Kaspersky Lab experts have discovered a new APT campaign that targets government institutions, mainly in the APAC region. It was named “Hellsing” after the string containing the project directory name found within the attack components’ code.

To penetrate the target infrastructure, cybercriminals used a spear phishing attack (targeted e-mails with spoofed sender e-mail address) containing malicious documents. Embedded in the letter file was an exploit targeting vulnerabilities on the targeted user’s software; once opened, it installed a backdoor that allowed attackers take control of a workstation.
Deny the #HellsingAPT by default
Tweet
APT attacks based on a thorough preliminary study of targeted systems and real-time operator co-ordination pose a very special level of danger. Governmental agencies handling highly sensitive information (often including huge volumes of citizens’ personal data) are targets of choice for cybercriminals. Yet according to Global IT Corporate Security Risks Survey, 73% of organizations do not think they are being specifically targeted by cybercriminals[i]. It’s a dangerous delusion; regulatory compliance is an obvious requirement, but it’s also important to pay particular attention to protecting IT infrastructures against this type of attack, preferably by deploying additional proactive defenses.
A well thought-out deployment of Default Deny scenario is vital for a truly comprehensive counter-APT strategy. According to Kaspersky Lab’s vision, such strategy includes both network-based and endpoint-based elements, with allowlist-based technologies playing key roles. Over-cautious as this may seem, the reality is that there are still attack scenarios where typical Anti-APTs are powerless.
Therefore extra endpoint-based multiple security layers are to be considered, which would be efficient against previously unknown malware components.
Art of Default Denying an APT
During the analysis of “Hellsing”, we highlight common characteristics that are present in the APT scenario.
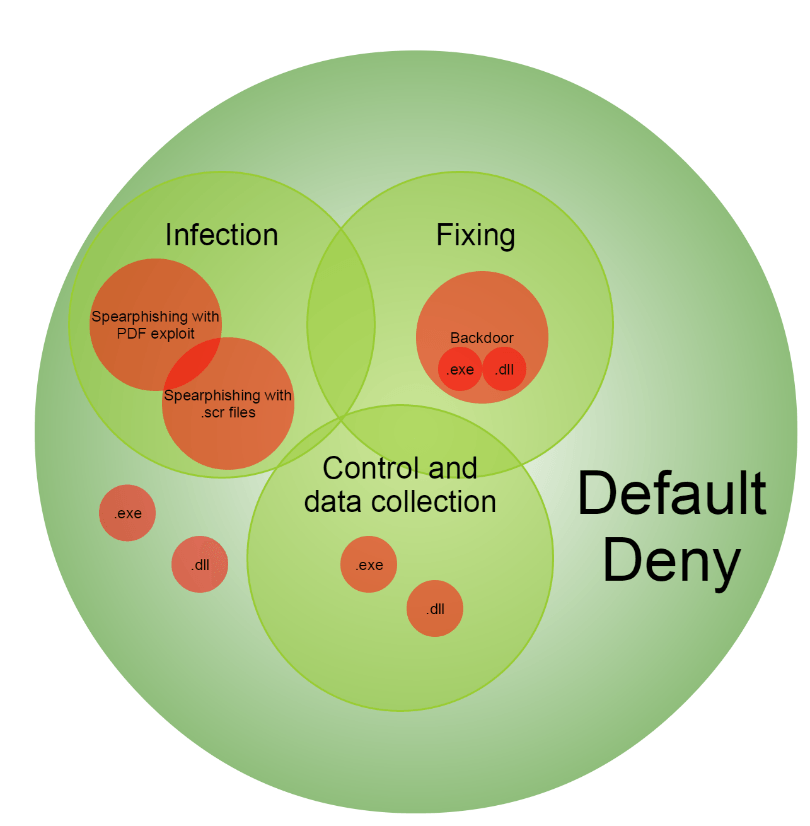
At the stage of “infection” attackers use various techniques for delivering malicious code to the victim’s operating system: sending emails containing the exploit; delivery of malicious code through social engineering, etc. The ultimate goal of these attacks: to deliver the backdoor to the victim’s operating system and run it. “Payload” is an executable (.exe) file or library (.dll), containing malicious code. In Hellsing’s case, the attacker uses social engineering to dupe the user into launching an exe-file from RAR-archive. The exe-file extension was replaced with an innocuous one and the victim did not notice the suspicious file.
A”Default Deny” scenario provides highly effective, proactive protection, even in instances where the cybercriminal somehow (e.g. using social engineering and duping the user into disabling her anti-virus) managed to deliver the malicious payload to their victim’s system.
The concept of “default deny” is not new, but it’s still effective against advanced threats with custom-made components – often the case with APTs. For example, if malicious exe-files or dll-libraries are successfully delivered to the victim, Default Deny would not allow their execution in the operating system environment because such files are not contained in a list of authorized, safe applications. Default Deny excludes all options to start executable code.
The next phase of the attack involves collecting information from the operating system, which may result in an escalation of privileges, the installation of a backdoor or additional modules. As a rule in such instances, executable files and dynamic libraries are being used. But if they are not a part of the trusted environment, Default Deny will not allow them to run.
Powerful yet cost-effective
Besides additional benefits including greater IT network stability, and lower maintenance time, consider this: deployment of an allowlist-based solution is considered one of the TOP4 strategies that can mitigate 85% of existing APT-related risks. The Default Deny scenario is the safest known variant of such an approach.
Compared with many standalone solutions for Default Deny implementation, even greater cost and operative efficiency can be achieved through the deployment of a truly integrated endpoint protection system that includes Default Deny capability.
It’s worth the effort
While the implementation of a Default Deny scenario is often considered too complicated for an average business, for government institutions dealing with extremely sensitive data, the effort is likely to reap rewards – not least because of the already highly regulated nature of government work processes. Kaspersky Lab’s convenient implementation tools (including pre-implementation test mode for compiled policies and our dynamic allowlists system), mean the process doesn’t have to be too taxing.
Default Deny mode and dynamic allowlists are parts of Application Control technologies, which are available in Kaspersky Endpoint Security for Business (“Select” and “Advanced” tiers), Kaspersky Total Security for Business and Kaspersky Security for Virtualization.
The organization and maintenance of a trusted environment in which the executable components of an APT would have no chance, is invaluable. In most cases, it would prevent attackers from achieving their goals.
Currently all components of “Hellsing” APT are blocked by all Kaspersky Lab solutions. To check your system for malicious software components we recommend start full scan of your systems. You can also use our free solution – Kaspersky Virus Removal Tool.
[i] Conducted in 2014 by Kaspersky Lab in conjunction with B2B International
 APT
APT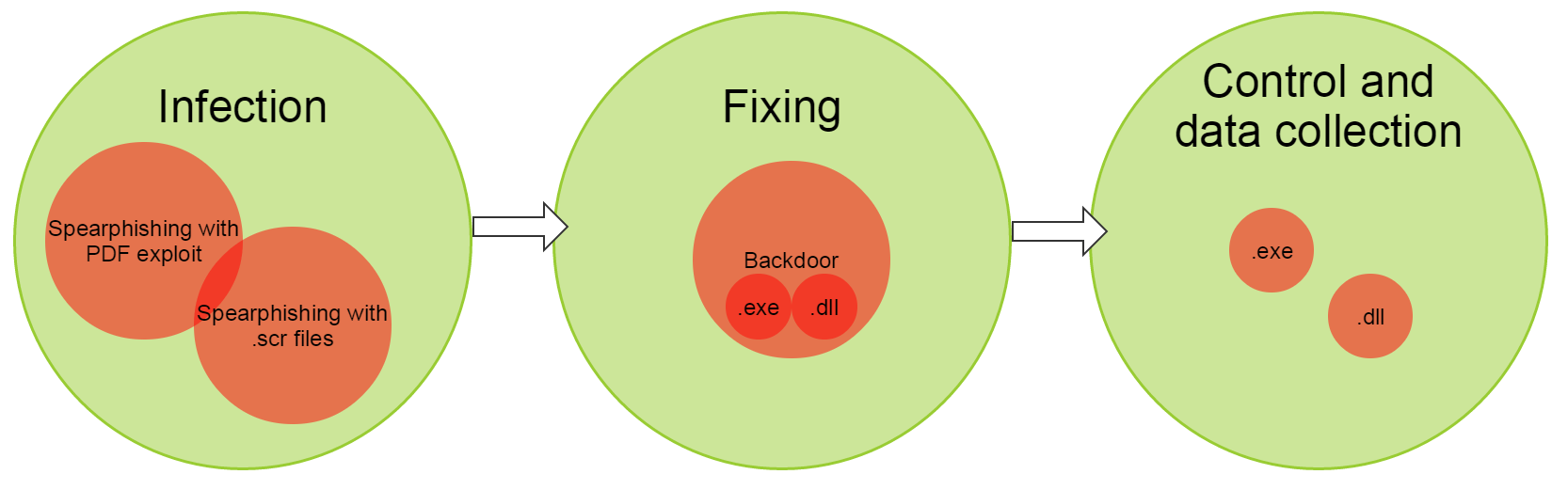

 Tips
Tips