While investigating a cybersecurity incident, Kaspersky’s experts discovered new ransomware they’ve dubbed “ShrinkLocker”. An interesting feature of this malware is that its creators artfully use the built-in capabilities of Windows to lock down computers the malware has infected. In particular, ShrinkLocker uses the standard full-disc encryption utility BitLocker to block access to the data.
What makes ShrinkLocker dangerous?
Like most ransomware today, ShrinkLocker encrypts the victim’s local drives to block access to their contents. What it essentially does is activate a standard security feature — BitLocker.
ShrinkLocker shrinks the computer’s drive partitions by 100 megabytes — hence its name — and uses the freed-up space to create a boot partition for itself. While it’s at it, it disables every BitLocker key-recovery mechanism, and sends the key that was used for the drives’ encryption to the attacker’s server.
After the user restarts the computer, they’re presented with the standard BitLocker password prompt. Since the user is now unable to start the system, ShrinkLocker changes the labels of all system drives to the attacker’s email address instead of leaving a ransom note.
How ShrinkLocker works
ShrinkLocker is implemented as a complex VBScript. It starts by gathering information about the operating system — primarily, its version. If the script finds that it’s running on Windows 2000, XP, 2003, or Vista, it shuts down. For newer editions of Windows, it runs parts of its code that are optimized for the relevant operating system.
Next, it runs preparatory operations on the local drives as mentioned above, and modifies several registry keys to configure the system for running BitLocker smoothly with the settings that the attacker requires.
Then it disables and removes all default BitLocker protectors to prevent key recovery, and enables the numerical password-protector option.
The script then generates this password and initiates encryption of all local drives using the newly created password. After this, ShrinkLocker sends an HTTP POST request containing the password and system information to the attacker’s command-and-control server.
To mask the actual server address, the threat actor uses several trycloudflare.com subdomains. This is a legitimate domain owned by CloudFlare and designed for website developers to test website traffic tunneling capabilities.
In its final stages, ShrinkLocker covers its tracks by removing its files from the drive, clearing Windows PowerShell logs, and so on. Finally, the script restarts the system.
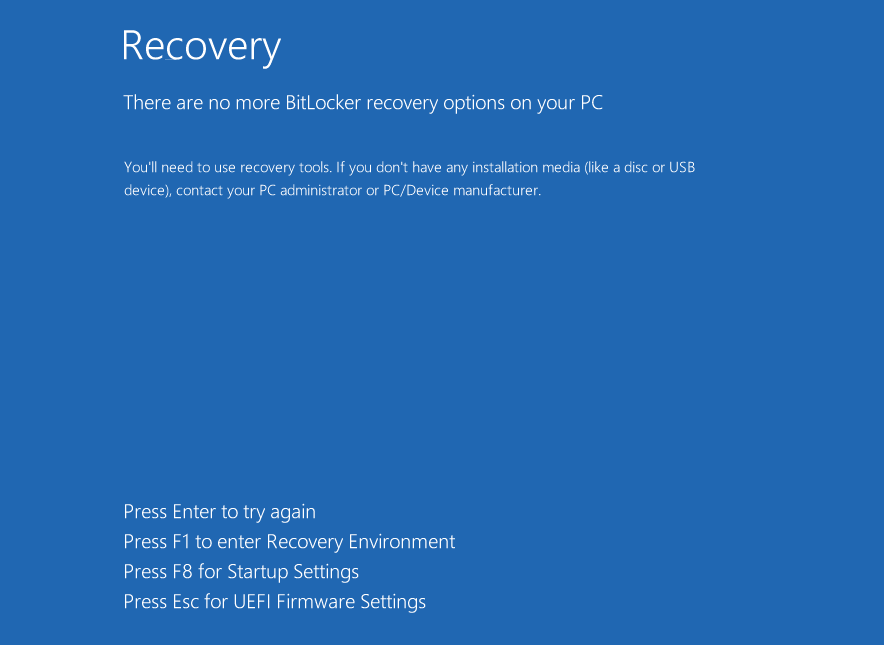
If the user tries choosing a recovery option while the machine is booting up, they get a message stating that no BitLocker recovery options are available.
Regarding the geographical distribution of infections, our researchers have observed ShrinkLocker and its modifications in Indonesia, Jordan, and Mexico. You can find more details about the ShrinkLocker modus operandi in our report on Securelist.
How to protect yourself from ShrinkLocker
Here are some tips for how to protect against ShrinkLocker and other ransomware threats:
- Apply the principle of least privilege. In particular, users should not be given permissions to modify the registry or enable full-volume encryption.
- Enable traffic monitoring. In addition to HTTP GET requests, it’s also helpful to log HTTP POST. In case of infection, requests to the attacker’s C&C server may contain passwords and keys.
- Monitor events associated with VBS and PowerShell execution. Save scripts and commands you discover to external storage, as the malware may delete your local logs.
- Back up your data regularly. Use offline storage for backups and verify their integrity.
- Use a reliable security solution on all corporate devices. For example, Kaspersky Endpoint Security for Business detects ShrinkLocker with the verdicts Trojan.VBS.SAgent.gen, Trojan-Ransom.VBS.BitLock.gen, and Trojan.Win32.Generic.
- Use EDR (Endpoint Detection and Response) solutions to monitor suspicious activity on your corporate network.
 Ransomware
Ransomware