Habits are easy to form and hard to break in all facets of life, including technology usage. Sometimes a user’s habits may not seem so harmful, at least from their employer’s point of view. Our Support Team sometimes tells us stories about how employees “technology dependencies” and employers’ views appear to be contradicting (or, rather, incompatible). We’d like to share one of those stories, without judgments, just the issue and solution.
One of our clients is a mid-sized company with 50+ employees, roughly half of which are very mobile; some work from home, meaning they have a “distributed” infrastructure and are BYOD enabled.
This company uses our Kaspersky Endpoint Security for Business, so every employee’s PC and mobile device has client information installed on it.
The problem was rather simple: in order to send and receive working files – sometimes pretty large ones, well exceeding the limits set by the company’s e-mail server – employees commonly used Dropbox and Google Drive, i.e. third party file hosting services. And that’s something company bosses frowned upon, viewing this as a potential risk to the company’s data.
And, to be honest, they had at least some reasons to view Dropbox and other such services that way.
Last year, Jacob Williams, a pen tester and top-notch digital forensic scientist, held a keynote at Black Hat EU on “how cloud based synchronization solutions in general, and Dropbox in particular, can be used as a vector for delivering malware to an internal network.”
In a short description of his presentation, available here, Williams noted there had been some theoretical research papers that identified the possible risk that cloud backup solutions may pose for data exfiltration. He has shown that – theoretically – such services can indeed be used maliciously. In other words, Dropbox, SkyDrive, Google Drive and other such services are, according to Williams, a possible threat.
Our own Global Emergency Response Team researchers often see how malware slips into corporate networks via shared file hosting services.
Tweet
That might sound like a “fear mongering theory”, but the “practice” is in place: a nasty malware using Google Drive; then there are Chinese “Comment Crew” that used publicly shared Dropbox folders to spread malware, then there is a handful of phishing scams of cloned Dropbox or Google Drive login pages, etc.
A simple Google search – “google drive skydrive dropbox malware” – returns a disturbing picture.
Our own Global Emergency Response Team researchers often see how malware slips into corporate networks via shared file hosting services. In late 2012, our experts had to deal with cascading attacks against shared access resources; as a result, large networks were compromised, with one company losing its e-mail for a few days (large amounts of data stored externally were lost as well).
But let’s get back to our main story. At some point, the company’s bosses advised their employees against using Dropbox and Google Drive when sharing any sensitive data. Employees complied, but they still had services client software installed on their machines and kept using them for “non-sensitive” items- for their own personal use. Until one day one of the employees made a mistake and shared some important documents publicly.
Fortunately, no disaster occurred; in fifteen minutes or so the file was removed, and apparently never fell into the wrong hands. But the company executives decided it was time for a crackdown.
Kaspersky Endpoint Security has a feature named Web Control that restricts the usage of certain web resources. Features like this are commonly used to block corporate employees from visiting “prohibited” resources, like porn, gambling, online shopping, etc. Sometimes it is also used to block banners, anonymous proxy servers, web mail or even social networks if they take away too much of employees working time.
Admins can block certain resources via their URLs, or let Kaspersky Endpoint Security analyze HTTP content and identify its category and/or data type automatically. Then the rules are applied according to settings.
This link goes to a Youtube video showcasing all of the Endpoint Controls in our solution, specifically detailing Web Control features. The entire video is available below.
There is also one more video overviewing the Web Control component in Kaspersky Endpoint Security:
And here is a detailed description of Web Control settings (this is an older version, but the interface has changed very little).
 So while there is no specific category for “web-based file hosting service” in the list, system administrators can block specific addresses – https://www.dropbox.com/, https://onedrive.live.com/, https://drive.google.com/. This can also be (and should be) combined with appropriate settings from the Application Control feature, so that in a BYOD case, employees would be unable to launch client applications for these services, while the device in use is accounted for within the corporate network. So it will make no sense to use these file hosting services during the day to share any working files – even if they come from outside the corporate network, they won’t be available for download.
So while there is no specific category for “web-based file hosting service” in the list, system administrators can block specific addresses – https://www.dropbox.com/, https://onedrive.live.com/, https://drive.google.com/. This can also be (and should be) combined with appropriate settings from the Application Control feature, so that in a BYOD case, employees would be unable to launch client applications for these services, while the device in use is accounted for within the corporate network. So it will make no sense to use these file hosting services during the day to share any working files – even if they come from outside the corporate network, they won’t be available for download.
It may be a harsh and unpopular measure, but – unsurprisingly – a risk to lose any important data over the file hosting service seems to be much more dangerous for company executives.
By the way, after blocking out Dropbox and other similar services, the company leased its own cloud, ensuring it’s protection. But that’s a different story.
 security
security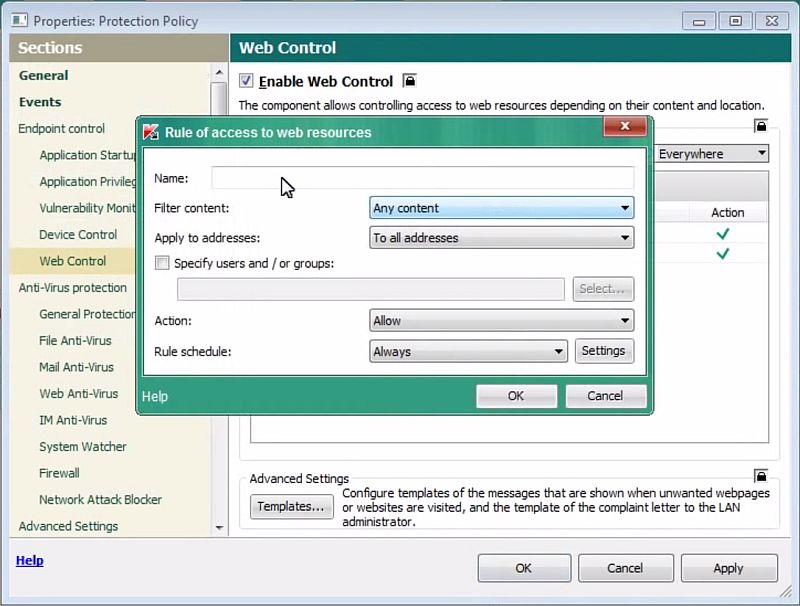

 Tips
Tips