
Real Problems With Virtual Money
In recent years, cybercriminals have stepped up their efforts to get hold of users’ money. Credit card numbers, login details for online banking, passwords and codes – all this and
834 articles

In recent years, cybercriminals have stepped up their efforts to get hold of users’ money. Credit card numbers, login details for online banking, passwords and codes – all this and

In a three-month period this year, Kaspersky Lab products detected and prevented nearly 1.5 billion attempts to infect users’ computers. These included attacks on mobile devices and malware targeting Mac

Apple popularized the app-store concept and the iPhone and its companion store have gained a reputation for security over the years. While iOS on its own is quite secure, there

Cybercrime is a funny business. The common element in cybercrime operations is that attackers enjoy virtual anonymity and a low chance of detections. And like most kinds of thievery, it

Google’s Android operating system far and away dominates the mobile market with more than 68 percent of devices running the open source OS, according to research firm IDC. Whilst this

Hackers spent much of 2012 laying the groundwork for what they have in store for not only big business and strategic government and military targets, but consumers as well in

For users, the browser is the key to their online lives. It holds their histories, their secrets, tracks their movements and stores their passwords. So for attackers, the browser is

The reality is that, on the whole, security for gamers and gaming isn’t all that different than best practices for normal online, social networking activities. You need to maintain strong

It’s a common belief that Macs are safer than PCs because most computer viruses are designed to attack Windows machines and not Macs. Recent high-profile Mac-targeted viruses like MacDefender and
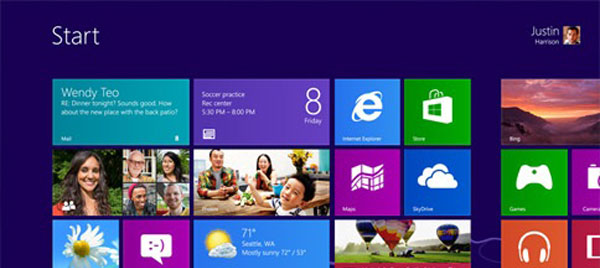
Windows 8 is being touted as a major change in the way that people will use and interact with their PCs, tablets and other devices. Much of the change is

In terms of security it’s not the one who has more talented programmers who creates the best protection. Instead, it’s often the one who’s been attacked the most who’s forced

Look at any one of the dozens of reports about cybercrime levels, and you’ll inevitably come away with the conclusion that online crime is getting worse by the day. And

The phrase targeted attack looks to be redundant at first glance. Of course an attack is targeted. What good would it be without a target? But the reality is that

A bug in the iPhone means that users shouldn’t necessarily trust that text messages they receive are coming from the phone numbers they claim to be sent from. According to

As you already know, Windows 8 has some major differences from Windows 7. In order to provide the best and most secure user experience, we created KIS2013 and KAV2013 modified