It’s safe to say that almost everyone has wanted to spy on someone at least once in their life, whether to make sure your partner is faithful, your kid has not fallen in with the wrong crowd, or your employee is not being courted by competition. The technologies for spying on colleagues and families are in great demand, which is universally known to breed supply.
The supply is represented by quite an impressive range of so-called legal spyware apps (aka stalkerware or spouseware), which can be installed on your employee’s or family member’s device for a relatively modest fee. These apps stay hidden and keep their users informed about device location, browser history, SMS messages, social media chats, and more. Some of them can even make video and voice recordings.
Stalkerware — unethical but legal (almost)
From a moral standpoint, it is not good to use stalkerware: Installed without the owner’s knowledge or consent, it operates in the background and has access to very personal information. Yet such applications are not illegal in many countries, even though spying on family members is legally prosecutable. Developers try to squeeze through legal loopholes, for example, by referring to their products as parental control solutions.
It’s no wonder people continue to buy these technically legal apps, unethical though they may be. Over the past year, more than 58,000 users have detected stalkerware on their phones or tablets with the help of our products alone. Of those, 35,000 had no idea about the stalkerware installed on their devices until our protection solution completed its first scan.
Stalkerware can leak your data
Despite its legal status, stalkerware is dangerous indeed. These apps put at risk both the subject and the object of spying. How do such apps pass the collected data to the person who installed them? By uploading it to a server where the user can access it and sift through the catch. So if you decide to spy on an employee suspected of dirty play, all of their incoming and outgoing letters with every confidential document and project detail will end up on that server, including the ones written by you. If you’re keen to learn the secrets of your love interest, your wooing messages, too, will be on the record.
But what’s wrong with that, you being the only person who can view this data? The problem is, you are probably not the only one. The app developer is almost certain to have access to it, too. That’s for starters. Worse, this sensitive data may end up in the hands of malefactors or even become publicly available.
In August 2018, a researcher known as L. M. discovered a vulnerability in the Android app TheTruthSpy, which was sending login and password data without encryption. The hacker took advantage of it to get hold of photos, voice recordings, messages, and location data from 10,000 devices controlled using the spyware.
In March 2019, another researcher, Cian Heasley, discovered a whole MobiiSpy server was publicly available. It held more than 95,000 photos, including intimate ones, and more than 25,000 voice recordings. MobiiSpy’s hosting provider, Codero, responded to the incident by blocking the resource.
According to Motherboard, a total of 12 stalkerware developers have leaked data over the past two years. That means by installing such an app on someone’s device, you are almost certain to compromise both them and yourself.
Stalkerware breaches device protection
Even the stalkerware installation process is not safe. First, most of these apps fail to comply with the policies of official stores such as Google Play, so you will not find them featured. That means, in the case of an Android device, you have to consent to installing third-party apps —which, in turn, opens the door to hosts of malware.
Second, stalkerware often claims lots of system rights, even down to root access, which puts the app in full control of the gadget — in particular, giving it the right to install other apps.
Moreover, some spying apps insist that protection solutions be deactivated — or they simply get rid of them, if authorized to do so.
That is where stalkerware is different from legal parental control apps, which do not try to hide themselves on the device, or deactivate the antivirus, and they can be found in official marketplaces. That’s why parental control apps, unlike stalkerware, do not pose a threat to their users.
Protecting yourself from legal stalkerware
As you can see, it’s best to think twice before installing stalkerware on someone else’s gadgets. We also advise following these tips to make certain that nobody can plant a “gift” like that on your own device:
- Protect your gadgets with a reliable password and never disclose it to anyone, even family members.
- Block installation of third-party apps. This will protect you against both stalkerware and real malware.
- Check applications installed on your telephone at regular intervals and delete those you don’t need. That will also free up memory space and reduce paid traffic.
- Use reliable protection. Even though stalkerware is considered legal in some countries and is not identified as malware per se, many antivirus products detect it and alert users about it — they refer to it as not-a-virus, a class of threats you should not ignore.
If you use Kaspersky for Android, you no longer have to sort out threat classes and names. We don’t think it’s right to refer to stalkerware as not-a-virus without explanation, because that may not give the users a good sense of how dangerous it is. That’s why we developed our all-new Privacy Alert function, which notifies users about such issues and explains the potential dangers. Once your update is installed, here’s what you’ll see:
 privacy
privacy
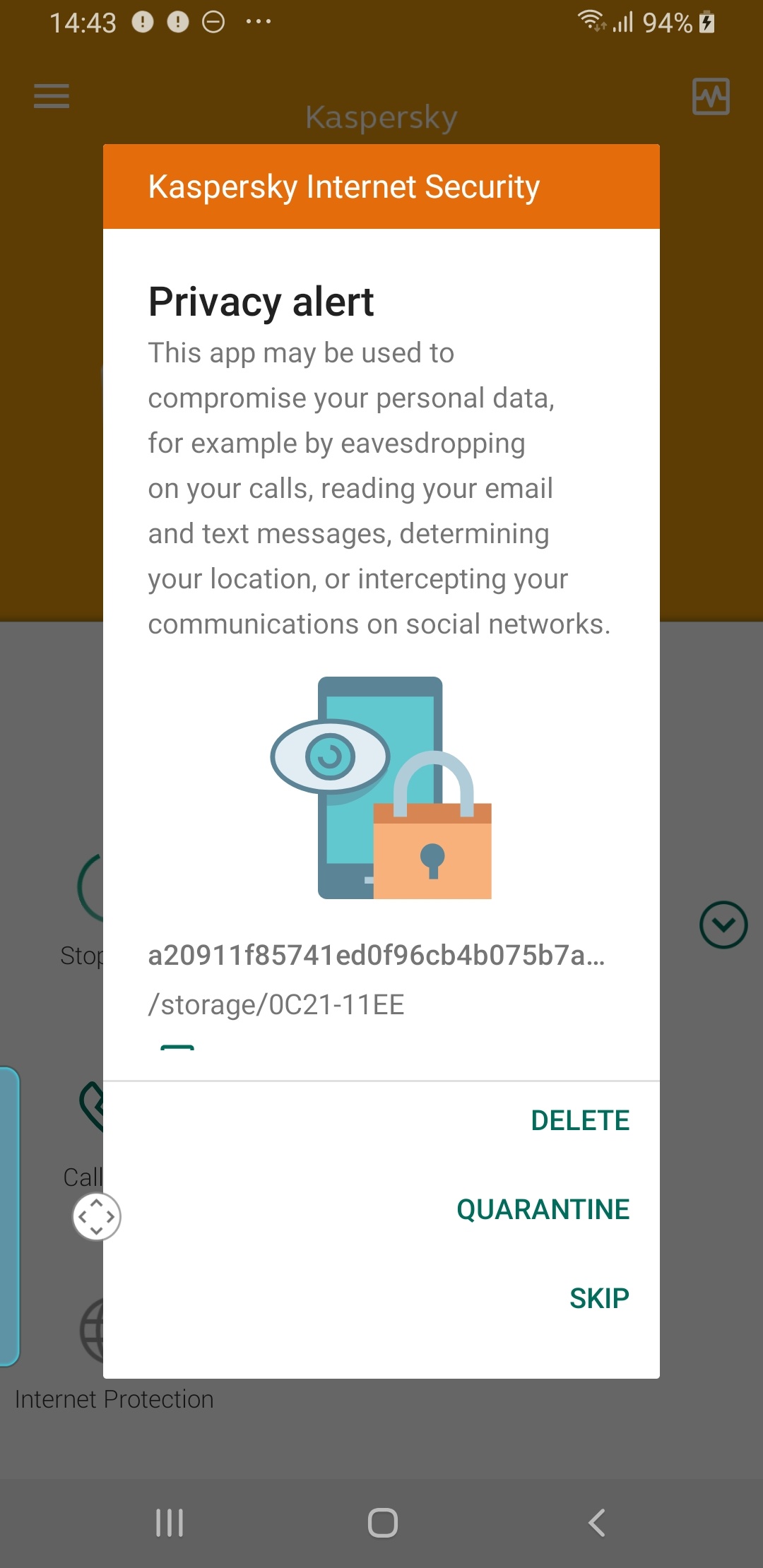

 Tips
Tips