
Security Incidents Digest, Aug. 18 – Sep. 18
Black Tuesday August the 13th brought numerous challenges to (primarily) corporate users of Microsoft products. The company released patches for critical vulnerabilities in Windows, Exchange Server and Active Directories. As
 Cybersecurity
Cybersecurity
 BYOD
BYOD social networks
social networks endpoint security
endpoint security




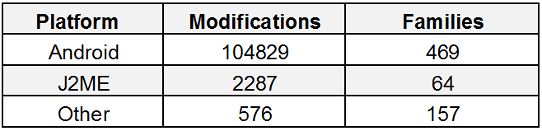

 Android
Android
 mobile devices
mobile devices
