
Hacking a car: a real threat or yet another shocker?
2015 proved: it’s possible to hack a connected car remotely. But is it as dangerous as it seems?
666 articles

2015 proved: it’s possible to hack a connected car remotely. But is it as dangerous as it seems?

Are you sure that one-time SMS passwords reliably protect your mobile bank? Think again! In this article we explain how Trojans fool two-factor authentication.

At the 2016 RSA conference, Kurt Baumgartner spoke on why we need to put some emphasis on security for the transportation industry.

We have previously discussed what VPN is. Now let’s review its implementations and their advantages and drawbacks.

The average American’s data has been stolen several times. Now when it’s done, what would a cybercriminal do next? We have discussed it at RSA Conference 2016.

Find out how to make sure you’re keeping your Tumblr account as secure as possible.

A look at the evolution of mobile threats in 2015 and some predictions for 2016

While many mobile applications serve as a mere distraction, these apps can help simplify or streamline your daily life.

Over the weekend, Snapchat was compromised via a phishing email pretending to be from company CEO.

Shodan and Censys are the search engines for the Internet of Things and this duo is capable of wreaking havoc in a lot of different ways

The only way to ensure the security of online payments is to be at least one step ahead of the cybercriminals, and that can be achieved only by improving the technology.

Why Steam users often fall victims to scams and frauds and how to avoid it.

Sooner or later each user of the internet will face a trick or trap. Here’s the list of the most widespread ones. Forewarned is forearmed!

At SAS 2016 Sergey Lozhkin revealed how he hacked his friend’s hospital and medical equipment.
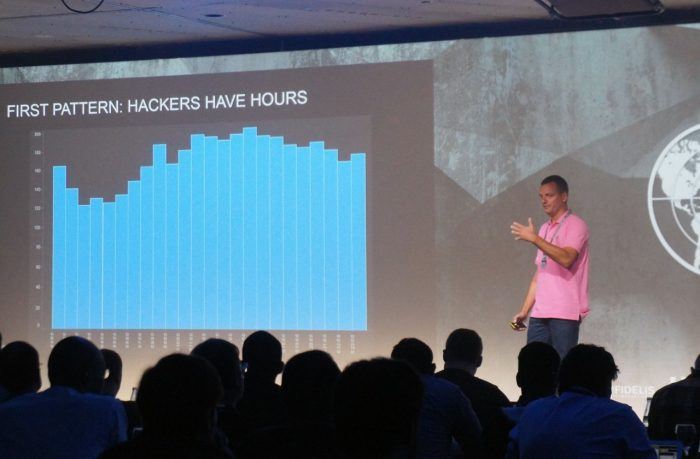
Observing cybercriminals’ behaviour one can find consistent patterns and thus find out who the criminal is in real life

Cybersecurity isn’t something that should fall exclusively with CISOs and IT pros. Rather it is something that impacts employees from the mailroom to the cushy corner office.

Kaspersky Lab’s research shows that some users are too eager to share everything they have when it comes to social networks

The rise of Snapchat has brought a whole host of security issues regarding the app. Make sure your account is secure.

What exactly is a VPN? There has been a lot of buzz around it, but why do we need it?

The Hyatt hotel chain has revealed recently that 250 of 627 of its properties worldwide were infected with money-stealing malware.