A rather naïve belief many blockchain enthusiasts share is that code backed by blockchain fabric is self-sufficient. “Code is Law,” as they say. Unfortunately, reality has already proved this maxim wrong, because, well, code is written by people, and people are prone to making mistakes. Even when machines write code, it’s still likely to contain flaws: For example, the exploitation of the DAO smart contract eventually led to a hard fork of Ethereum Classic from Ethereum. This sort of trouble has happened more than once and with more than one blockchain.
https://twitter.com/CoinbasePro/status/758158060355551232
Problems are not limited to code flaws. From an information security perspective, blockchain systems — including nodes and wallets — are just software. And the people who use this software have a tendency to fall for social-engineering tricks. Some problems, such as the use of phishing to steal coins from wallets , can be solved with security software on the consumer side. Others cannot, such as people believing scammers who promise ROIs of hundreds of percent and then disappear.
Initial coin offerings (ICOs) remain popular among startups raising funds; the number of token sales is higher than it was back in 2017. At the same time, fraud did not diminish as crypto prices did. One estimate has losses from last year totaling $1.7 billion, up 400% from 2017 — the record-setting year for amount of single-incident losses. The most notable example, vulnerabilities in the Parity Wallet, resulted first in a loss of $30 million worth of Ethereum and then to the locking out of $154 million worth of Ethereum tokens by the removal of their data from the blockchain.
It got worse. In 2018, about $950 million was lost to theft from crypto exchanges and wallets, and another $750 million was lost as a result of fraudulent ICOs or token sales, exchange hacks, and other schemes. It’s no wonder regulators are catching up. The stance of such financial authorities as the US Securities and Exchange Commission is that tokens, especially those that assume the receipt of profits from the startup that organizes the sales of its tokens, should be treated as financial securities with all that implies, including criminal prosecution if things go south for investors (buyers of tokens). That is true as well for an STO (secondary token offering), so if you consider token sales a means to boost your business, we suggest you start thinking of selling tokens the way you would think about issuing securities. That means, stop a moment and think about security (pun intended).
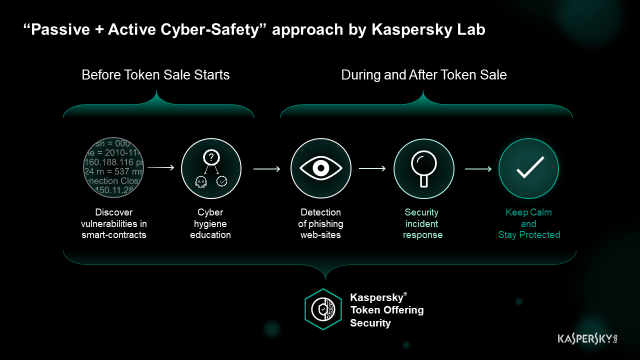
The four major areas of risk for token sales: smart-contract vulnerabilities, staff wrongdoings, phishing attacks on investors, and operations security.
Smart-contract vulnerabilities
The lousiness of smart-contract writers is inexplicable. Estimates of several years ago claimed smart-contract code contained about six times as many bugs as commercial code. Based on 2018 stats, the situation seemingly has not improved.
From our perspective dealing with software flaws for more than two decades, studying smart contracts is actually quite similar to conducting application security testing. Sometimes it’s even simpler, because smart contracts are written in script language before compilation. There’s nothing new under the sun, really — you can see for yourself that most of the top mistakes people make have been long known in the “regular” software world. For example, recursive empty calls that led to DAO heist and subsequent Ethereum hard fork, or improper access control, as with Parity Wallet, are considered rookie mistakes in the world of information security.
It takes an attentive (and experienced) eye to look at the code sometimes, so don’t be too proud to ask an expert for a smart-contract review before you commit the code to blockchain — you will not be able to roll back any subsequent changes.
Staff wrongdoings
You might be expecting a traditional rant about humans being the weakest link in cybersecurity, but that’s not my point here. Instead, I want to focus on a goal of transforming employees into a “human firewall” through effort and dedication to improving cyberhygiene. In fact, we’ve seen that in some organizations the number of incidents dropped 90% after our training.
Phishing attacks
Fame never comes alone, and once your ICO gains traction, you can assume phishing scammers will follow. Sometimes, as our analysis has shown, phishing sites pop up even before the official ones do. While it’s hard to take down phishing sites that target the buyers of tokens, you can still detect them and notify your current and potential investors. It’s better to have good fame than bad, right?
Operations security
For companies operating in the financial securities market, incident response capability and employee training are not luxuries; they’re absolute necessities. You may push the tasks off, figuring you’ll deal with them later, if regulators ever impose more restrictions. Well, in cybersecurity, you have to think “when,” not “if” — and add one important consideration: Assume an incident has already happened. That mindset will pay off in more ways than one, and what helps your reputation among investors today (you are helping them prevent losses, remember?) will save you from being slapped with fines — and, possibly, criminal charges — tomorrow.
You can learn more about solutions for ICOs and STOs here.
 BlockChain
BlockChain

 Tips
Tips