Scammers often pose as well-known companies: video streaming services, job hunting websites, internet stores and so on. This time, phishers are targeting customers of Wells Fargo, one of the four largest US banks, providing services in more than 40 countries. Counting on the bank’s trustworthiness, the cybercriminals don’t limit themselves to stealing bank card details, but go after e-mail accounts and selfies of users holding their ID documents, too.
Phishing attack on Wells Fargo customers
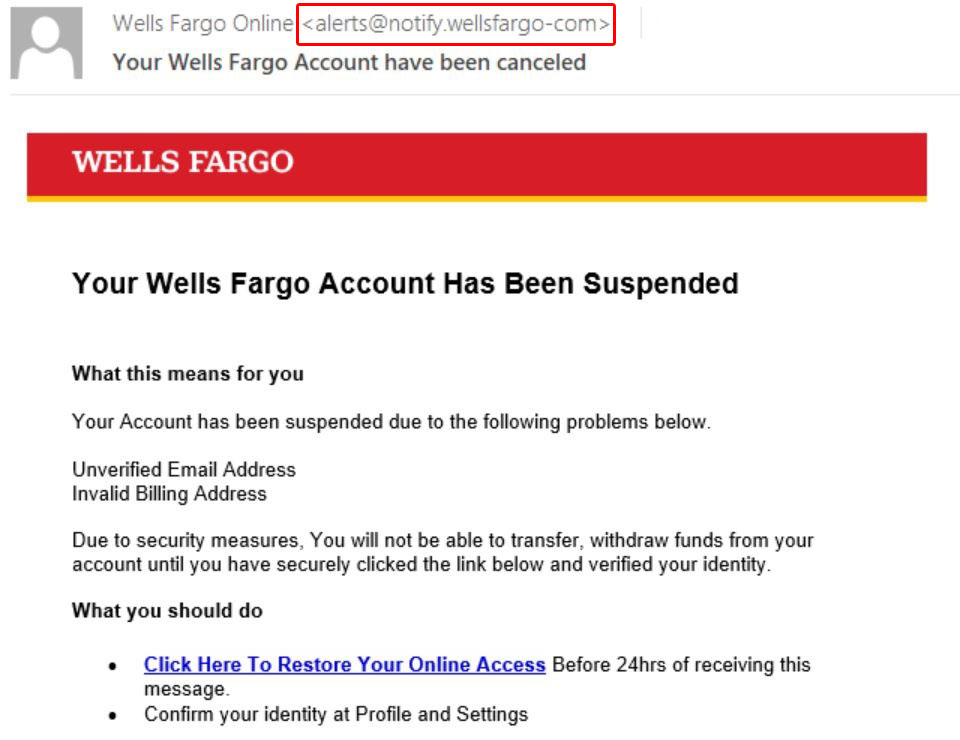
As ever, an attack starts with a phishing e-mail designed to alarm the recipient. It informs the user that their Wells Fargo bank account has been blocked, allegedly due to an unverified e-mail address or a mistake in their home address. To regain access, the message asks the recipient to follow the link and verify their identity within 24 hours of receiving the notification. Otherwise, it will no longer be possible to transfer or withdraw money, the letter warns.
The e-mail looks quite convincing: a neat logo element, business-style text, and almost no errors. Even the sender’s name and address are very similar to those of the bank’s customer service. However, the address does have a very unusual domain in the non-existent zone wellsfargo-com (instead of the usual .com). But it takes a sharp eye to spot it.
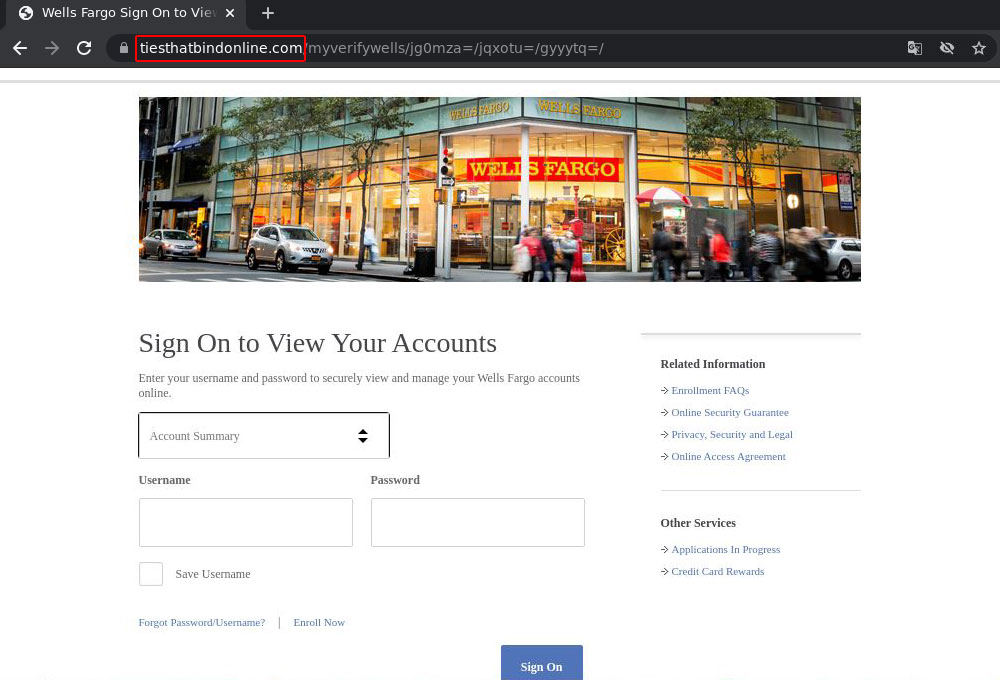
The link in the e-mail points to a third-party site, and from there, via a redirect, to a fake Wells Fargo account login page. Here the phishers made less of an effort: the design does not match that of the official page, and the URL has nothing to do with the bank at all, but for some reason references either the Bruce Springsteen song The Ties That Bind or the TV series of the same name!
On the very first page, the victim is prompted to enter their Wells Fargo account username and password. But that’s only the beginning — two more “verification” stages lie ahead.
Having signed in, the victim lands on the next page — where there are a lot more fields to fill out. Here the scammers brazenly ask for an e-mail address with password (!), a phone number with postal address, the user’s date of birth and social security number (SSN); and, of course, payment details: aside from a bank card number and expiration date, they also ask to fill in the CVV code on the back, plus PIN.
Next comes the most interesting bit: the user is prompted to upload a selfie in which they’re holding up an ID document. This page displays no fewer than three Wells Fargo logos, probably to add credibility. However, some typos somewhat spoil the impression.
[wells-fargo-phishing-screen-4.png]
[Alt/title/caption:
Having extracted all vital data from the victim, the scammers report that the account has been successfully restored and redirect said victim to the real Wells Fargo website. This maneuver is designed to make them believe they have been on the legitimate resource all the time.
What the stolen data can be used for
Typically, this kind of phishing is used to build up a massive database for subsequent sale on the dark web. The merchandise is valuable: armed with such a treasure trove of personal data, criminals can siphon off money from the victim’s card. But it doesn’t stop there: with a dataset like this they can also enrich themselves in other ways at the victim’s expense — for example, by opening a bank or crypto exchange account to launder stolen funds, obtain a credit card, and so on. With an ID-card selfie and SSN, attackers have every chance of passing the KYC (Know Your Customer) security check required for such transactions.
As such, after entering the data, probably nothing will happen at first; only later will trouble arise. This may pose an additional danger: by the time the cybercriminals start using the stolen data, the user may no longer remember having entered their personal data somewhere, making it much harder for them to give bank representatives or police officers a proper explanation.
How to avoid falling victim to bank phishing
Here are some tips on how to avoid becoming a victim of phishing schemes that involve bank accounts.
- Look carefully at unexpected e-mails about account suspensions, suspicious charges, odd purchases or generous giveaways: they are nearly always fake. We’ve explained recently why such e-mails are most likely a scam and how to spot fraud.
- Do not follow links in e-mails to bank websites. It’s better to enter the URL of the official site manually, or find it on Google, Bing or another reliable search engine.
- Remember that, as a rule, full personal information plus a selfie with an ID document are not required to recover a bank account. And you certainly don’t have to enter the CVV code from the back of your card, let alone your PIN! If you are asked for this, be very wary and contact the bank for confirmation by calling the phone number printed on your card.
- If you are a Wells Fargo customer and get a phishing e-mail, report it to your bank immediately so they can take measures to protect other users. See here for contact details.
- Install a reliable security solution that warns you about scams and phishing attempts and keeps your valuable data safe from cybercriminals.
 phishing
phishing