
VPN for small businesses
In recent years, small businesses have increasingly become the target of man-in-the-middle cyberattacks. Protect yourself by using a VPN.
12 articles

In recent years, small businesses have increasingly become the target of man-in-the-middle cyberattacks. Protect yourself by using a VPN.

Small businesses may not be the main target of cybercriminals, but it does not mean an SMB will not fall victim to a supply-chain attack. How not to become collateral damage.


Alex Moiseev addresses the issue of transformations that happen when a business starts working with enterprises.

For the past 20 years, Kaspersky Lab has been saving the world. This e-book shares business best practices that the company has learned over the past two decades.
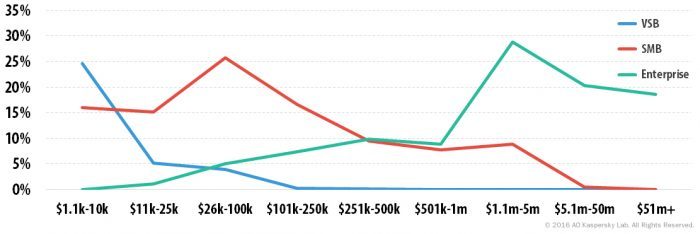
For many SMBs SaaS can provide a cost effective way to take advantage of technology through a cloud-based, subscription model.

Smart MSPs craft security software proposals for SMBs and offer security systems management services that eliminate the need for in-house information security specialists. Not every service provider is good for small companies, but the most successful MSPs are focused on this segment.

Security is a tough matter for small businesses for multiple reasons; startups and small entities tend to save on their IT wherever possible, and that’s where security failures are common.

Understanding something means getting the correct answers to questions. In this post, we have picked – and answered – three questions that need to be asked to ensure business data security.

Small businesses are unwilling to invest in security solutions – often because they don’t think there are any – designed specifically for their needs. But such solutions do exist.
Very small businesses, including private enterprises and companies with fewer than 25 people involved, are the foundation of the economic structure of the developed and of many developing countries without

It’s a sad reality that, sooner or later, most businesses will be hacked. If this happens to your business, there are two types of response to avoid. First, there’s the