At the 37th Chaos Communication Congress (37C3) held right now in Hamburg, our experts from the Kaspersky Global Research and Analysis Team (GReAT) Boris Larin, Leonid Bezvershenko and Grigoriy Kucherin gave a talk called “Operation Triangulation: what you get when attack iPhones of researchers”. They described the chain of the attack in detail and talked about all of the vulnerabilities involved in it. Among other things, they for the first time presented exploitation details of the CVE-2023-38606 hardware vulnerability.
We will not repeat all the nuts and bolts of this report — you can find technical details in a post on the Securelist blog or you can listen the recording of the talk on the conference’s official website. Here we will briefly describe the main points.
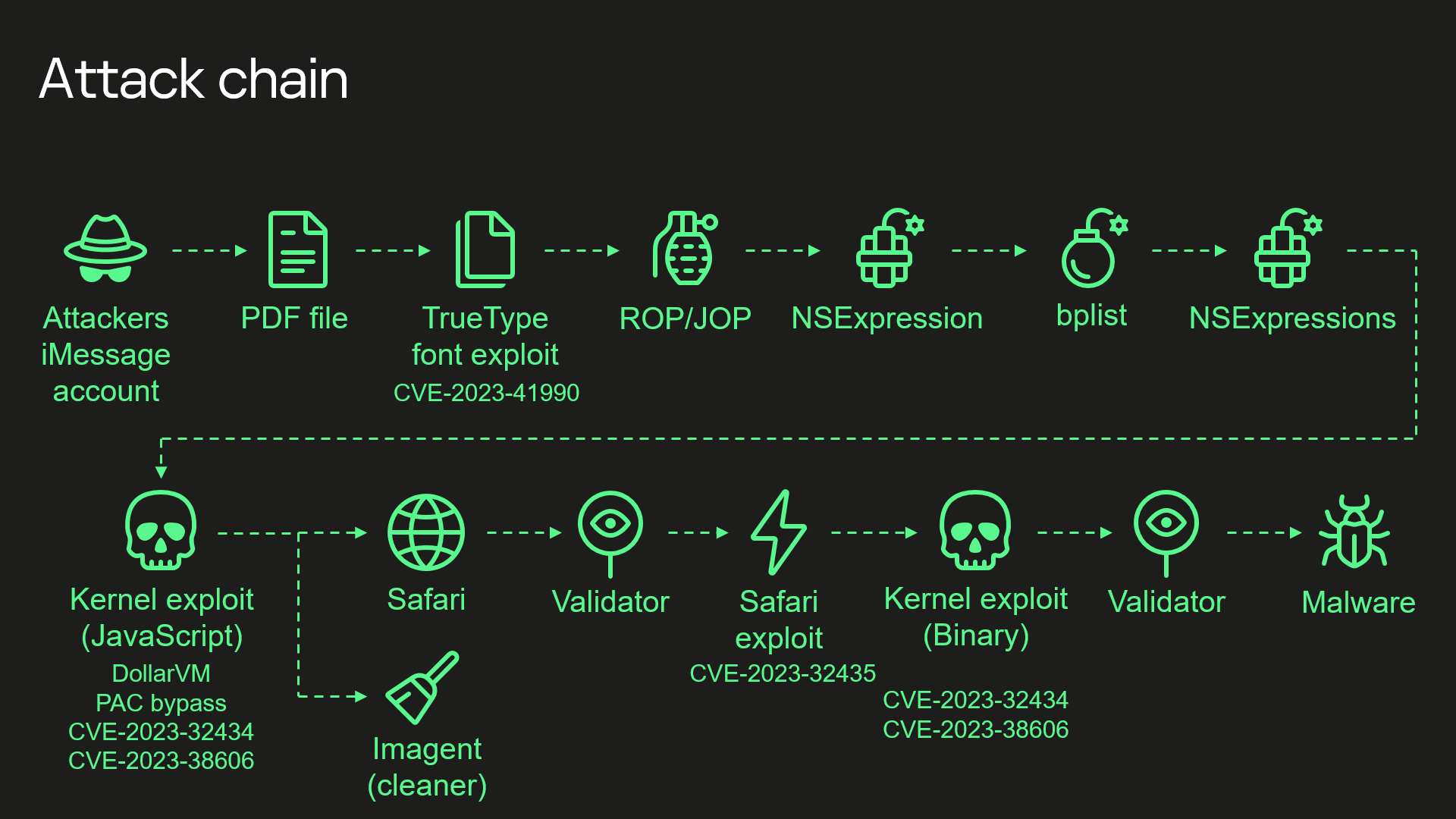
- As we already have written in the beginning of this summer, the attack started with an invisible iMessage, which contained a malicious attachment that was processed without the user’s knowledge. This attack did not require any actions from the user at all.
- Our experts were able to detect the attack by monitoring a corporate Wi-Fi network using our own SIEM system Kaspersky Unified Monitoring and Analysis Platform (KUMA).
- The attack employed four zero-day vulnerabilities that affected all iOS devices up to version 16.2: CVE-2023-32434, CVE-2023-32435, CVE-2023-41990 and the aforementioned CVE-2023-38606.
- The obfuscated Triangulation exploit could work both on modern versions of the iPhone and on fairly old models. And if attacking newer iPhones it could bypass Pointer Authentication Code (PAC).
- The CVE-2023-32434 vulnerability used by this exploit, allowed attackers access to the entire physical memory of the device at the user level, both for reading and writing.
- Thanks to the exploitation of all four vulnerabilities, the malware could gain full control over the device and run any malware needed, but instead it launched the IMAgent process and used it to remove all traces of the attack from the device. It also launched the Safari process in the background and redirected it to the attacker’s web page with exploit for Safari.
- This Safari exploit got root rights and launched further stages of attacks (which we already talked about them in our previous publications).
- Vulnerability CVE-2023-38606 allowed bypassing of the built-in memory protection mechanism using undocumented and unused in the firmware processor registers. According to our experts, this hardware function probably was created for debugging or testing purposes, and then for some reason remained enabled.
The only remaining mystery — how exactly did the attackers knew how to use this undocumented function and where did they find information about it at all.
 iOS
iOS

 Tips
Tips