Do you know the weakest link in the security chain that protects your personal data, banking files and other kinds of critical information? It’s you. For years there was one great threat that no security system could truly stand against: the human factor.
Nowadays, IT pros from security departments answer the question of what to allow and disallow: prohibit too much and employees will start to ignore rules or they will not be able to work efficiently. Give them too much freedom and you risk critical corporate information and their precious personal files draining away at data signaling speed.
Leave your passwords at the Checkout Desk:
"Do Not Disturb" Does Not Apply to In-room tablets https://t.co/ev0AwZ3W1D (by @dimitribest)— Fabio Assolini (@assolini) October 23, 2014
There will never be a balance until we learn that we are responsible for the data leakages that we cause. Every time you enter your personal account information from an unknown device, and leave the session open, your data becomes vulnerable. Sometimes it can be crucial information. For example, your Apple ID and Google Wallet may be connected to your credit card. Unfortunately, only a few of us think about this when we use our mobile devices.
@dimitribest found tons of #personaldata from previous guests on a hotel’s in-room iPad
Tweet
Let’s talk about a real situation that happened to one of our GReAT experts, Dmitry Bestuzhev.
 Among other alluring services, many hotels also offer free tablets to their customers (airports and restaurants have similar options as well). Guests often use them with pleasure; they figure why not browse through the latest updates on Facebook, check iMessages, e-mail or Google for news and recent arrivals in the Play Store, make a video call or do whatever else people do on the Internet to relax and unwind.
Among other alluring services, many hotels also offer free tablets to their customers (airports and restaurants have similar options as well). Guests often use them with pleasure; they figure why not browse through the latest updates on Facebook, check iMessages, e-mail or Google for news and recent arrivals in the Play Store, make a video call or do whatever else people do on the Internet to relax and unwind.
Dmitry also found a free iPad in his room. He explored the device and was very surprised: the tablet was filled with the private information of previous guests who had stayed in the room before.
You don’t need to be an IT ninja in order to gather the data saved on that iPad, which kept accounts with pre-saved passwords, authorized sessions on social networks, search results from the browser (including queries for pornographic content among other things), full contact lists automatically saved into the address book, iMessages and even a pregnancy calculator.
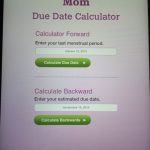 It was not difficult to find out who this careless lady-in-waiting was as she also kindly left her personal contact information on the device. Most sessions were still open meaning that one could easily post or send messages posed as one of these people. Just imagine: an imposter could write nasty messages to your boss or colleagues.
It was not difficult to find out who this careless lady-in-waiting was as she also kindly left her personal contact information on the device. Most sessions were still open meaning that one could easily post or send messages posed as one of these people. Just imagine: an imposter could write nasty messages to your boss or colleagues.
Dmitry spent some time Googling and found out that some of the previous visitors were also people who work for the government. If anybody used their data to access their corporate information, it would mean a serious data leak.
 It is indeed easy to bring to life a similar scenario for data theft. A malefactor could come into the room before you check-in and install apps that track your passwords and other info. After that, s/he would have a wide range of possibilities at his disposal: blackmail the victim, publish inappropriate photos on the web (do you remember the leaked photos of Jennifer Lawrence?), download a few music files from iTunes at your expense or anything else.
It is indeed easy to bring to life a similar scenario for data theft. A malefactor could come into the room before you check-in and install apps that track your passwords and other info. After that, s/he would have a wide range of possibilities at his disposal: blackmail the victim, publish inappropriate photos on the web (do you remember the leaked photos of Jennifer Lawrence?), download a few music files from iTunes at your expense or anything else.
So don’t be so careless. To keep your personal data safe, follow these simple rules. First: always use strong passwords. Second: connect only to reliable and secure Wi-Fi networks. Third: use only your own devices when you are working with personal information (and nowadays that means always). In short, public devices are the worst — so never use them.
How to remember strong, unique passwords https://t.co/wUk4D4vw4f pic.twitter.com/C9K2ZMjQwS
— Eugene Kaspersky (@e_kaspersky) October 20, 2014
 leaks
leaks

 Tips
Tips