
10 best quotes from Tim Cook’s recent speech on privacy and security
Recently, Apple’s CEO Tim Cook delivered a speech on privacy and security during EPIC’s Champions of Freedom event. Here are the 10 best quotes from his speech.
669 articles

Recently, Apple’s CEO Tim Cook delivered a speech on privacy and security during EPIC’s Champions of Freedom event. Here are the 10 best quotes from his speech.

Kaspersky Lab experts detected a sly scheme that allows fraudsters to steal personal data without your login and password.

Tech journalists Chris Brook and Brian Donohue discuss Google I/O, the IRS and Carefirst BlueCross BlueShield Data Breach in this Talk Security podcast.

At Google I/O 2015, the software giant presented a slew of new features and services. We take a first look at customizable app permissions, Android Pay, Now on Tap, and others.

Technology dependence cannot be beaten, but the technologies can be laid out properly. With good system architecture and a proper security policy, the number of bottlenecks is brought to an absolute minimum.

Since the holiday season is upon us, we prepared a list of simple tips to help you minimize risks when renting a car abroad.

While LTE networks are seemingly just now starting to take off, networking vendors and carriers are already fully engaged in a vivid discussion on 5G’s perspectives. What are those next-gen networks going to be and why do we need them at all?

To hackers’ delight, merchant vessels that transfer about ninety percent of the world’s cargo heavily depend on automation and remote monitoring systems with poor IT security.

Much has been said about the VENOM vulnerability, which is part of the new-age phenomena of Virtualization.

How many research centers do you need to fight for a safer cyber world? We used to have three labs based in Moscow, Beijing, and Seattle. Now, we’re excited to announce the opening of a fourth lab — our new European Research Center based in London.

It was recently discovered that certain Hospira drug infusion pumps contain dangerous and easily exploitable security vulnerabilities.

A legendary Soviet spy, Richard Sorge, is famous for conveying the exact date of the German invasion into the Soviet Union, and for letting the command know Japan had no plans of attacking the USSR in the Far East.

Five lessons from the story of the Enigma cryptographic machine which are still relevant.

This post isn’t about smearing the good, evolving system that is Apple’s Mac OS X. The goal was to bring perception and reality together: just like the other operating systems, Mac OS X has its fair share of bugs, and while the historically smaller Mac user base has resulted in less cyber criminal targeting, it doesn’t make Mac OS X impervious. Macs’ user base has been growing steadily over the last few years, and criminal interest is following the same pattern.

During WW2 modern cryptography principles were often coupled with ‘amateur’ ciphering methods. Curiously, the latter ones often proved to be equally reliable
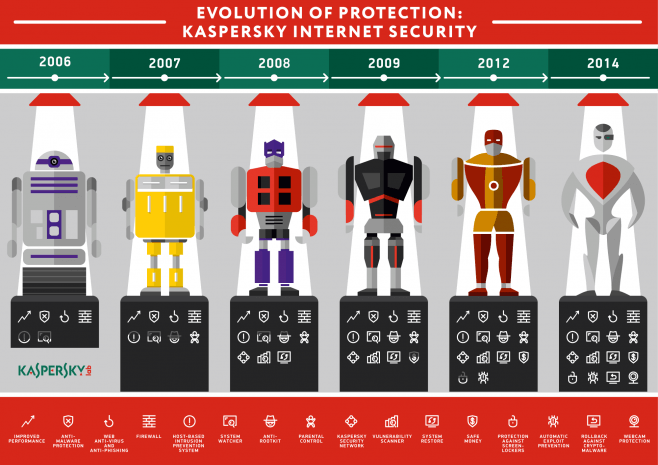
We’ve created an infographic that shows how the Kaspersky Lab flagship antivirus software has improved over the last 10 years.

New research demonstrates that it is possible to hack and hijack devices used to perform remote surgery

Yet another APT of the ‘Dukes family’ is hitting high-profile targets, including the US government office.

The story of how Israeli UAVs defend the country on the ground, in the sky, and in the information domain.

The annual RSA Conference in San Francisco, California of Internet-of-things insecurity and how no amount of money can fix computer security

Recent report by US GAO was treated by medias as “Modern aircrafts can be hacked and commandeered through onboard Wi-Fi”. Is it really that bad?