Social engineering, sometimes called the science and art of human hacking, has become quite popular in recent years given the exponential growth of social networks, email and other forms of electronic communication. In the information security field, this term is widely used to reference an array of techniques used by criminals who obtain sensitive information or to convince targets to perform actions that could compromise their systems.
With so many security products available today, it´s the end user who has the power. Be it a set of login credentials (username and password), a credit card number or bank account, most of the time the weakest link in the chain is not technological but human and when psychological manipulation takes place it’s extremely important to know what types of tricks are being used and how to prevent them.
Social engineering is not new. It has been around since the beginning of time, with popular engineers such as Kevin Mitnick or Frank Abagnale, now renowned security consultants, we can see how the transformation from criminal to white hat guru is possible. Frank Abagnale, for example, was one of the most famous con artists, creating multiple identities, forging checks and tricking people into disclosing information he needed to carry on his scams. If you have seen the movie “Catch Me If You Can” you’ll get a picture of what a social engineer is capable of doing when he has a clear objective. Just remember, a social engineer might not only rely on technical or computer scams to get your information. You need to be wary about everyday activities that might seem suspicious. For example, your password might be revealed in a phone call. It seems unwise to tell your password to anyone. However, the perspective changes when you receive a phone call from “tech support” of your company early Sunday morning requesting you to visit the office to perform some minor technical updates on your computer. You will tell your password to the “network administrator”, moreover, you’ll say “thank you”! Or maybe you’re too cautious for that, but many of your colleagues are not.
Most cyber criminals wouldn’t spend much time trying complex technological hacks when they know it’s much easier to use social engineering for their purposes. Moreover, there are even websites that exists containing valuable information to learn about these types of techniques and why they are so successful when used to trick people. One of them is SocialEngineer.org, which provides a framework to learn the theory behind why each type of attack works and many real world examples that support the definitions and concepts mentioned previously.
We use spoken language daily to influence each other without even being aware of such actions. Language has some drawbacks when viewed from a social engineer’s point of view since it’s linked to our subjective experience. NLP or neuro-linguistic programming even though invented for therapeutic purposes is considered an evolved form of hypnosis used by many social engineers as a tool to influence and manipulate their victims in order to get them to do the actions needed to deliver a successful attack. This can include giving up their password, disclosing confidential information, disabling a security measure or pretty much anything that you can imagine in between as a stepping-stone to further develop an intrusion.
Although the link between psychology and hacking seems far stretched, the shocking reality is that online attacks are based around the same principles as their offline counterparts. The desire of every person for reciprocation (if I do you a favor you will quite likely do one for me), social proof (you believe in the judgment of the majority), authority (i.e. trusting a police officer, a doctor, a technical support guy, etc.) and many more, are universal ways to build rapport with someone and attend to our basic human needs. A social engineer knows what buttons to push to get the desired response from us by creating a context (framing) that enables an invented history to be believable. Bypassing our rational thought process is not difficult for highly skilled individuals and it only takes a fraction of a second to give them the advantage they need to get what they want.
Nevertheless, in this article we will be focusing mainly on the various techniques used by online criminals to perform their activities in order to obtain illegal information and profit from their victims. As previously mentioned, the principles used for online scams are the same as the ones presented in real life. But, because the Internet is such a massive medium for distributing information, a phishing email, for example, can be sent to millions of recipients in a brief lapse of time making this type of attack a numbers game. Even if a small number of the intended targets believe this ruse it will still reap a huge benefit for the criminal group or individual responsible for it.
Today, one of the most common methods used to obtain confidential information is known as Phishing (a contraction of the terms password harvesting fishing). Phishing can be characterized as a type of computer abuse or fraud that leverages social engineering principles with the aim of obtaining private information from the victim. The cybercriminal usually relies on email, instant messaging or SMS to deliver the phishing message which will persuade the victim to either reveal information directly or perform an action (entering a fake website, clicking on a malware download link, etc.) which will unknowingly allow the attacker to carry on their ill-intentioned plan.
We have seen an evolution in malware which goes hand in hand with social engineering. In the old days, any computer virus would be quite obvious to the user and display fancy message boxes, icons, images and pretty much anything that would give the author credit for their creation. In the present, it’s not uncommon to find malware that gains access to the victim’s system via social engineering tricks and stays hidden until it needs to execute the malicious payload. A never-ending cat and mouse game is played between criminals and security companies making education one of the fundamental defense mechanisms for every user.
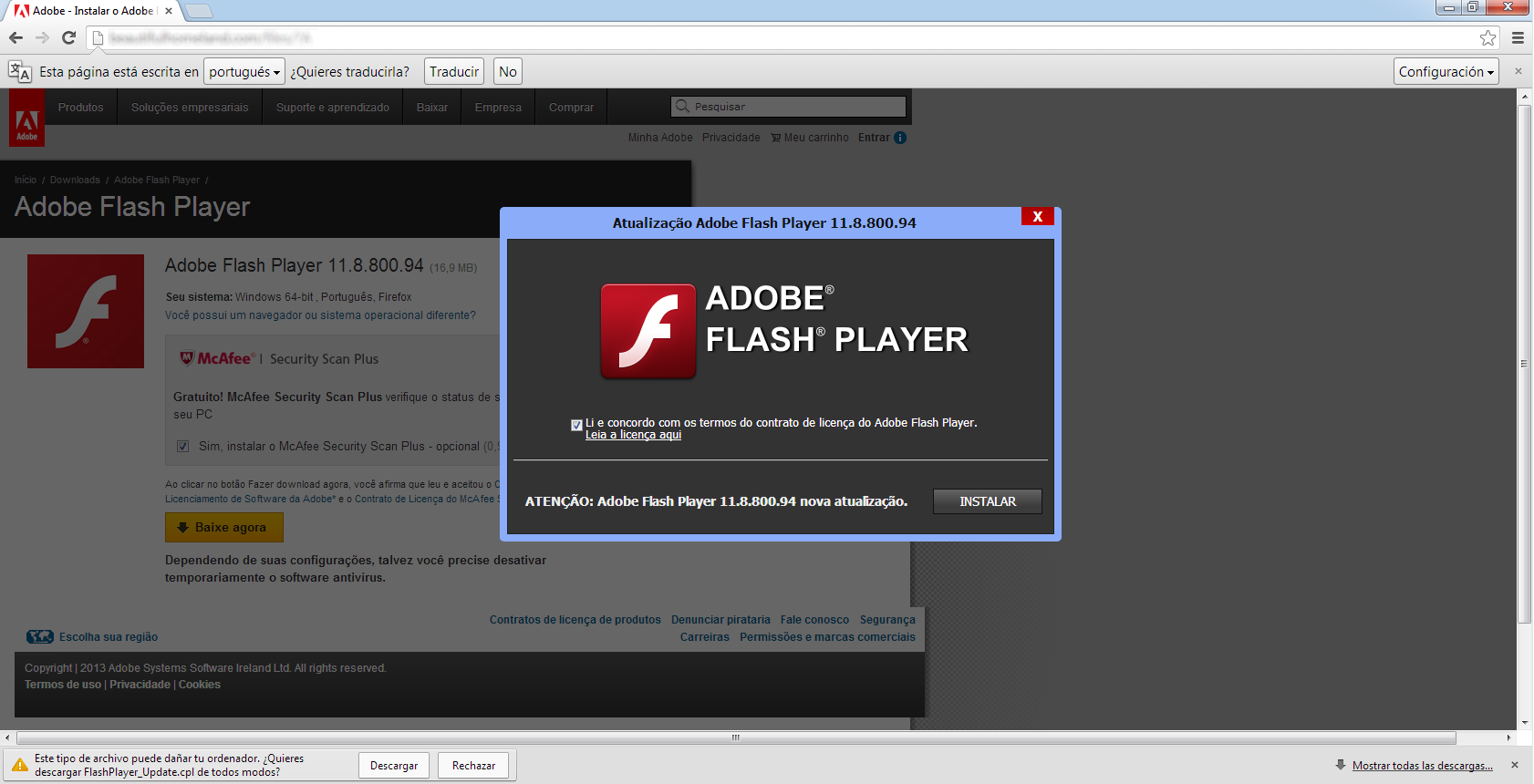
Many interesting malware samples can be found that rely on social engineering to effectively deliver their attack to the victim. Amongst the most popular we can name are fake Flash Player updates, embedded executable files in Word documents, low quality copies of legitimate browsers such as Internet Explorer and many more.
A malware distributing website that uses a fake Flash Player update to trick users into installing the software.
Most of the example attacks listed are targeted at Latin American audiences, mainly because these types of technological threats are not well known or understood in the region. Additionally, most of the computer systems in the region are running outdated software that gives cyber criminals a great business opportunity. It wasn’t until recently that some online banking security measures were strengthened but there are still many loopholes that can enable a successful social engineering attack in South America.
Other attacks are more popular in the region even if they don’t fully fall into the computer fraud category. A scam known as “virtual kidnapping” uses social engineering telemarketing tactics by claiming that a victim’s family member has been kidnapped and a ransom must been paid without further delay to guarantee their safety and freedom. By taking advantage of the victim’s sense of urgency and fear, the attacker’s demands are complied with without even knowing if there was someone kidnapped to begin with. In Latin America, where these types of crimes are common criminals have been getting a huge profit using schemes like this which exploit characteristic traits of the human behavior.
In addition, it’s important to keep in mind that whatever information you post publicly online (Facebook, Twitter, Foursquare, etc.) might give criminals a clue on how to connect the dots on where you are and your real identity. A targeted (spear-phishing) attack is not common but if you provide valuable information without a second thought you could be making the lives of cyber-criminals easier. Even an Amazon wish list could be the gateway to an epic social engineering hack.
As mentioned earlier, a complete security suite installed is mandatory nowadays if you are doing any kind of online activity (and most likely you are). Moreover, keeping up to date with the latest threats and social engineering tricks might give you the edge you need to avoid becoming a victim in these types of attacks (online or offline). Remember that all the technological gadgets and defense mechanisms mean next to nothing if you don’t know how to use them and are aware of what the bad guys are currently up to. Crime evolves, so should you.
 hacking
hacking

 Tips
Tips