A year ago I addressed cybersecurity specialists to let them know about a new tool we’d developed. Our Open Threat Intelligence Portal (OpenTIP) offers the same tools for analysis of complex threats (or merely suspicious files) as our GReAT cyberninjas use. And lots of other folks use them now too, testing zillions of files every month.
But a lot has changed in the past year, with practically the whole world having to work remotely because of coronavirus, which in turn makes life more difficult for cybersecurity experts. Maintaining the security of corporate networks has become a hundred times more troublesome. As precious as time was before COVID-19, it is even more dear now — and today, the request we get most from our more-sophisticated users is simple and direct: API access and higher rate limits.
You asked, and we delivered.
The new version of OpenTIP offers user registration, and I highly recommend regular visitors do register; a large chunk of the paid Threat Intelligence Portal appears when you do.
First, did you know you could use the API to send artifacts for testing? You can integrate OpenTIP into your analysis processes whichever way you find quick and convenient. In addition to unlimited quantities of files, you can also test other suspicious artifacts such as URLs, IPs, and hashes.
Second, for executable files, in addition to the verdict about which contents seem suspicious, OpenTIP now supplies more raw material for analysis, by which I mean not only data about the structure of PE files, but also text strings extracted from them. Our super cool cloud sandbox, which is actually a paid product in its own right, is also available. And finally, a “Private submission” button appears in the settings, permitting a check of artifacts without anyone knowing they were submitted to OpenTIP. From the start, we haven’t allowed anyone to view other’s files, but now it’s possible to keep tested portal indicators from the public history.
Even without registration, OpenTIP improvements will be noticeable.
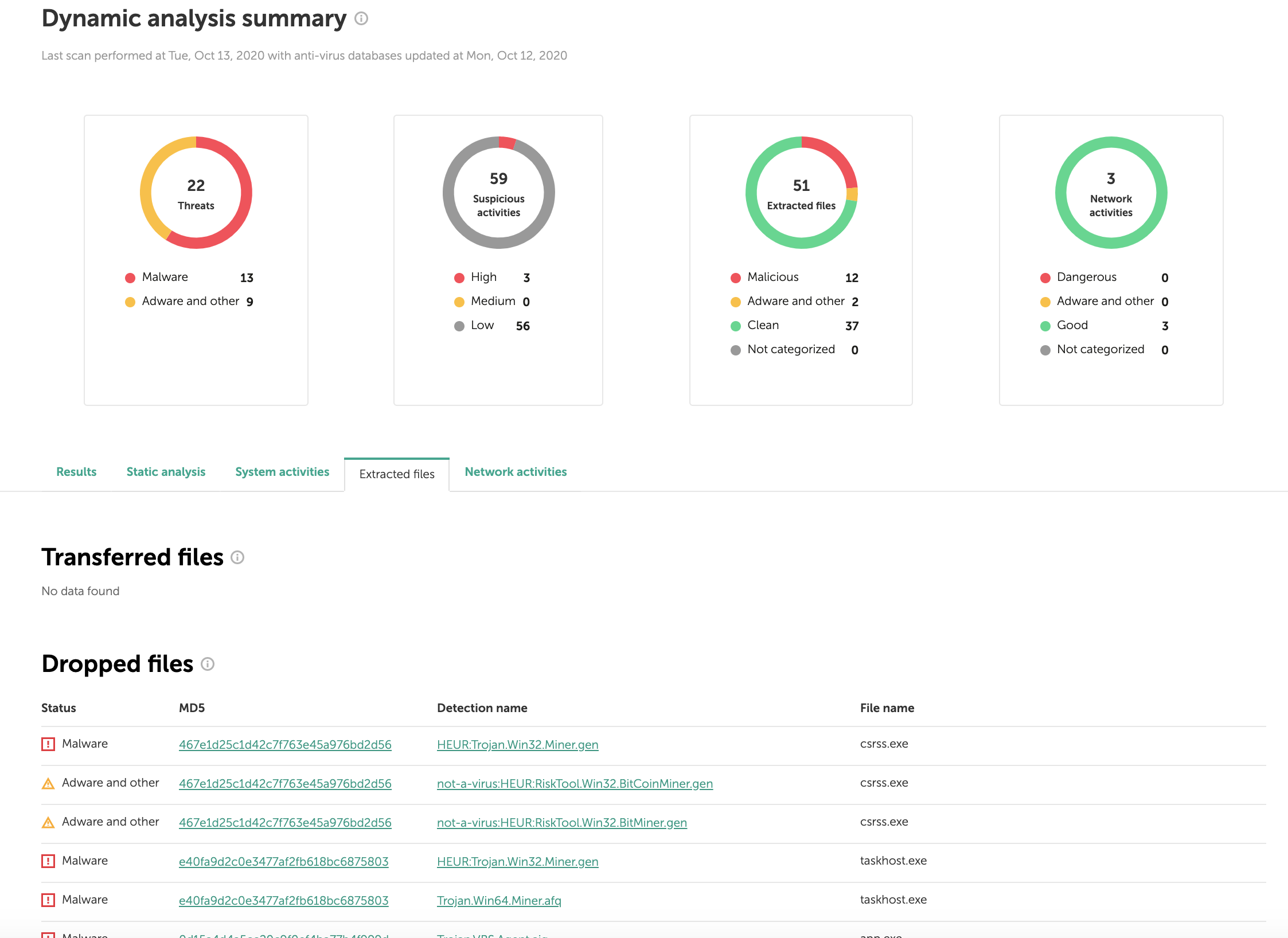
The Web interface is more convenient, time-saving, and easy on the eyes, and analysis results are much more informative.
We’ve also applied extra behavior analysis technologies in the second version of OpenTIP. You won’t get a simple “infected/clean” verdict, as with traditional endpoint protection, but rather a detailed analysis of suspicious properties, on the basis of which an analyst can decide whether to dig further. For suspicious URLs, categorization of dangerous properties will be available as well.
For those who need even more, the paid version of the Threat Intelligence Portal is much richer — in part because of the access to detailed reports on detected cyberthreats from our top analysts.
How to subscribe
Enough with the abstract descriptions: Why not stop reading and have a go for yourself? Simply throw a suspicious file at OpenTIP.
For those who haven’t yet subscribed to our Threat Intelligence services, I know you will find the portal indispensable (yes, I remember VirusTotal, but I talked about that last time). But most of all, OpenTIP will be indispensable to those who adapt it to their daily processes of analyzing all manner of cyber-nastiness.
 threat intelligence
threat intelligence


 Tips
Tips