
Listen, Chrome…
It appears that PCs are not only able to spy on you via cameras, but they’re also able to listen in on you on as well, and in a discreet
1436 articles

It appears that PCs are not only able to spy on you via cameras, but they’re also able to listen in on you on as well, and in a discreet

We are proud to announce that Kaspersky Internet Security, the flagship home user product of Kaspersky Lab, has received the ‘Product of the year’ award from the independent testing lab

For as long as I’ve been working in the security industry, which – in the spirit of full disclosure – hasn’t been a very long time, I have been shocked

At the end of 2012, we thought were about to observe the End of the world. In 2013, the end of Futurama was gravely approaching. 2014 will bring us the

Bitcoin is a cryptocurrency that owes much of its popularity to its rather volatile — and occasionally very high — price. Its potential for investors has made it a tempting

I understand your initial interest in this article, but a disclaimer: porn is not the main topic of discussion in this post. Rather, I will focus on a position at

Reports emerged earlier this week that the Starbucks’ iOS mobile application could be exposing the personal information of any customers that downloaded it. To their immense credit – especially considering

A number of widely used iOS banking applications from some of the world’s most prominent banks contain bugs that expose users to data theft and account takeovers. Specifically, a knowledgeable

Skype commercials make grandparents seem so happy, and why wouldn’t they be? Through the magic of the Internet, they can connect with their grandchildren and other loved ones instantly and

It may be the New Year, traditionally a time for new resolutions and goals, but we at Kaspersky Lab are continuing our dedication to standing by our promise to bring

The global Kaspersky Daily blog (blog.kaspersky.com) will be on recess from December 24 through January 8. Between those two dates, you’ll find no new content on the global blog (except
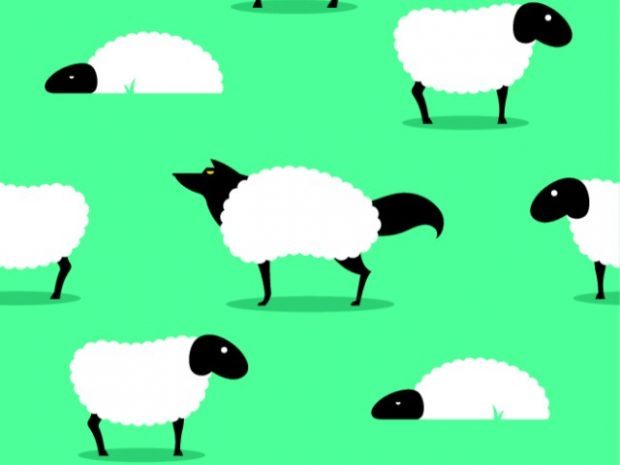
Social engineering, sometimes called the science and art of human hacking, has become quite popular in recent years given the exponential growth of social networks, email and other forms of

Firefox mandates in its latest update that all Java plug-ins will operate on a click-to-play basis. Google removes a key privacy feature and fixes a serious vulnerability in its Android

It seems Santa’s reindeer could be deprived of their usual Christmas duty by 2016, as Amazon would arrange for your Christmas presents to be delivered via air drones. Moreover, the

It’s that time of year when you’re buying new computers for yourself, your family or your business. And because you want to take care of the items you spend good

2013 will be remembered by both security professionals and everyday people for the number of events that took place in information security. Various incidences, from Edward Snowden’s revelations to the

It is more important than ever during the holiday season that parents monitor and protect their childrens’ web activities. That’s because kids with toys on the brain – so basically

From takeoff to landing, the U.S. Federal Aviation Administration and its counterpart in the European Union have cleared the use of computers and mobile devices, though flyers will still be