Kaspersky Lab’s Q2 report on spam and phishing has arrived, and brought little surprises. As usual, spam is littered with Nigerian scams, emails meticulously reflecting major events in the world, malware (including some non-conventional things), and phishing attempts in the millions. Global internet portals, social networking sites and blogs, and banks make up the top three targets of the phishers.
Spam and phishing in Q2: spam percentage stopped decreasing #Q2
Tweet
In detail
An earthquake in Nepal, the presidential election in Nigeria, and the Olympics in Rio de Janeiro were the primary topics of scam letters in Q2. Just like any event extensively covered in mass media, these attracted a lot of fraudsters, who have no scruples when it comes to taking advantage of human tragedies like the Nepal earthquake.
These emails are mostly written in such a bad English that it’s hard to imagine anyone buys into it.
However, some amusing events also took place. One mass-mailed scam letter claimed that the newly elected President of Nigeria had arranged a $2,000,000 compensation for – pay attention! – “the countless fees that you have been sending to Nigeria which turns out to be scam” (sic!).
The letter goes on: “We are deeply serious (sic!) for what you have been through”.
Sorry, seriously couldn’t help posting this:

The next Olympic Games in Brazil will not be held until 2016, but Kaspersky Lab is already registering fraudulent notifications of lottery wins dedicated to this popular sporting event.
Interestingly, a large number of emails of this type were sent out in the run-up to the World Cup, while the Olympics were not mentioned.
The content of the messages is standard: the lottery was held by the official organization, the recipient’s address was randomly selected out of millions of email addresses, to receive the winnings it is necessary to respond to the email and provide the specified personal information.
This personal information is then “used appropriately” by the cybercriminals.
SEO spam spike
Yet another event exploited in spam in the second quarter of 2015 was the release of regular updates to the Google search algorithm. This changed the mobile web search results so that the sites adapted for mobile phones were displayed in top positions. And, of course, a significant increase in the amount of spam relating to SEO (search engine optimization) and promotion of sites took place. According to Securelist, spammers sent out offers advertising the creation of sites of any complexity and purpose, as well as services to attract new customers. They emphasized the necessity to bring the site up-to-date by using the latest features of a popular search engine. Those site owners who still had doubts were threatened with ending up in the last pages of Google search results and the resulting loss of potential customers.
Volume stats
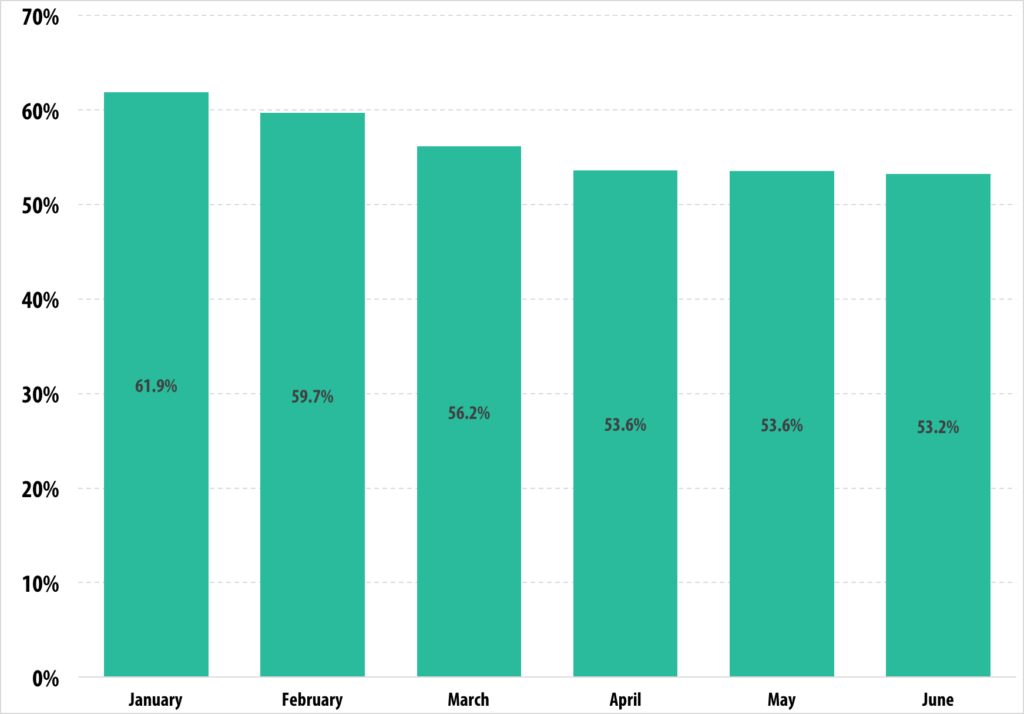
In comparison to Q1, the long-observed decrease in the spam percentage in email traffic seems to have stopped. From April through June the percentage remained basically the same: 53.6% in April down to 53.2% in June. As soon as figures of Q3 are in, there will most likely be some increase due to the fact that it’s the end of vacation period.
Malware
Arguably, the primary problem with the spam, aside from clogging the bandwidth, is the malware and phishing attempts it carries along with it.
In Q2, the notorious Trojan-Spy.HTML.Fraud.gen topped the ratings. This program is a fake HTML page which is sent via email, imitating an important notification from a large commercial bank, an online store, a software developer, etc. In other words, something that is very likely to be clicked.
This threat appears as an HTML phishing website where a user has to enter his personal data, which is then forwarded to cybercriminals.
Second and third positions are occupied by Trojan-Downloader.HTML.Agent.aax and Trojan-Downloader.HTML.Meta.as. Both are HTML pages which, when opened by users redirects them to a rigged site. Once there, a victim is usually faced with a phishing page or is offered a download – Binbot, a binary option trading bot. The two malicious programs spread via email attachments and the only difference between them is the link which redirects users to rigged sites.
Outside the Top 3 reside more harmful things: a Banker ChePro (Trojan-Banker.Win32.ChePro.ink), a downloader for specifc Trojans designed to steal confidential financial information.
Trojan-PSW.Win32.Fareit.auqm. Fareit Trojans steal browser cookies and passwords from FTP clients and email programs and then sends the data to a remote server run by the fraudsters.
Also, there are a couple of Trojan downloaders from Upatre family, and Exploit.MSWord.CVE-2014-1761.k, a Word document containing an exploit which uses an appropriate vulnerability to download to the victim’s computer other malicious programs designed to steal user personal data.
Upatre, by the way, also heads the Q2 rating of malware families.
The top 3 of those families also welcomes back ZeuS/Zbot multipurpose malware, most often used to steal banking information. It is also known to install Cryptolocker.
Among other highlights of Q2 is the continued presence of macro viruses in spam emails – albeit the peak was in the previous quarter.
The distribution of letters containing non-typical ARJ archives made with 1990s software also continued. Spammers seem to have loved other non-conventional archives too: April’s and May’s spam traffic distributed attached archives withCAB and ACE extensions, which are not common with today’s spam. The archives contained Trojan Trojan-Downloader.Win32.Cabby and HawkEye Keylogger. Unlike such popular spam extensions as ZIP and RAR, the CAB and ACE attachments may not always be recognized by users and thus cause less suspicion.
Phishing
Securelist says in Q2 2015, the Anti-Phishing system was triggered 30,807,071 times on computers of Kaspersky Lab users. 509,905 masks of phishing URLs were added to the Kaspersky Lab databases over this period.
Anti-Phishing system was triggered 30,807,071 times on computers of Kaspersky Lab users. #protectmybiz
Tweet
Primary targets of phishing attempts were Global Internet portals – their share even increased by 2.78 percentage points from the previous quarter and accounted for 42.35%. Other categories, in turn, were attacked slightly less often. “Social networking sites” lost 2.6 percentage points, “Banks” – 5.56 percentage points, E-payment systems – 2.84%.

These decreases don’t seem to be indicative of anything; just petty fluctuations, but the problems remain.
Full report is available on Securelist.
 malware
malware
 Tips
Tips