In pursuit of business account credentials, cybercriminals are devising new ways to trick employees onto phishing sites. Previous spam campaigns have used SharePoint invitations and voice messages as bait.
Recently, our experts uncovered another phishing scheme in which cybercriminals try to mimic the performance appraisal process of the target company. The attack is twofold: Recipients think that the appraisal (a) is mandatory and (b) can lead to a pay raise. It’s worth noting that in some companies such appraisals are a routine part of the salary revision process and that’s why they don’t raise any suspicions.
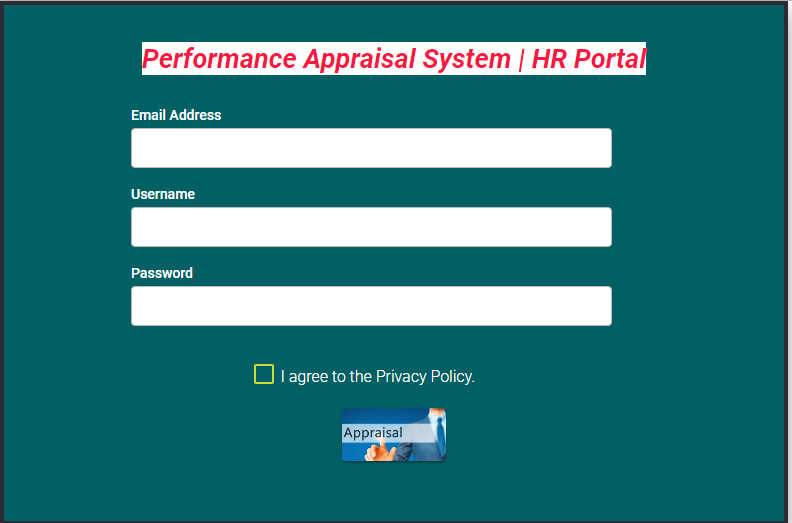
It all begins, as usual, with an e-mail. The employee receives a message that appears to be from HR, recommending a performance appraisal. The text of the message contains a link to a website with an “appraisal form” to be filled out.
Targeting the uninitiated
If the instructions are to be believed, the user must follow the link, log in, wait for an e-mail with additional details, and select one of three options. For anyone new to the company and its appraisal procedure, the sequence of steps might look convincing. Only the website address (which is unrelated to any corporate resources) could arouse suspicion.
If the employee opens the link, they will see an “HR portal” login page. Unlike many phishing resources meant to look like login pages for business services, this one looks quite primitive, with a bright monochrome or gradient background and data entry fields covering the page. For the sake of authenticity, the scammers invite the user to accept the privacy policy (without providing a link to any such document).
The victim is asked to enter their username, password, and e-mail address. In some cases, the scammers direct them to enter their work address. By clicking the Sign In or Appraisal button, the employee actually forwards the data to the cybercriminals.
At this point, the “appraisal” is likely to come to an abrupt end. The employee may wait a while — in vain — for the promised e-mail with further details to arrive. In the best-case scenario, they might suspect something is wrong, or send a kindly reminder to the real HR department, which will then notify IT security. Otherwise, the company might not detect the identity theft for months.
The dangers of corporate account hijacking
It all depends, of course, on what technologies the company in question deploys. Having obtained an employee’s credentials, the cybercriminal could commit mischief by, for example, sending targeted phishing e-mails in the victim’s name to other company employees, partners, or clients.
The attacker could also gain access to their correspondence or internal confidential documents, which increases the chances of a successful attack: Messages that appear to come from the victim are likely not only to bypass spam filters, but also to lull recipients into a false sense of security. Later, stolen information could also be used for various types of targeted attacks on the company itself, including business e-mail compromise (BEC).
Furthermore, internal documents and employee messages can be put to other uses as well, such as for blackmail or sale to competitors.
How to defend against phishing attacks
Such attacks primarily exploit the human factor. Therefore, it is vital to ensure that employees are familiar with the company’s cybersecurity procedures and processes.
- Issue regular reminders that employees should treat any links in e-mails with caution, opening them only if their authenticity is certain;
- Remind staff not to enter work account details on any outside website;
- Intercept phishing e-mails before they even get close to anyone’s inbox. For this, install a security solution at the mail server level. Kaspersky Security for Mail Server or Kaspersky Endpoint Security for Business Advanced will get the job done.
 spam
spam


 Tips
Tips