
Clavis Aurea, or Does the “Golden Key” actually solve encryption issues
People encrypt their communications so strongly that governments cannot access it when there is a need. Is it really bad?
443 articles

People encrypt their communications so strongly that governments cannot access it when there is a need. Is it really bad?

Here are some simple yet effective ways to protect your files from infection by ransomware.

Kaspersky Lab has recently conducted an unusual research and proved that many users hardly care about security. Here is the reason to create reliable passwords for all of your accounts.

Cellular networks are not that hard to hack and it is almost impossible to protect them. Telcos are not ready to take responsibility and spend millions of dollars to secure their clients.

Think a photo of your boarding pass is innocent when posted online? Think again.

Since you started to connect all those Things to the Internet, creating IoT, your home is no longer your fortress by design. Now attackers can spy on your kid through a baby monitor or break into your house by fooling your ‘smart’ security lock.

Criminals can use VoLTE to cause connection failure, subdue voice calls, or strip the victim’s mobile account of money.

While FBI recommends victims to pay the ransom, Kaspersky Lab won back the access to the files for dozens of thousands of CoinVault and Bitcryptor victims.

Google’s Android OS is a vulnerable system. Developers make it worse by not providing critical patches in time.

What is the difference between real and theoretical threats?

Today’s weekly news digest covers the stories about various mistakes in coding, and how they can be used for different purposes, including earning money.

If the idea of “hacking-back” against cybercriminals who have harmed you or your company has seized you, your executive team, or your spouse as a reasonable thing to do, read
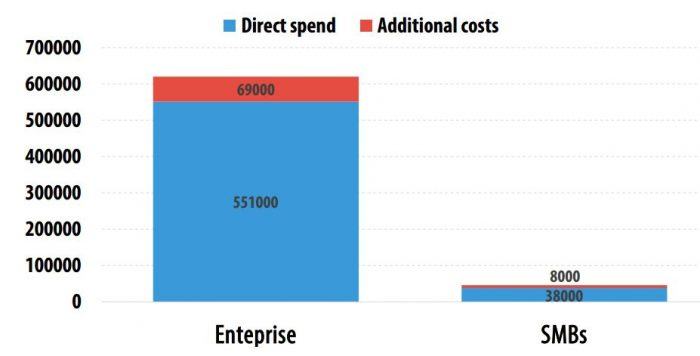
Kaspersky Lab, together with B2B International, has conducted a new survey of IT security risks.

A virus damaging hardware is one of the most widely believed myths in the infosec domain. And, at the same time, it’s the most non-standard one. And it’s not totally a myth, after all.

In the new installment of our explosive hit series “Infosec news” you’ll find: the breach of Bugzilla, Carbanak is coming back and Turla uses Level-God hard to track techniques to hide servers.

Kaspersky Lab’s researchers have found that Russian-speaking Turla APT group is exploiting satellites to mask its operation ant to hide command-and-control servers.

Information security digest: the greatest iOS theft, farewell to RC4 cipher, multiple vulnerabilities in routers

RAT stands for Remote Administration Tool. While it may sound rather innocuous, the term “RAT” is usually associated with the software used for criminal or malicious purposes.

A look at what the “threat landscape” is comprised of for businesses.
It’s not feasible to call a security solution, either for individual users or for businesses, “an antivirus.” There’s more than that.

Researchers compete at finding security holes in infotainment systems of connected cars and breaking in. The new case proves that Tesla does care a lot about security at wheel.