The idea of using an app to control your car remotely sounds very appealing. Is it freezing outside? Just start the engine while you’re still lying under a blanket, and by the time you leave the house, your car will be toasty. If, on the contrary, it’s hot out, you can start the engine and get the AC running. And you no longer have to remember where you parked — the car will always provide you with its GPS coordinates through the mobile app.
Sounds tempting, which is why more and more car models support control by mobile app. But is it safe? Kaspersky Lab experts conducted a two-stage study to understand this particular aspect of security.
Researching the security of connected car apps
The first stage of the study took place at the end of 2016. Then, at the RSA Conference in February 2017, antivirus analysts Mikhail Kuzin and Viktor Chebyshev presented a report called Mobile apps and stealing a connected car. The experts analyzed Android apps that let users remotely control connected cars: unlocking doors, starting the engine, finding cars on a map, viewing dashboard readings, and so on.
Our experts analyzed nine mobile apps from the largest car manufacturers, testing their protection. Their goal was to evaluate if these apps are protected from three typical kinds of attacks used by malicious Android apps: gaining root permissions on the device (rooting), overlaying the app interface with a fake window, and injecting malicious code into legitimate connected car app.
First, let us understand what makes these attacks dangerous.

Potential attack vectors
Rooting
In standard operating mode, all Android apps store data, including valuable data such as logins, passwords, and other information, in isolated sections of memory that other apps cannot access. Rooting disrupts this security mechanism: With root access, a malicious app can gain access to data stored by other apps and steal it.
Many types of malware take advantage of this. About 30% of the most common Android malware can use vulnerabilities in the OS to root devices. In addition, many users make the job easier for viruses and root their Android devices themselves — something we do not recommend doing unless you are 100% sure that you know how to protect your rooted smartphone or tablet.
App interface overlay
This devious trick works very simply. Malware keeps track of apps as the user opens them, and the moment the user starts an app familiar to the malware, it overlays the app’s window with its own similar-looking (or even identical) window. The process is instantaneous, so the user has no chance of noticing something suspicious.
Then, as the user enters information into the fake window, thinking he or she is interacting with a trusted app, the malware steals logins, passwords, credit card numbers, and other information of interest to the hackers.
The app interface overlay trick is included in the standard arsenal of mobile banking Trojans. But the word “banking” no longer necessarily applies: The creators of these Trojans have far exceeded collecting data only in mobile banking apps, and they now create fake windows for a large number of other apps in which users enter credit card numbers or other interesting information.
The list of imitated apps is very long: various payment systems and popular messaging apps, apps for buying plane tickets and booking rooms, the Google Play store and Android Pay, apps for paying fines, and many others. Recently, the creators of one such Trojan started stealing payment information from taxi service apps.
Malware introduction
Hackers can also take a legitimate app, figure out how it works, inject malicious code into it while preserving the functions of the original app, and spread it through Google Play or other channels (in particular, using malicious ads on Google AdSense).
To prevent them from using this trick, app developers have to make sure that reverse-engineering their apps and injecting malicious code into them is as time-consuming — and therefore unprofitable — as possible. Developers use well-known techniques to strengthen their apps; in a perfect world, all developers would use them in developing any apps that work with sensitive user data, but unfortunately, in the real world, they don’t always do so.
Main threat
Using the aforementioned methods, malicious apps can steal user logins and passwords or PIN codes, as well as a vehicle’s unique vehicle identification number (VIN), which is all that’s required for authentication in the app.
Once the criminals obtain that data, all they need to do is install the corresponding app on their own smartphone, at which point they will be able to unlock doors (all apps have this feature) or even start the engine (not all of the apps allow this, but it is pretty common) and steal the car, or track the car owner’s movements.
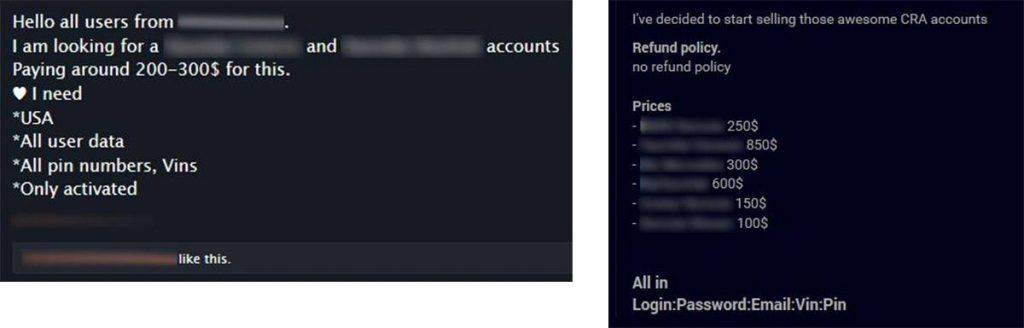
The threat has gone beyond theory and into practice. Darknet forums periodically feature ads for selling and buying real user account information for connected car apps. The prices for such data are surprisingly high — a lot more than criminals typically pay for stolen credit card information.
Cybercriminals respond quickly to new opportunities to earn money, so widespread use of malware attacking connected car apps is only a matter of time.
Part 1: 9 connected car apps, 0 protected against malware
When the first part of the research was published, early in 2017, experts had checked nine Android connected car apps developed by the largest manufacturers’ cars, and found that none of these apps were protected from any of the aforementioned threats.
Once again: All nine apps we studied were vulnerable to all of the most common attacks.
Kaspersky Lab experts naturally contacted the corresponding automotive manufacturers and told them about the problems before publishing the results.
Part 2: 13 connected car apps, 1 protected against (some) malware
It’s always interesting to see how events develop. Thus, a few days ago, Mikhail Kuzin presented the second part of the report at IAA 2017, the International motor show in Frankfurt.
The expert added another four apps to the list and examined them all, testing 13 programs in total. Only one of the new apps was protected — and against only one of the three types of attack (if it detects that the phone has been rooted, it refuses to operate).
Worse: The new inspection showed that all nine of the original apps were still vulnerable. In the months they’ve known about the problem, developers haven’t fixed anything. Moreover, some of these apps were not updated at all.
Unfortunately, auto manufacturers, despite all their knowledge and talents at building cars, still do not have the experience required to implement cybersecurity properly.
They’re not alone. This problem is typical of manufacturers of other smart and connected electronics. With cars, though, the issue feels more urgent and serious; hacks could cause losses in the tens of thousands of dollars, or even put someone’s life at risk.
Luckily, cybersecurity expertise doesn’t have to be learned in-house, and you don’t have to make all of the same mistakes to get it. We’re happy to work with automotive manufacturers and help solve problems with apps and other digital things.
Anyone worried about their smartphone becoming accessible to malefactors should install reliable protection on their phone to detect and block malware before it intercepts important information.
 connected cars
connected cars

 Tips
Tips