Last week Kaspersky Lab hosted a webinar to discuss the threat landscape in the era of targeted attacks. The webinar and Q&A session was moderated by UK broadcaster and technology journalist David McClelland, who was joined by Kaspersky Lab Principal Security Researcher for Kaspersky Lab’s Global Research & Analysis Team and Erik Devine, Chief Security Officer of Riverside Medical Center based right outside of Chicago, Illinois.
Attendees had the opportunities to ask questions throughout the webinar and a lively conversation was had about Heartbleed and the business implications of such a major vulnerability. Roel Schouwenberg said, “I think Heartbleed was just the tip of the iceberg.”
I think #Heartbleed was just the tip of the iceberg. @Schouw #Threattalk
Tweet
The webinar covered many topics, including the end of Windows XP, and the privacy concerns of both large and small businesses but Schouwenberg mainly focused on the current threat landscape and the major players in the cyber world. He mentioned that Hacktivists are probably the most dangerous because they are so unpredictable and they could take down an entire power planet because they don’t care about the implications.
Schouwenberg also touched upon a current topic – the Internet of Things – and how this is changing the threat landscape. Since everything is connected, we are seeing more attacks on things that we normally wouldn’t, for example, a baby monitor, a DVR, etc.
The conversation also covered the type of malware we are seeing (did you know that Kaspersky Lab identifies 320,000 new malware samples a day?), and specifically mentioned that malware targeting the Android platform is very similar to the amount of malware that targeted Windows OS in 2007 and 2008. Currently, most of the Android malware is outside of the U.S., which gives us time to prepare for that wave of attacks.
When asked about the future, Schouwenberg said that he expects there will be an increase focused on attacking virtual environments. He also said, “New technologies, more connected devices, present more opportunities for us, but also for the bad guys. With this, challenges are also presented.”
The webinar covered many topics, including the end of Windows XP, and the privacy concerns of both large and small businesses but Schouwenberg mainly focused on the current threat landscape and the major players in the cyber world. He mentioned that Hacktivists are probably the most dangerous because they are so unpredictable and they could take down an entire power planet because they don’t care about the implications.
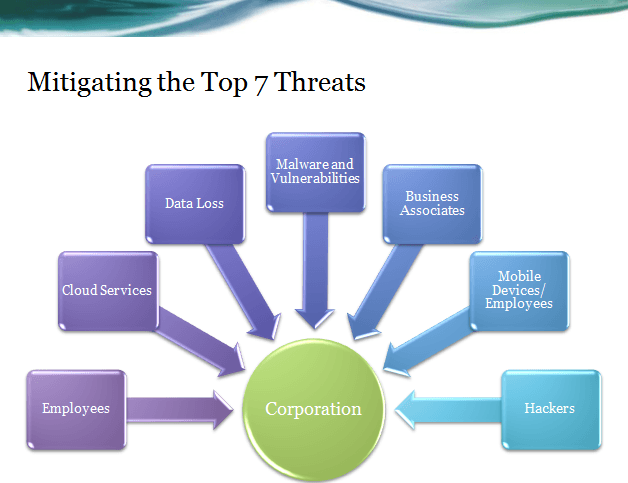
Erik Devine talked about the challenges he faces at Riverside Medical Center. He began by discussing the seven threats the he thinks present the biggest challenge to him, which include: employees, cloud services, data loss, malware and vulnerabilities, business associates, mobile devices/employees and hackers. He mentioned that while all of these present their own challenges, one of the most important to focus on is the education of his employees. He said it all starts with education and making sure his employees understand the security risks of the actions they take. They have several BYOD devices and also several advanced technologies in their hospital that are treated like security risks, and that presents an even bigger challenge.
Erik Devine talked about the challenges he faces at Riverside Medical Center. He began by discussing the seven threats the he thinks present the biggest challenge to him, which include: employees, cloud services, data loss, malware and vulnerabilities, business associates, mobile devices/employees and hackers.
However, Devine has a security mantra, which is, “Know your data, network, endpoints and users, then apply the rules!” He tries to keep his security policies and regulations simple and rely on the best technologies to keep their data secure.
Please find the full webinar here
[slideshare id=34559708&doc=threatlandscapeintheeraofdirectedattacksfinalslideshare-140512045053-phpapp02]
Does Riverside Medical use a MDM solution?
Erik Devine: Riverside uses two types of MDM solutions. Our Home Health Department uses Kaspersky MDM, which is for Android, and the Medical Center uses AirWatch, which is mainly for iOS.
Do you find the bio-medical community to be open to “security” or is it perceived as a barrier to open, accessible research?
ED: At times, the bio-medical community completely loses sight of securing their devices or software. I have devices that still use WEP on wireless so we have to create firewall rules and MAC filters to secure the device better on the network. I have noticed, though, that more and more companies have started to follow today’s higher standards to secure their devices/software better. I think the main problem is, and this is just an opinion, that the medical device and software to run that device are so expensive that companies tend to refrain from rewriting the code to secure the device and wait for the next revision to add it in. Sometimes these revisions can take five years.
Will the updates from Win32 increase the threat from Heartbleed to users through updates?
Roel Schouwenberg: To attack a client system with Heartbleed, an attacker would have to be able to redirect network traffic their way. Updates should not negatively impact users.
My older business files are in XP Professional, what type of problems will I have running XP on another program like Vista or Windows 8?
RS: That really depends on the program. Most programs should run fine on newer versions of Windows. Things generally get more complicated when there are device drivers at play, those will need updating. It’s always good to test before deploying.
Are companies likely to bring their IT Security departments back in-house in light of the millions of hack/crack attacks and Heartbleed?
RS: That’s definitely a possibility. Some companies are seeing that the money they’re saving with cloud services needs to be spent on extra security. That leads some people to the conclusion that it’s better to do everything in-house.
How do you know what emails to open if you are saying that they are using industry logos and making the email look legitimate?
RS: If an email is instructing you to go to a particular well-known site, it’s best to manually use your web browser and type in the link, or use a bookmark. Hovering over a link in an email will generally tell you the real destination of the link, rather than the one being displayed in the email.
Was the Heartbleed vulnerability really that serious? Do you expect new, similar incidents?
RS: OpenSSL is part of the internet’s critical infrastructure. Any vulnerability that can disclose passwords, personally identifiable information, or other types of sensitive information without interaction is a serious one. Researchers are now taking a closer look at this area, as evidenced by the confirmed information disclosure vulnerability in OpenSSH this week.
 targeted attacks
targeted attacks

 Tips
Tips