In the past few years, cybercriminals have changed tack considerably. Until just a few years ago, they typically sent out Trojans en masse and waited quietly for someone to pay up, knowing full well that most targets would ignore the demand. Now they appear to have adopted a different approach, becoming more client-centric, so to speak.
Attackers have switched from mass infections to targeted ones, undoubtedly reducing their coverage area and hence increasing their determination not to let anyone escape. Now every target represents a big prize, and cybercriminals are reaching for more levers of influence. Take, for example, a recent e-mail we came across while researching the cybercriminal group known as Darkside.
The crux of the matter
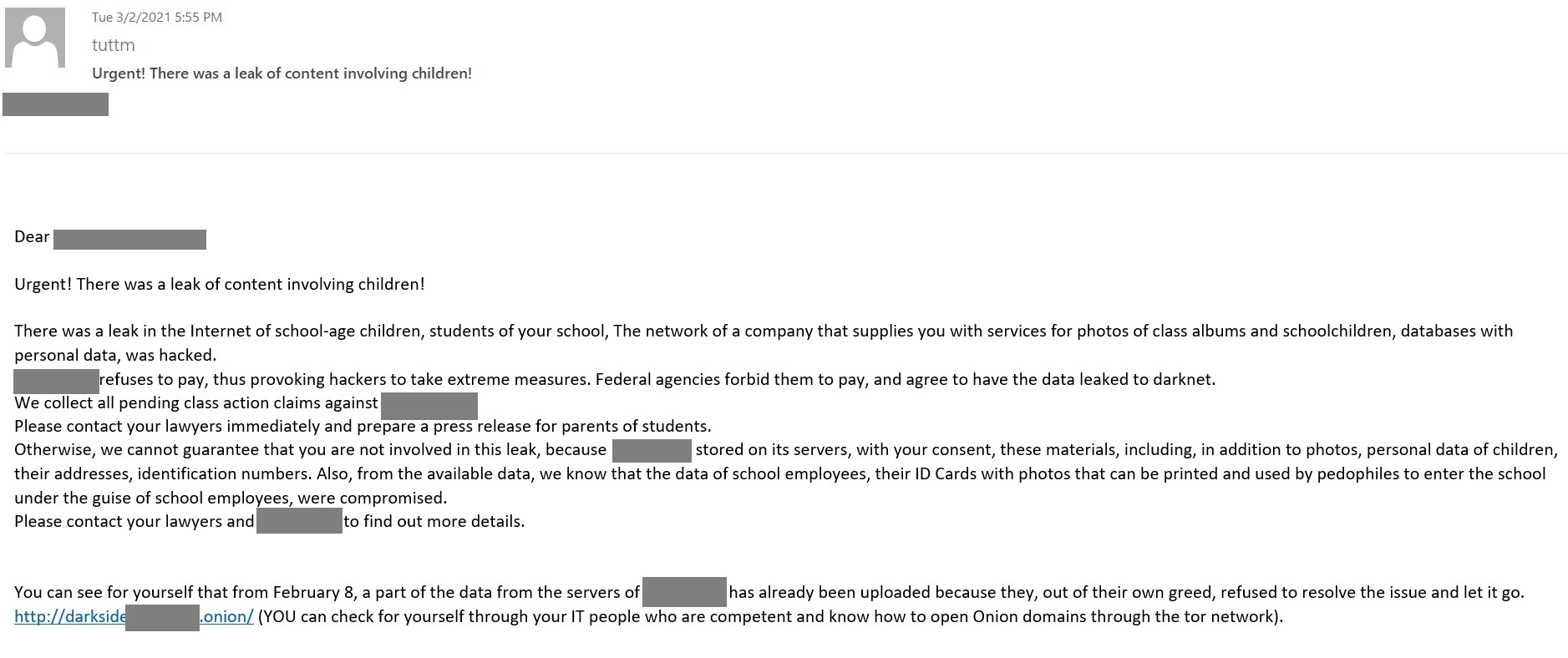
The e-mail essentially says that attackers infected an organization that supplies photography services for schools and therefore stores student and school employee data. It claims that federal authorities forbade the organization to pay the ransom, apparently forcing the aggrieved cybercriminals to bring additional leverage to bear.
Darkside’s mind games
The cybercriminals turned directly to the schools whose student data had been compromised, which were seeking to initiate as many class actions as possible against the affected company. The cybercriminals urged the schools to prepare press releases and contact students’ parents to explain the situation. Otherwise, they said, they could “not guarantee” that the school’s data, including children’s personal data, would not end up on the dark web. They also stressed that the data included employee photographs and details that could potentially help pedophiles to create fake school passes, thereby putting the children at greater risk.
Thus, the attackers threatened not only to ruin the victim’s reputation, but also to influence its clients and partners to cause additional damage through potentially devastating legal ramifications.
What to do
It is important to understand that, in reality, satisfying cybercriminals’ demands will not make the problem go away. You have no way of knowing whether they have actually deleted any stolen data, as Eugene Kaspersky pointed out recently.
Therefore, we advise all organizations and companies, but especially ones that store partner or client data, to prepare in advance for a possible attack:
- Explain the nature of the threat to all employees, and train them to recognize intruder actions;
- Equip all computers and devices with reliable security solutions that can defeat ransomware Trojans;
- Keep track of available software updates and install them regularly (ransomware attacks through vulnerabilities have been especially destructive of late).
 Ransomware
Ransomware