The security of smart devices is a hot topic. We can find articles about how hackers and researchers find vulnerabilities in, for example cars, refrigerators, hotels or home alarm systems. All of these things go under the term IoT (Internet of Things), and it’s one of the most “hyped” topics in the industry. The only problem with this kind of research is that we cannot really relate to it all. I started to think about this topic, and figured that if we can’t secure ourselves against current threats, what good will it do to identify potential new future threats? A typical modern home can have around five devices connected to the local network which aren’t computers, tablets or cellphones. I’m talking about devices such as a smart TV, printer, game console, network storage device and some kind of media player/satellite receiver.
A typical modern home can have around 5 connected devices, which aren’t computers or cellphones. Most of them are susceptible to hack.
Tweet
I decided to start a research project, trying to identify how easy it would be to hack my own home. Are the devices connected to my network vulnerable? What could an attacker actually do if these devices were compromised? Is my home ‘hackable’? Before I started my research, I was pretty sure that my home was pretty secure; I mean, I’ve been working in the security industry for over 15 years, and I’m quite paranoid when it comes to applying security patches, etc. I reckoned there must be other homes that are much more hackable than mine, because I don’t really have a lot of ‘hi-tech’ things at home.
During my research I didn’t focus on computers, tablets or cellphones, but rather on all the other devices I have connected to my network at home. To my surprise it turns out that I actually have quite a lot of different things connected to my network. Most of them were home entertainment devices: smart TV, satellite receiver, DVD/Blu-ray player, network storage devices and gaming consoles. I’m also at the moment relocating to a new house, and I’ve been talking with my local security company. They’re suggesting I get the latest alarm system, which connects to the network and can be controlled with my mobile device… After this research, I’m not so sure it’s a good idea.
Some of the devices on my network were for example:
- Network-attached storage (NAS) from famous vendor #1
- NAS from famous vendor #2
- Smart TV
- Satellite receiver
- Router from my ISP
- Printer
To consider a “hack” successful, one of the following should be achieved:
- To obtain access to the device; for example, to get access to files on the network storage devices;
- To obtain administrative access to the device;
- To be able to transform/modify the device for my personal interest (backdoor, etc.).
Before conducting the research I had all devices update with the latest firmware version. During this process I also noticed that not all devices had automated update systems, which made the entire process quite tedious. Another interesting observation was that most of the products were discontinued more than a year back or simply didn’t even have any updates available.
The hack
After researching the network storage devices I found over 14 vulnerabilities that would allow an attacker to remotely be able to execute system commands with the highest administrative privileges. The two devices did not just have a vulnerable web interface, but the local security on the devices was also very poor. The devices had very weak passwords, a lot of configuration files had incorrect permissions, and they also contained passwords in clear text. More details on the device hacks are available in the longer Securelist version of this post.
During the research project, I stumbled upon some other devices that had ‘hidden’ features; one of those devices was my DSL router, which was provided by my ISP. I found that there were tons of functions I didn’t have access to. I just assume that my ISP or the vendor have FULL CONTROL over the device, and can do anything they want with it and access all these functions I don’t have permission to use. By just looking at the ‘hidden’ function names it seems that the ISP can for example create tunnels so as to connect to any device on the network. Just imagine if these functions fell into the hands of the wrong people? I understand that these functions are most likely supposed to be helping the ISP perform support functions, but when you log in using the administrative account you don’t have full control over what you consider is your own device, and thus it becomes quite scary. Especially when some of the names have equally scary names like ‘Web Cameras’, ‘Telephony Expert Configure’, ‘Access Control’, ‘WAN-Sensing’ and ‘Update’.
I’m currently still researching these things to see what the functions really do. If I find anything interesting I’m pretty sure there’ll be another blog post.
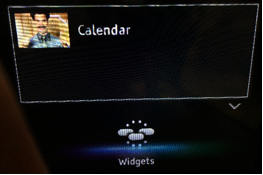
To hack my Smart TV and media playing devices, I had to get creative. I had to play with the idea that I’m the attacker, and I’ve already compromised the two network storage devices, and so what can I do next?’ The media players are most likely reading information from the storage devices (which I’d already compromised). At this point I was researching potential code execution vulnerabilities with the smart TV and DVD player, but due to the high price I paid for the devices I wasn’t able to investigate this further. It wasn’t only a question of the wasted money if I were to break my brand new LED smart TV, but also I had no idea of how I would explain my wrecking the telly to the kids; how were they going to watch Scooby Doo? However, I did identify one curious security issue with the Smart TV. When the user accesses the main setup menu on the TV, all the thumbnails and widgets get downloaded from the vendor’s servers if the device has network access. The TV didn’t use any kind of authentication or encryption when it was downloading the content, which means that an attacker could perform a man-in-the-middle attack on the TV and modify the images in the administrative interface; the attacker could also have the TV load any JavaScript file, which isn’t a good thing. A potential attack vector is to use JavaScript to read local files from the device, and use the content of the files to find even more vulnerabilities. But this is something I’m working on with the vendor to see if it’s possible or not. As a proof of concept for my attack, I changed the thumbnail of a widget to a picture of everyone’s favorite, Borat. Yakshemash!
The conclusion
This post doesn’t name specific TV, NAS or DSL router vendors on purpose. The goal of my research is not to brag about all the undiscovered vulnerabilities I found, or that there are big security problems in the home entertainment product line. There will always be vulnerabilities, and we need to understand that; however, by understanding I don’t mean accepting. We need to actually do something about it; we need to know what the impact is and assume that our devices can be, or are already, compromised. We need to start assuming that products are vulnerable and that attackers can and will gain access to them.
I would like to conclude this research by saying that we as individuals and also companies need to understand the risks with network devices. We also need to understand that our information is not secure just because we have a strong password or are running some protection against malicious code. We also need to understand that there are so many things that we do not have control over, and that we are largely in the hands of the software and hardware vendors. It took me less than 20 minutes to find and verify extremely serious vulnerabilities in a device considered to be secure – a device we trust and on which we store all the information we don’t want stolen.
We need to come up with alternative solutions that can help individuals and companies improve their security. This is not a problem you simply can fix by installing a product or security patch; therefore, I would like to end this post by saying that even though the home entertainment industry might not be focused on security, we at KL do, and with just a few simple tips I think we can raise the security level a little bit higher. Hopefully some of the vendors will read this research and improve their software security; but until then, here are some simple tips from my side:
- Make sure all your devices are up to date with all the latest security and firmware updates. This is a problem for a lot of home, business and entertainment devices, but it is still the best thing you can do to avoid being at the mercy of known vulnerabilities. It also gives you an indication of whether the devices have any updates at all to install, or if it’s considered to be a ‘dead’ product.
- Make sure that the default username and password are changed; this is the first thing an attacker will try when attempting to compromise your device. Remember that even if it’s a ‘stupid’ product such as a satellite receiver or a network hard drive, the administrative interfaces are often vulnerable to serious vulnerabilities.
- Use encryption, even on the files you store in your network storage device. If you do not have access to an encryption tool, you can simply put your files in a password-protected ZIP file; it’s still better than not doing anything at all.
- Most home routers and switches have the possibility to set up several different DMZ/VLAN. This means that you can setup your own ‘private’ network for your network devices, which will restrict network access to and from this device.
- Use common sense and understand that everything can be hacked, even your hardware devices.
If you’re really paranoid you can always monitor the outbound network traffic from these devices to see if there’s anything strange going on, but this does require some technical knowledge. Another good tip is to restrict network devices from accessing sites they’re not supposed to access, and only allow them to pull updates and nothing else.
 GReAT
GReAT


 Tips
Tips