Kaspersky Lab experts unveiled new Linux-targeting malware related to the infamous Turla APT.
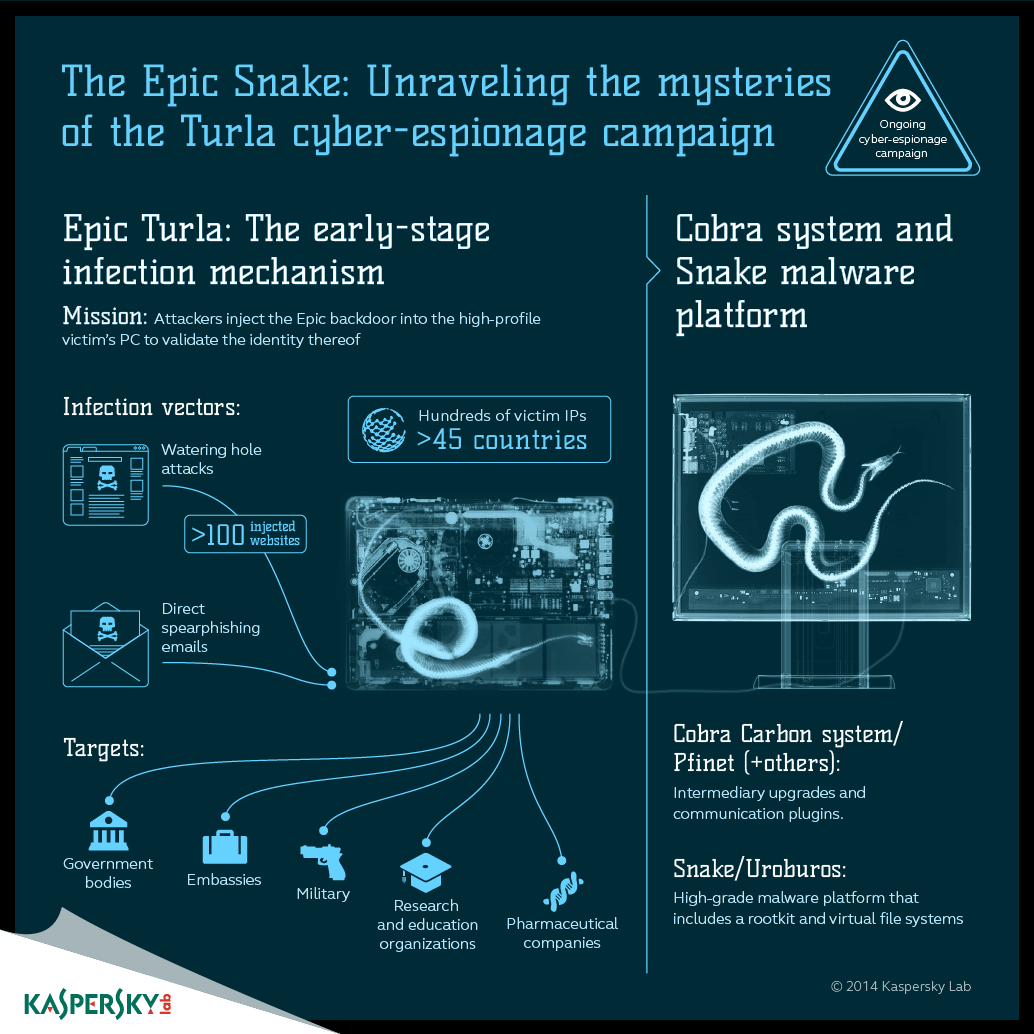
Epic Turla (aka Uroburos, Snake, etc.) is considered one of the most complex APTs in the world. Analysis on it was published earlier this year (see Securelist and Kaspersky Business blog for details), and the newly discovered malware seems to be the “previously unknown piece of a larger puzzle”, according to Kurt Baumgartner and Costin Raiu.
All previously known “pieces” were targeting the Microsoft Windows family, both 32 and 64 bit, using zeroday vulnerabilities in Microsoft and Adobe products, and the appropriate backdoors. A Linux component was suspected, although it hadn’t been observed in the wild. Until now.
No penguin left behind: #EpicTurla #APT’s #Linux component discovered
Tweet
The attacks committed in the course of the Epic Turla campaign are very sophisticated. It employs multistage infections, with a number of backdoors, keyloggers, rootkits, and other malicious tools deployed into the compromised systems consecutively.
The most interesting point is the initial vector. Epic Turla uses relatively “mundane” methods. An attack scenario against a given business would look like this: First, a spearphishing e-mail is sent, crafted well enough to ensure it’s going to be opened and the malicious payload activated. The e-mail is sent to the right person (previously identified by the attackers), it has industry (and situation) relevant headers – as does the attached document – and the spoofed source looks credible.
Then there are waterhole attacks – and social engineering – used to lure the victims to compromised websites. Needless to say, compromising those sites is a separate activity, which requires some effort. This shows how thorough the actors behind the Epic Turla campaign are.
The attackers are also notoriously dynamic in using exploits or different methods depending on what is available at the moment. Today, they may send you a spearphish and the next day you’re prompted to download a fake Flash Player, etc.
Once they are in, the compromised system is served with a backdoor, then a keylogger. If attackers find their target is indeed of interest to them, a more advanced and sophisticated backdoor from the Carbon/Cobra family is installed – again, in several stages (a detailed description is available here).
Now, the Linux component – the so-called “Penquin” Turla. Why is it there if Epic Turla is mostly Windows oriented?
The most likely answers are the most obvious. First, Linux is widely used on servers. And taking over a server means securing a nearly perfect spot to intercept the data of interest.
Also, Linux-based endpoints are common in government organizations worldwide – both in developing and developed countries – and government organizations are the primary targets for Epic Turla.
Windows, Linux… How many more systems #EpicTurla attacks?
Tweet
Now the troubling part: According to Securelist, “Penquin” Turla is a stealth backdoor which doesn’t require “elevated privileges” – i.e. any administrative or root rights from the user. Even if a user with limited access to the system launches it, the backdoor can intercept incoming packets and run commands on the system incoming from the attackers while maintaining stealth. It is also rather hard to uncover, so if this thing slithers its way into the servers, it may be sitting tight and low indefinitely – depending on when the compromised system’s operators check the machine for more exotic threats.
The question now is: How many more Epic Turla malware variants are out there undiscovered? What might they target, and what can potential victims do to stop it from happening?
The technical tools capable of protecting your infrastructure from the “initial vector” attacks listed above – namely phishing and waterholing – do exist, but it is also utterly important that the employees are aware of these threats and know how to counter them too.
More data on Epic Turla campaign:
- Epic Operation Kicks Off Multistage Turla APT
- The Epic Turla Operation
- The ‘Penquin’ Turla: A Turla/Snake/Uroburos Malware for Linux
- Epic Turla – catching the reptile’s tail
 Cybersecurity
Cybersecurity


 Tips
Tips