
Technology
157 articles


How Internet ads work, part 2
We continue our series on the mechanics of Internet advertising. This time we will focus on the the various types of ads and how, precisely, they work.

I, for one, welcome our new chatbot overlords
Powerful chatbots can replace real-life communication — and take over the world.

#BionicManDiary, entry 008: The one where I contemplate the jobs of the future
Evgeny Chereshnev, professional cyborg, talks about fascinating new jobs that will emerge in the near future.

The dark side of facial recognition technology
Lynch law, loss of basic privacy, disgusting marketing, digital identity theft — how else can facial recognition be misused?

Facial recognition gets interesting — and useful
Catching criminals, waking up a sleepy driver, stopping teens from buying cigarettes — facial recognition can help us accomplish all that and more.

Flying Internet: who needs it and why
Facebook launched Aquila, a solar-powered drone which took its inaugural flight last week. Why does the social network need its own drones and how it is connected to the Google Loon project?

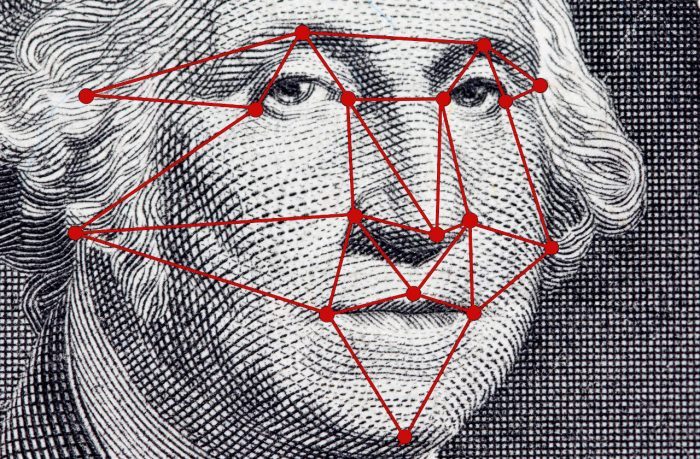
Man vs. machine: facial recognition
Accurate identification of people’s faces is a very human process but computers are gaining on our processing. A look at what’s going on now and what we’ll see soon.

You can’t replace your face, says face recognition
The Kaspersky Daily team checks if FindFace can really find users on a social media site with one image taken on the street and if it is possible to hide from it. Some interesting peculiarities detected!
Human trafficking: big data turned you and me into goods for sales
How everyone and his dog online make the big data tyranny raise.

What you need to know before switching to VPN
VPN’s features and pitfalls from legal and technical standpoint

Big data flaws we need to address
Big data is amazing for sure, but as any other tech, especially emerging one, it has issues. Let’s take a look what could possibly go wrong with big data implementations.

What are virtual SIM cards and what do they do?
Apple SIM, Google Project Fi and, for example, GigSky are all virtual SIM cards. OK, what’s so virtual about them?

VPN implementations and their peculiarities
We have previously discussed what VPN is. Now let’s review its implementations and their advantages and drawbacks.

eSIM: what is it for?
The next step in SIM cards evolution is not about squeezing them into even more miniscule form factor, it’s about replacing them at all — with a profile stored in connected device.

#BionicManDiary entry 006: Evgeny Chereshnev talks Internet of Us at Campus Party Brazil
Our bionic man Evgeny Chereshnev talks on the biochip in his hand and how it makes you a part of the Internet of Things

What exactly is VPN?
What exactly is a VPN? There has been a lot of buzz around it, but why do we need it?

Mobile fingerprint sensors: more or less secure?
Vendors claim, that a fingerprint sensor in your smartphone is user-friendly and really secure. But it’s not true.

The evolution of the SIM card
Observing the evolution the good old SIM card went through and the results so far

Quantum computers: what does it mean for you today?
Quantum computers are said to be coming soon. They will definitely change the information security paradigm. How you can prepare to this shift?

Clavis Aurea, or Does the “Golden Key” actually solve encryption issues
People encrypt their communications so strongly that governments cannot access it when there is a need. Is it really bad?
 privacy
privacy apple
apple BionicManDiary
BionicManDiary 3d printing
3d printing Aquila
Aquila 4G
4G biometrics
biometrics