In June 2021, our specialists discovered new malware called PseudoManuscrypt. PseudoManuscrypt’s methods are fairly standard for spyware. It functions as a keylogger, gathers information about established VPN connections and saved passwords, steals clipboard contents, records sound using the built-in microphone (if the computer has one), and captures images. One variant can also steal the credentials of QQ and WeChat messengers, capture screen video and has a function that attempts disabling security solutions. Then it sends the data to the attackers’ server.
For the technical details of the attack and indicators of compromise, see our ICS CERT report.
Origin of the name
Our experts found some similarities between the new attack and the already known Manuscrypt campaign, but analysis revealed that a completely different actor, the APT41 group, had previously used part of the malware code in its attacks. We have yet to establish responsibility for the new attack, and for now we’re calling it PseudoManuscrypt.
How PseudoManuscrypt infects a system
Successful infection rests on a rather complex chain of events. The attack on a computer usually begins when the user downloads and executes a malware that imitates pirated install package for popular software.
You can find PseudoManuscrypt bait by searching the Internet for a pirated software. Websites that distribute malicious code matching popular queries rank high in search engine results, a metric attackers seem to monitor.
Here you can clearly see why there have been so many attempts to infect industrial systems. In addition to providing malware posing as popular software (such as office suites, security solutions, navigation systems, and 3D first-person shooters), the attackers also offer fake install packages for professional software, including certain utilities for interacting with programmable logic controllers (PLC) using the ModBus. The result: an abnormally high number of infected industrial control system (ICS) computers (7.2% of the total).
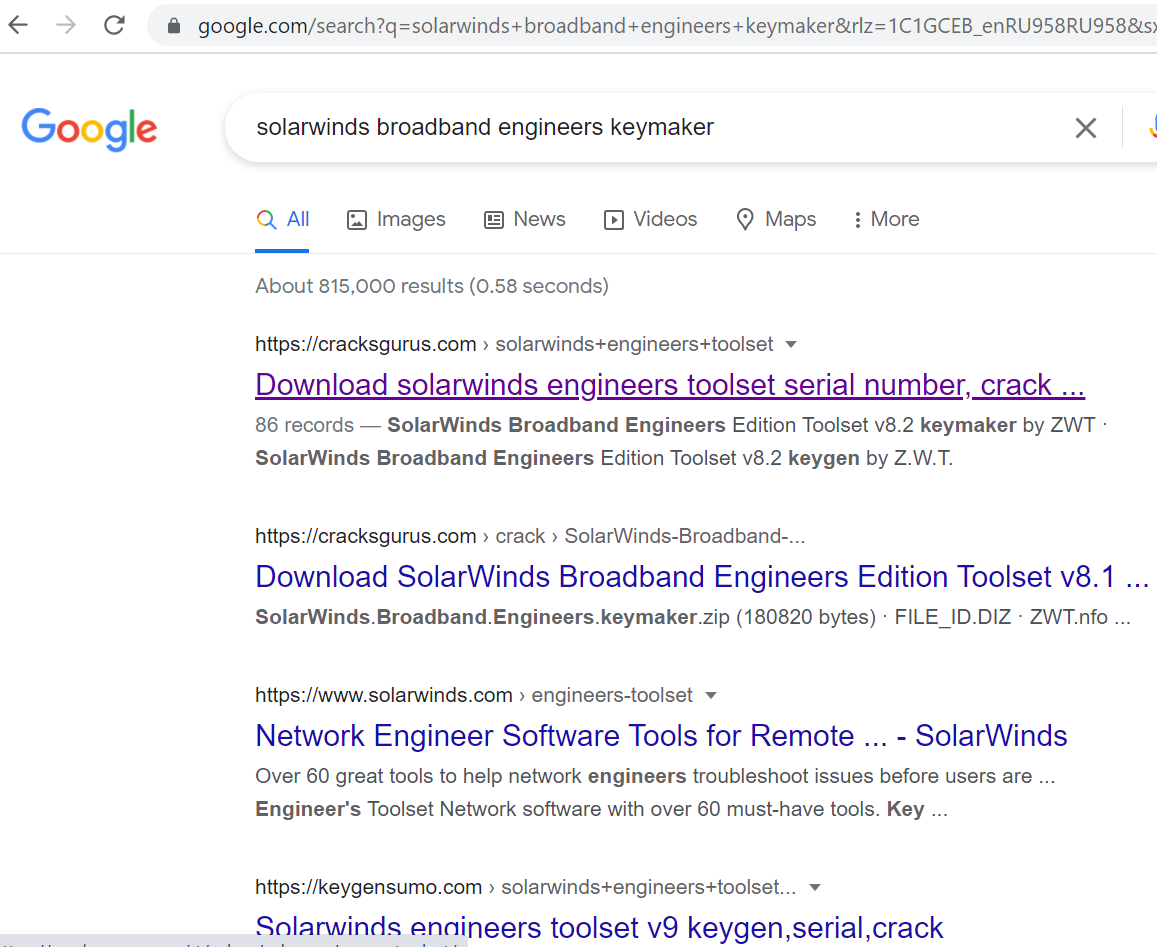
Search results for pirated software. PseudoManuscrypt can be found at the very first link. Sourse.
The example in the screenshot above features software for system administrators and network engineers. Theoretically such an attack vector could provide attackers with full access to the company’s infrastructure.
The attackers also use a Malware-as-a-Service (MaaS) delivery mechanism, paying other cybercriminals to distribute PseudoManuscrypt. That practice gave rise to an interesting feature our experts found when analyzing the MaaS platform: Sometimes PseudoManuscrypt was bundled with other malware that the victim installed as a single package. The purpose of PseudoManuscrypt is to spy, but other malicious programs seek other objectives, such as data encryption for money extortion.
Who is PseudoManuscrypt targeting?
The largest number of PseudoManuscrypt detections have occurred in Russia, India, Brazil, Vietnam, and Indonesia. Of the huge number of attempts to run malicious code, users at industrial organizations account for a significant share. Victims in this sector include managers of building automation systems, energy companies, manufacturers, construction companies, and even service providers for water treatment plants. In addition, an unusually large number of affected computers were involved in engineering processes, and in the production of new products in industrial companies.
Methods for defending against PseudoManuscrypt
For protection against PseudoManuscrypt you must have reliable and regularly updated protective solutions, and they must be installed on 100% of a company’s systems. In addition, we recommend instituting policies that make disabling protection difficult.
For IT systems in industry, we also offer a specialized solution, Kaspersky Industrial CyberSecurity, which both protects computers (including specialized ones) and monitors data transfers that use specific protocols.
Also keep in mind the importance of raising personnel awareness of cybersecurity risks. You can’t totally rule out the possibility of clever phishing attacks, but you can help staff stay alert, and also educate them about the danger of installing unauthorized (and especially pirated) software on computers with access to industrial systems.
 Industrial Cybersecurity
Industrial Cybersecurity

 Tips
Tips