The Christmas and New Year holidays, alas, were not a pretext for any real decrease in the number of information security incidents, as experts and users continue to face malware attacks with varying levels of quality and sophistication.
Browser botnet
In the middle of December there were news reports on the Advanced Power botnet, powered by Firefox add-ons. This zombie network comprises about 12,500 Windows machines. The bots are spread via a phony add-on called the Microsoft .NET Framework Assistant.
The Advanced Power botmasters used compromised Windows machines as a scanning platform for websites vulnerable to SQL injection attacks. The botnet automated this probing, which is generally a time-consuming manual process.
White Flag
The day before Christmas Eve, Microsoft declared the major ZeroAccess/Sirefef botnet dead. The botnet’s primary function was to hijack search results, redirecting users to malicious websites hosting information stealing malware, amongst other threats to commit click fraud. ZeroAccess demonstrated a proclivity for Bitcoin mining. The botnet was quite large and included some two million infected machines.
Microsoft, Europol, the FBI and the application networking and security firm A10 Networks cooperated on disrupting ZeroAccess and wrestling control of its click-fraud activities. But the takeover did not impair the peer-to-peer botnet’s communication protocol. In 24 hours, the attackers were able to issue new configuration commands to bots under their control and resume operations. However, German police joined the effort and were able to monitor this activity, identify and track down the new IP addresses used in the fraud schemes under the new configuration.
As a result, the bot-herders released one additional update to the infected computers that included the message ‘WHITE FLAG’ and stopped trying to release new code in the botnet. Microsoft reported victory, but some experts believe that the botmasters simply decided to lay low until the hype died down, only to resume their activities later.
Onerous advertising
Since New Year’s Eve, Yahoo.com visitors have gotten an unexpected surprise: advertisements that targeted their systems with malware.
It turned out that the attack advertisements served by ads.yahoo.com used iFrames to hide malicious scripts. If users clicked on the advertisement, they were redirected to a site that hosted the Magnitude exploit kit, which then attempted to exploit any Java vulnerabilities present on their system to install malware including the infamous Trojans ZeuS, Dorkbot/Ngrbot, Andromeda and several other programs of the kind.
The exact number of victims is unknown, tens of thousands may have been affected. Most users targeted by the malicious advertisements were in Romania, the United Kingdom, and France.
More information here
Another ransomware
A new extortionist blocker program, under the names PrisonLocker and PowerLocker, was reported in the late 2013. At the moment, it appears to lack a completed graphical user interface and is still undergoing quality assurance tests. Once it’s ready, the creator claims he will sell the malware for roughly $100 per license, which can be paid using the cryptocurrency Bitcoin.
PrisonLocker is written in C++ and drops a single executable file into a temp folder. Following successful installation, PrisonLocker is designed to encrypt nearly every file on infected machines, including those on hard drives and shared drives but excluding .exe, .dll, .sys, and other system files.
As with CryptoLocker, infected users will be given a predetermined amount of time to pay the ransom before the decryption key is forever deleted. Whoever administers the ransomware will have the ability to choose the preset amount of time and pause or reset this deletion clock in order to examine ransom payments, and determine the ransom amount and method of payment.
More information here
Ice fog with coffee flavor
Kaspersky Lab announced the detection of a new branch of the cyber espionage campaign Icefog.
The point is the emergence of new spyware tools are referenced as Javafog. The attackers use malicious JAR-file to infect computers, and there is even a large independent oil and gas company from the USA that fell victim.
The details are available here.
Critical patch for ragged OS
Last week Microsoft released four security bulletins. The update MS14-002 is of special interest because it addresses a zero day vulnerability in Windows XP and Windows Server 2003.
The vulnerabilities in the “ancient” but still actively used Microsoft products were made public in early November, along with their exploits for targeted attacks.
The exploits are spread via infected PDF attachments. They work only in conjunction with an Adobe Reader vulnerability that has since been patched.
This must be the last or one of the final updates for Windows XP by Microsoft. Microsoft will end support for XP in April. This year Windows XP will celebrate its 13th anniversary.
Memory issues
Adobe has issued security bulletins addressing five critical vulnerabilities in its Flash, AIR, Reader and Acrobat Players that could give attackers the ability to cause crashes and take control of affected machines.
CVE-2014-0491 (security bypass) and CVE-2014-0492 (memory leak bypassing address space randomization) resolve problems in Adobe Flash and AIR. CVE-2014-0493 and CVE-2014-0495 resolve memory corruption vulnerabilities that could lead to code execution. CVE-2014-0496 resolves a use-after-free vulnerability that could lead to code execution.
No exploits for these vulnerabilities have yet been detected.
How did you get there?
The hacker groups named European Cyber Army and 1775Sec declared a break into Apple’s database and proved their announcement by publishing the personal data of hundreds of registered Apple users on the Web. Soon after, however, there were doubts about the authenticity and/or up-to-datedness of the data. Many phone numbers in the document turned out to be out of service which suggests possible data forgery.
If the data was actually obtained from Apple’s servers, the matter is how anyone managed to get in there at all.
Details are here.
Syrian Electronic Army again
The Syrian Electronic Army excelled once again. On January 1st, the Syrian Electronic Army obtained access to the official Skype blog, Facebook and Twitter accounts, and posted an appeal to never use Microsoft Outlook (the former Hotmail service) because Microsoft sells users’ details to U.S. authorities.
Then the group took control of the @XboxSupport Twitter account which redirected users to the official website of SEA.
This was followed by some of the Microsoft employees’ social-networking accounts hacked. Microsoft also confirmed that some e-mail accounts were also compromised. The company stated that the number of hacked accounts was negligible. Their owners yielded to banal phishing.
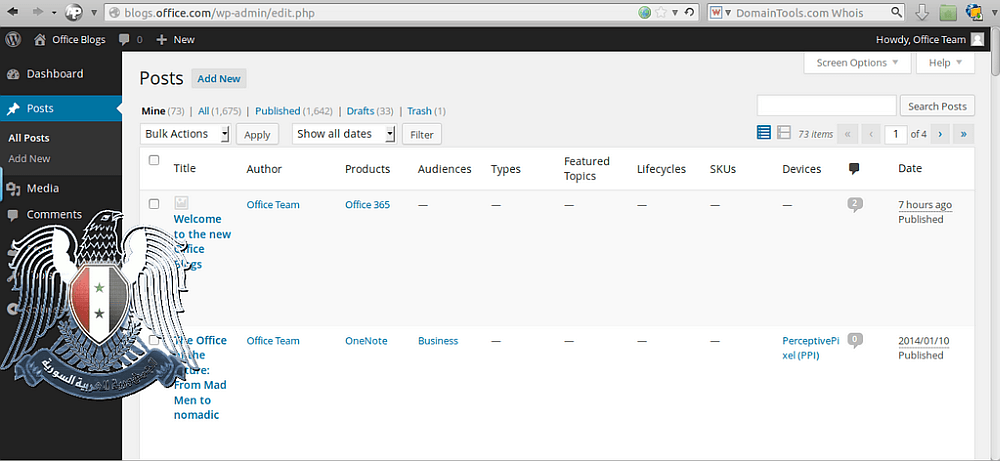
The official Twitter of SEA plainly declared that the attack at Microsoft was not over yet, and soon intrusion into Microsoft Office official blogs would follow. SEA published several screenshots of the blogs allegedly compromised administration panel: apparently Microsoft used WordPress CMS.
 security news
security news


 Tips
Tips