At the end of March a previously undocumented ransomware strain started making rounds; experts codenamed it CryptXXX. It has little to do with “adult” themes, although the ransom it demands is really “grown-up” – Bitcoins worth $500. It claims to be using a strong encryption algorithm, but Kaspersky Lab has already fixed up the cure.
Greedy
CryptXXX is being pushed via the notorious Angler exploit kit. It adds .crypt extension to all encrypted files, which makes it instantly recognizable, and drops three files – de_crypt_readme.bmp (an image file), de_crypt_readme.txt and de_crypt_readme.html. These files display typically intimidating messages of the “all-your-files-belong-to-us” kind and instructions for contacting the criminals and paying ransom. Victims are notified that the encryption algorithm used is RSA4096 (a strong one), so abandon any hope and pay up. Victims are even given their personal IDs and provided with links where they can acquire Bitcoin if they have no any.
The encryption process itself doesn’t start instantly; ransomware “gets to work” in a couple of hours or so after the initial infection, so that users wouldn’t find out which site “served” the cryptor. Also worth mentioning that CryptXXX not just encrypts the files but also steals bitcoins kept on victims’ hard drives and copies other data, which can be useful for the greedy guys that cybercriminals are.
Not just greedy but overly boastful too: it appeared that the vaunted RSA4096 algorithm just isn’t there. At our side we have prepared a decryption tool: the RannohDecryptor utility which was initially created to decrypt files affected by Rannoh ransomware, can be used to crack CryptXXX too.
#Alert We've got a #decryptor for those infected with #CryptXXX #Ransomware #infosec https://t.co/MTtTKQom79 pic.twitter.com/N56Wof2BZY
— Kaspersky (@kaspersky) April 25, 2016
Saving it
To recover the files at least one original (not encrypted) file is required. If you have more files like this backed up, this will work.
Then you need to do the following:
- Download the tool and launch it.
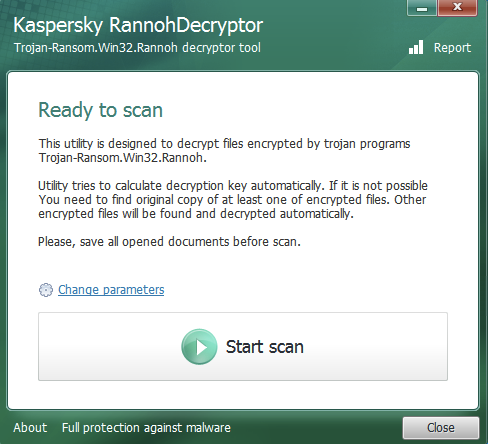
- Open Settings and choose drive types (removable, network or hard drive) for scanning. Don’t check the “Delete crypted files after decryption” option until you are 100% that decrypted files open properly.
- Click the “Start scan” link and choose where the encrypted .crypt file lies (that file, for which you have an unencrypted copy as well).
Then the tool will ask for the original file. - After that RannohDecryptor starts searching for all other files with “.crypt” extension and tries to decrypt all files, which weigh less than your original. The bigger file you’ve feed to the utility — the more files would be decrypted.
Users of Kaspersky Lab solutions are further protected because the Angler Exploit Kit used by the CryptXXX ransomware is detected in the early stages of infection by the Automatic Exploit Prevention technology in Kaspersky Lab solutions.
Businesses are threatened as well
Ransomware is mostly the end-user’s problem. However, businesses get hit too, and hit hard. Especially smaller companies where every employee is an “admin on its own”, as the external expert isn’t yet affordable. A successful ransomware attack can drive an entire company out of business.
Besides, there is a new threat looming: server-side ransomware has been already identified (see our yesterday post), with a large number of entities becoming victims already.
Some strains of ransomware can be decrypted; but where CryptXXX and some others fail, the likes of more advanced and dangerous Teslacrypt prevail, and you never know what you would be dealing with tomorrow. The proper approach here is prevention, not remediation.
Following rules are most basic, but also most efficient:
- Regularly make backups.
- Don’t hesitate installing all critical updates for your OS and browsers. Angler and other exploit kits used to deliver cryptors, leverage software vulnerabilities to download and install the ransomware.
- Install a proper security solution. Kaspersky Lab offers a number of solutions tailored for businesses of all sizes, providing a necessary multilayered protection from known and unknown threats.
Also we’d like to recommend the new column by the head of the global research and analysis team Kaspersky Lab USA Ryan Narain about how to avoid falling victim to ransomware.
We also would like to offer our Practical Guide “Could Your Business Survive A Cryptor”. In order to acquire your copy of the practical guide, kindly fill out the form below.
 decryption tool
decryption tool

 Tips
Tips