
Android under attacks: old vulnerabilities, present threats
The late April was especially “rich” with news related to bugs, attacks and Android-targeting malware.
29 articles

The late April was especially “rich” with news related to bugs, attacks and Android-targeting malware.

We talk a bit more about how our software protects businesses and helps their IT security staff.

With all of the security improvements, criminals find and exploit various ways of circumventing them to deliver their malicious creations to end-users’ phones, which puts at risk both the device owners and the businesses they are involved with.

A New York artist made an exhibition out of making a single private and anonymous cell phone call outside the scope of government spying. Here’s how he did it:

Losing a phone is always a bit of a nuisance, especially if it’s an expensive piece of hardware. With smartphones conquering the world with authority, losing a phone means also
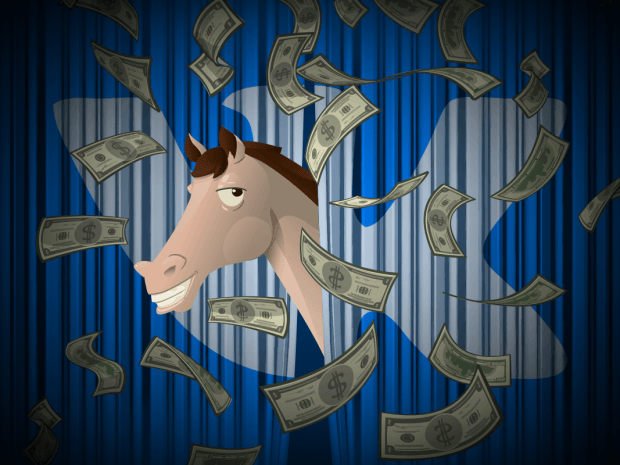
A Trojan malware called Podec uses popular Russian social network VKontakte, and other channels, to infect Android phones. Beware: It can bypass CAPTCHA.

Kaspersky Lab experts analyze the security and privacy trends that emerged in 2014, including anonymous Tor browsing, ransomware, APT attacks and more.

The Electronic Frontier Foundation recently graded a slew of mobile and Internet messaging services based on security and privacy. Here we list the low scorers.

By default, your iPhone’s OS is set to give you the best performance instead of the best battery life. But you can change that!

The Electronic Frontier Foundation recently graded a slew of mobile and Internet messaging services based on security and privacy. Here we detail the top scorers.
A number of popular Android applications are putting sensitive user data at risk of exposure because the app developers are not fully implementing encryption.

The biggest concern about Apple Pay is that one’s iCloud account now controls not only private photos, app data, and messages, but also money. You lose your password – you lose everything and as the celebrity hack showed us, there is no need to hack Apple’s servers. Social engineering, phishing, trojans – all cybercriminal tools will now be targeted at people’s electronic wallets.

Facebook fails to fully encrypt data on its Instagram mobile app, which puts user security and privacy at risk.

As ISPs push to make Wi-Fi more widely available outside the home, users are increasingly vulnerable to attacks that rely on rogue and malicious hotspots

App stores offer all the promise of a virtually unlimited range of games and tools, but are rife with pitfalls too. These include bad apps, ballooning costs, and malicious apps, particularly on Android devices.

Quick tips for internet and mobile security, and avoiding scams while booking for a safe vacation and traveling.

Windows Phones continue to grow in popularity, which means users should take precautions to make their devices as secure as possible.