Mobile issues of end users and their relevance to businesses
Kaspersky Lab has rolled out a new cyberthreats report covering Q2. While it is consumer-oriented, certain findings are extremely relevant to business.
1247 articles

Kaspersky Lab has rolled out a new cyberthreats report covering Q2. While it is consumer-oriented, certain findings are extremely relevant to business.

Is it still correct to use the term “antivirus?” Cybersecurity today is much more than just antiviruses; still essential, but alone it is no longer enough.

Apple patched a serious issue in its App Store and iTunes Store, which could have undermined many of the businesses working in this ecosystem.
Windows 10 was launched to general availability on July 29th. The feedback so far is mixed, which isn’t unusual with new versions of Windows. Some say it’s the best Windows since XP, some call for caution. Security-wise and business-wise it looks promising.

Since Windows 10 arrived two days ago, new security-related concerns have surfaced. First and foremost, they’re about control over the data on Windows 10-based PCs and other devices.

Among all of its promised security enhancements, Microsoft also said that updates will be performed as a “service”: Users will receive new features at no charge for the “supported lifetime” of the device it is installed on.

It’s up to the manufacturers to change the approach to designing modern hi-tech equipment. As we have written before, security should come first. It must be taken in account at the design level, not added later.

If it is not possible to get rid of a risky software for some reason, it is better to exist in a “presumption of guilt” mode, with an efficient security solution keeping it in check and preventing exploits from successful attacks, targeted ones included.

Top-level IT security pros believe there’s a significant, unaddressed gap between enterprise security priorities and the serious threats that keep them awake at night.

Minidionis is yet another backdoor from the same APT group responsible for CozyDuke, MiniDuke, and CosmicDuke – this time with some “cloud” capabilities.

These days, ransomware-related news stories look a bit like, well, war chronicles. In fact, this is the consequence of an elevated attention to this particular kind of threat; similar things occurred in early the 2000s when net-worms thrashed the Web.

Exploits are a subset of malware, but they are not always detectable by security software if it doesn’t employ behavior analysis. In fact, it’s the only good way to beat exploits. Malware programs may be plentiful and varied, but most of them have similar behavioral patterns.

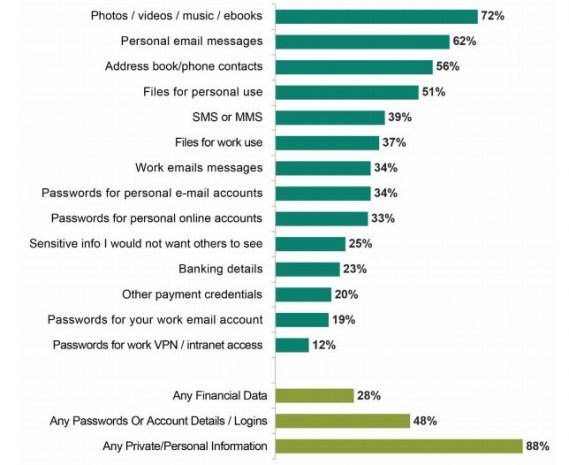
With all of the security improvements, criminals find and exploit various ways of circumventing them to deliver their malicious creations to end-users’ phones, which puts at risk both the device owners and the businesses they are involved with.

More than a half of mobile devices users carry out financial transactions on them, and roughly the same amount stumbled upon a financial threat recently. Yet, in most cases, there are no security solutions and/or passwords in place.

You tell them: Hey guys, you have snakes in your backyard. And they tell you: No, no, that’s impossible. They stick to their belief until the moment when a stick under their own leg turns into a venomous monster.

They say history repeats itself and that holds true with revolutionary development. The malware industry has advanced so much that antique ideas are relevant again.

Throwing away the old junk makes the environment healthier in every possible sense.

Attacking a broad spread of companies allows the group to access potentially valuable ‘bonus’ data from unexpected sources.

Earlier this year, Kaspersky Lab’s products received commendations from a number of respected independent testing labs. Here are a few pertaining to our business-oriented products.

A huge state-of-art building on 18 Napier Road in Singapore is nestled among the green created by local flora and tropical climate, almost like a spaceship. As written on the

Kaspersky Lab recently released the list of its newly received patents on both sides of the Pacific. We take a look at a few of them.