Today is the second day of Kaspersky Security Analyst Summit 2014 – the security conference initiated by Kaspersky Lab, where our experts, security pros from other companies and independent researchers share their knowledge. One of today’s conference segments was devoted to online banking malware and the cybercriminal activity aimed directly at your bank account. The segment consisted of five presentations and covered various areas of the problem. Here’s a short recap.
Millions of users attacked
Sergey Golovanov, Kaspersky Lab’s security expert, provided specific data numbers. Although the prevalence of online banking scams varies from country to country, in total about 1.8 million of Kaspersky Lab’s clients were protected from this specific type of attacks in 2013.
Sergey Golovanov presenting at Security Analyst Summit 2014
One notable example of cybercriminal activity was the circumvention of a one-time-code security system available in Germany. Instead of trying to break the system itself, criminals employed a social engineering technique. They made victims think that there was an erroneous money transfer to their account. After that victims entered all the data, including a one-time confirmation code, to ‘return’ the money but, in fact, were sharing access to their own account.
Education is crucial in trying to lower the risk of online banking scams. This is one of the major takeaways from Sergey’s presentation. Businesses as well as consumer need to think about it. Even the most sophisticated banking system, with all security features and necessary limitations, can be circumvented by a social engineering technique.
Small, unique targeted banking malware

The next keynote was by Peter Kruse of the CSIS Security Group, presenting research on the Tinba banking malware: a highly sophisticated trojan targeting users mostly in the United Arab Emirates and Turkey. One of the specifics of the operation of this malware is that it changes the security settings of Internet Explorer, allowing insecure content to be displayed and thus enabling the possibility to alter the online banking webpages. It is written in assembly code and stores its numerous features in just 20 kilobytes.
Online malware goes offline
The curious case of the interaction between the online and offline world (and stealing people’s money in the process) was presented by Kaspersky Lab’s researchers Fabio Assolini and Santiago Pontirolli. The cybercriminal act targets a payment system named Boleto, which is very popular in Brazil.

Fabio Assolini presenting the research on Boleto attack
In order to pay for a service or transfer money, the user of Boleto goes to a website to generate and print the invoice. He or she then brings the invoice to a bank, where the money transfer is completed. Our researchers found evidence of an attack, which alters the contents of the printed invoice, so that, in the end, the money is sent to cybercriminals’ accounts instead of the true destination. All that cybercriminals must do is modify the number and the bar code of the invoice.
Mobile banking malware on the rise
Another presentation by Kaspersky Lab’s experts, Roman Unuchek and Anton Kivva, focused on mobile banking malware. There is no doubt that more and more interactions with your bank account are performed via a smartphone – using an assured app or some sort of SMS-based service. Does this activity attract cybercriminals? Until the last year the number of new banking trojans targeting Android devices was relatively low. But 2013 saw a major increase of cybercriminal activity in this field, which can be seen on this slide:
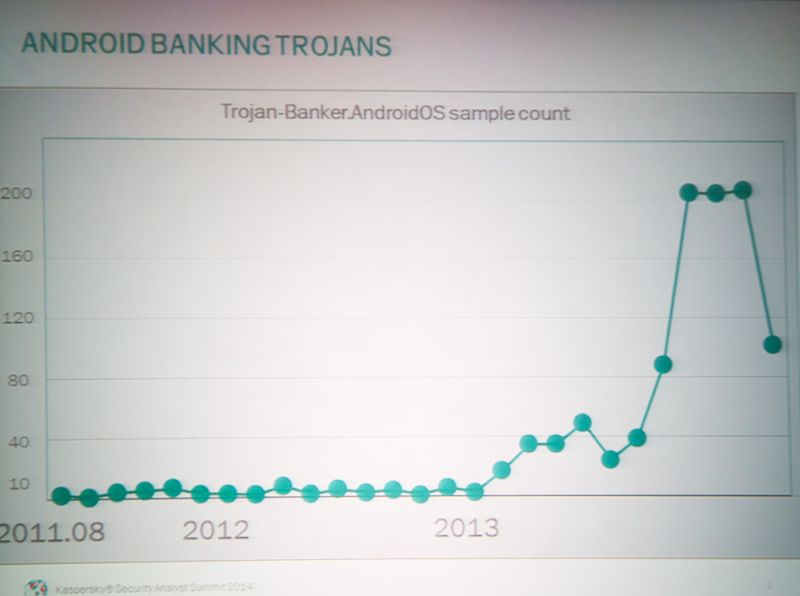
It is quite a significant increase. Keeping in mind that small businesses often rely on smartphones to process purchases made via credit or debit card, this trend is certainly alarming. Examples of mobile malware showed by Roman and Anton, however, targeted standard end user banking apps, often trying to steal access credentials.
The potential vulnerability of the Android ecosystem was later confirmed in the final presentation of this particular section, by independent researcher Colin Mulliner. He showed some examles of how legitimate apps can be modified and their functionality altered. What does this has to do with money? In a few examples, Colin explained how cybercriminals can overcome the authorization process of an in-app purchase mechanism.
Overall, the presentations on banking malware certainly show that online banking, both for end users and businesses is constantly being targeted by cybercriminals, with some of new “flavors” like mobile banking scams becoming more and more popular. In order to mitigate such risks, employee education and proper protection from malware, including integrated features like “Safe Money” in Kaspersky Small Office Security is certainly required.
 online banking
online banking

 Tips
Tips