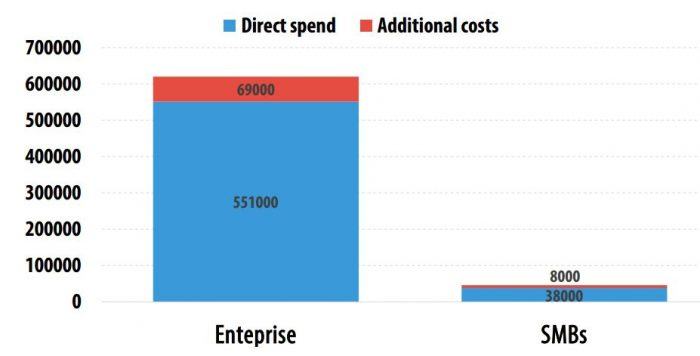
Businesses keep losing large sums to recover from cyberattacks – survey
Kaspersky Lab, together with B2B International, has conducted a new survey of IT security risks.
1247 articles

Kaspersky Lab, together with B2B International, has conducted a new survey of IT security risks.

New variants of the “legendary” banking Trojan Carbanak are making the rounds on the Web, so far noticed in Europe and the United States.

Call it retribution, justice, or just plain revenge: few films are as satisfying as when the bad guy (or gal) gets what they deserve in the end. But vigilante movies

Threatpost published a fairly detective-like story earlier this month about an attacker who was able to compromise a Bugzilla, steal bug-related data, and turn it into an exploit.

Routers are again becoming a source of cyberthreats as a new batch of security vulnerabilities in UPnP were publicized earlier this month.
Law enforcement agencies, with the help of leading IT security providers, are keen on blocking all the malware Command & Control servers they find. Sometimes, they efficiently shut down massive
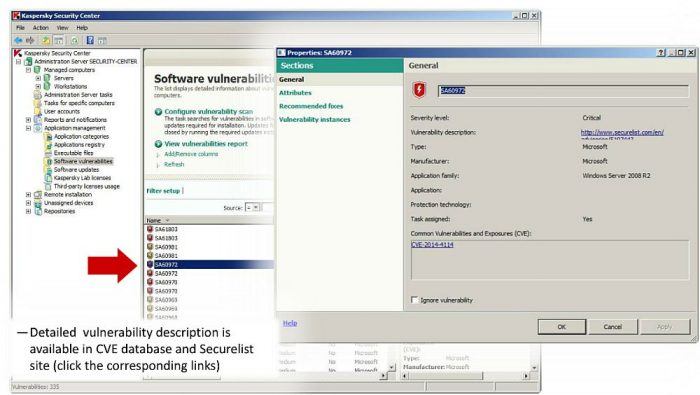
Kaspersky Security Center 10, the Kaspersky Lab’s unified management console, makes it easier to manage and secure all your endpoints – including physical, virtual and mobile devices.

We received more accolades from AV-Comparatives in late August, and we would like to take a moment to share them.

RAT stands for Remote Administration Tool. While it may sound rather innocuous, the term “RAT” is usually associated with the software used for criminal or malicious purposes.

The results of the recent IT Security Risks Survey 2015 show that half of banks and payment systems prefer to handle cyberincidents when they happen, rather than invest in tools to prevent them.

Kaspersky Lab’s Q2 report on spam and phishing has arrived, and brought little surprises.
Kaspersky Lab has just released a new version of Kaspersky Endpoint Security for Mac, specifically for Mac-savvy businesses.

A new Kaspersky Lab report finds businesses pay a significant premium to recover from a cyber attack if the virtual infrastructure is affected during the incident.

A look at what the “threat landscape” is comprised of for businesses.

The BlueTermite APT campaign is rather new and extremely persistent. Here’s why.

These days, the propagation of zero-day exploits occurs almost literally at the speed of light. As soon as such useful exploit makes it to the public, APT authors can begin

The experience of forgetting information you trust a digital device to remember for you is called Digital Amnesia. Digital Amnesia’s impact on businesses can range from mere inconvenience to something far more serious.

Kaspersky Lab has just received a trove of new awards for one of its business products, Kaspersky Small Office Security.

Kaspersky Lab has just released its Q2 report on DDoS activities on the Web, showing that this part of the global threat landscape is extremely volatile and permanently evolving.
It’s not feasible to call a security solution, either for individual users or for businesses, “an antivirus.” There’s more than that.

Kaspersky Lab experts have investigated a new series of attacks by the Darkhotel cybercriminal group. Here are the details.