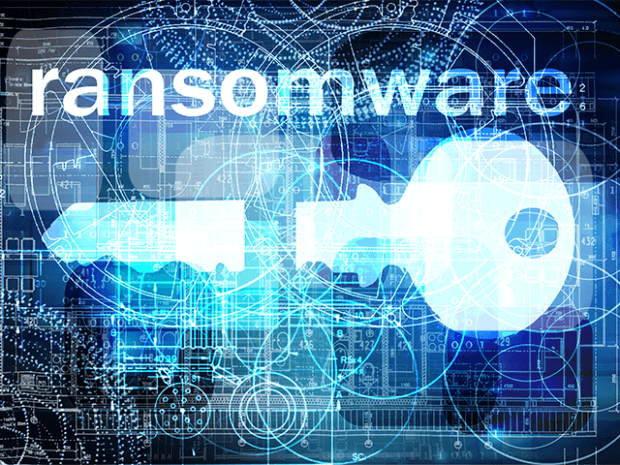
A new version of file-encrypting malware hides its sever inside an anonymous TOR network, making it safer for criminals to extort money from victims.

Criminals invented Cryptolocker, spying malware and Zeus banking Trojan. We have new protection against them.

New analysis pinpoints some weaknesses in a new generation of cars with online capabilities. If exploited, this may result in car theft and other problems.

Let’s analyze new safety features in the upcoming Android release while we wait for it to arrive.

Kaspersky Lab’s recent research demonstrates that cyber-stealing is a very profitable and well-organized crime.

There were long time rumors about iPhone malware used to spy on smartphone owners, but now it’s official ―Kaspersky Lab researchers discovered a real life sample of this Trojan.

Computer ransomware is getting more sophisitcated, while mobile cryptolockers are emerging both in Europe and the U.S.
Teaching your child the essential codes of conduct on the Internet is as important as teaching them road safety.

What Facebook habits make you vulnerable and how to avoid them.

It’s ridiculously simple to lose your money because of credit card fraud. Secure yourself in all stages―from choosing your card to paying overseas ―using our simple guide.

OpenID and OAuth are protocols responsible for those “Login with Facebook” and “Authorize with Google” buttons you see on almost every site nowadays. Of course, there is a hack for that™, but you don’t need neither panic nor change your password. Read on for our simple action plan.

Top Apps to protect you from prying eyes, mischievous kids, thieves, natural disasters, forgetfulness and of course malware.