The problem
Any company regardless of the level of maturity possesses some valuable information which having got into the hands unscrupulous individuals can put an end not just to the financial future, but also to the whole business. Representatives of very small businesses may have quite considerable sums on their bank accounts, but they can seldom boast of their secure network of workstations. At best PC owners in the companies just install a demo version of an antivirus and a custom firewall. At worst they do not establish protection at all.
The Figure 1 below illustrates the situation when a user installs many different products by various vendors. Due to their functional protective features for any strictly defined set of threats the installed products in a LAN may not completely cover the entire set of threats, which in turn reflects the situation where an attacker despite the abundance of protective measures has an opportunity to make mischief.
Figure 1. Correlation of various threats (in red circles) with the functionality of various protective means (in green circles)
There are other downsides in installing all sorts of tools carelessly. On the one hand, the PC owner installs any product that possesses clearly defined functions (for example, antivirus protection) and forgets about it. On the other hand, the fact that the owner of the workstation forgets about the software after it has been installed can cause havoc at the most inappropriate moment. At some point the software may fail to update its database automatically, and it would require manual update, thereby, it will lead to the situation when the program becomes potentially open for hackers’ threat probing which it should protect against (See Figure 2).
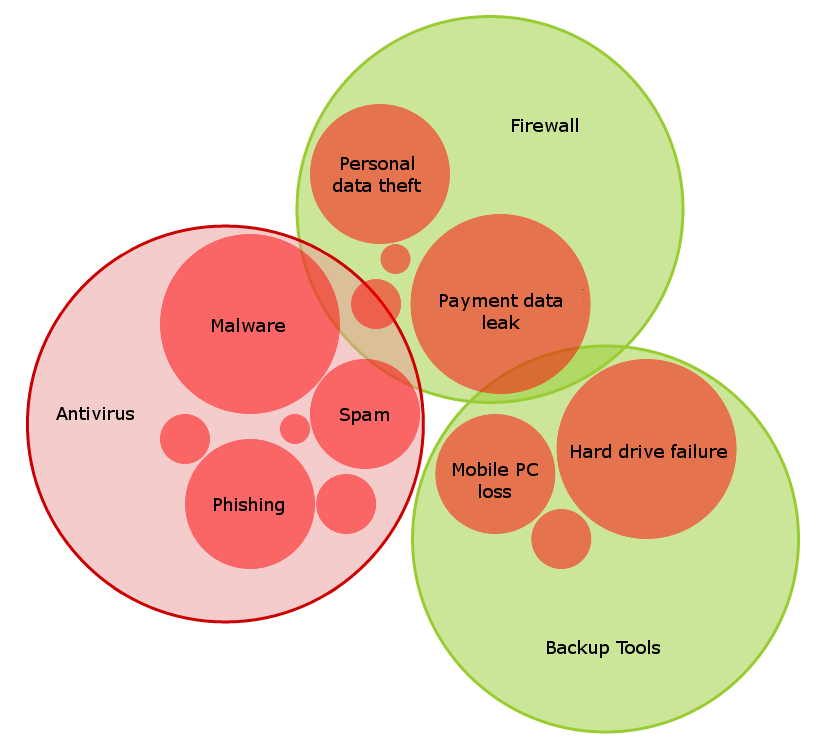
Figure 2. The software not updated in time is vulnerable
The scenario above is just a special case to illustrate the necessity to update and maintain antivirus products. But security is provided by not an antivirus only. What if, for example, there is a need to organize data encryption procedures, and at the same time to install additional protection against spam? What now, you should spend valuable time on the administration of these products?
The solution
Kaspersky Small Office Security allows you to organize the protection of basic information resources and eliminate malicious activity. For these purposes the Kaspersky Lab’s product includes an Internet Security feature in addition to virus protection, as well as protection from phishing and spam. It performs the following actions:
• monitors incoming and outgoing traffic for malicious activity;
• scans web resources for malicious codes;
• makes reputation checks of links from a cloud;
• protects against spam.
From the above functionality we can conclude that there is no need to install additional means of protection (a firewall). Moreover, KSOS Internet Security can also maintain all settings of a user’s firewall on the grounds of where a workstation currently is (within an organization’s network, a home network or at a public access point).
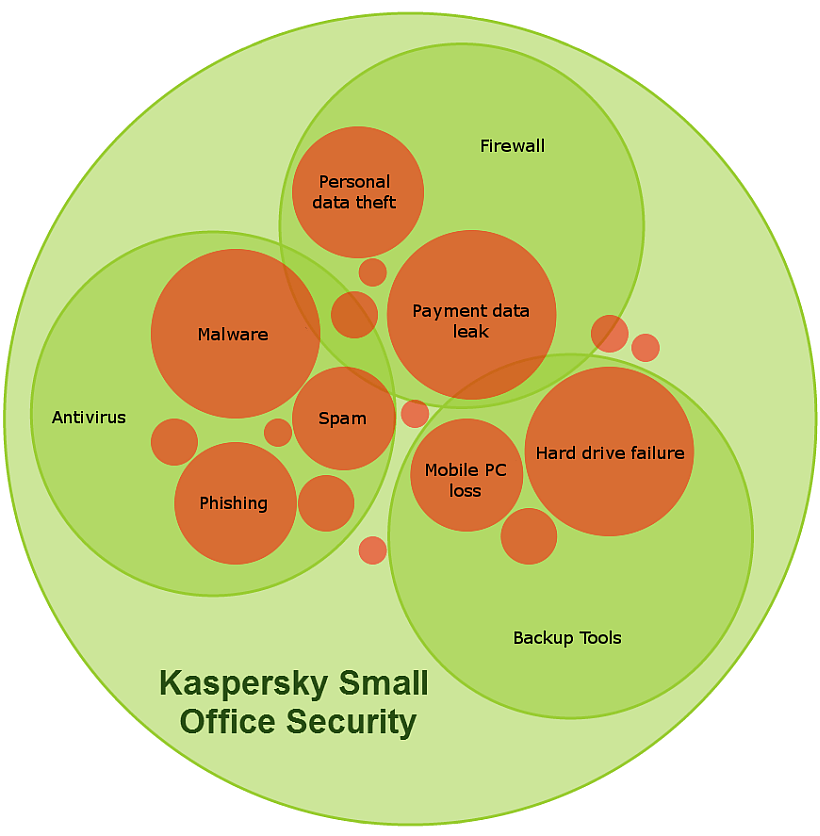
Figure 3. Correlation of various threats and KSOS functions
In addition to providing additional protection of a workstation from the activities of intruders and malware KSOS also includes:
• encryption of valuable information;
• backup and restore of important data;
• web resources access control;
• reliable means of removing files from a workstation.
Each KSOS tool is configured from the single management console that also provides detailed information of running processes on your workstation. The user gets rid of lengthy configuration procedures and the need to maintain each product separately, thereby obtaining more time for performing business tasks.
 Kaspersky Small Office Security
Kaspersky Small Office Security

 Tips
Tips